Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
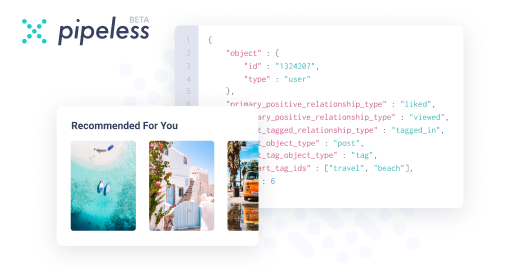
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "key store"
-
Client comes to me after a year to publish an update to his app.
I accept, start looking for my release key.... Found it.
Fuuuuuuucccck what's the password? I can't remember
Googled what to do if forgot password of keystore: Nope can't do shit other than brute Force. You've to forget your app and publish as a new app. Nice.
I must have written it somewhere... I'm sure. Check my password manager: Nope.
Start brute forcing:
Default pass: android. Nope
Name of app? Nope
After 10 mins of brute forcing:
Why would I not store the password in my password manager? The only reason I can think is the password is too stupid to be stored.
Try "password". App signed successfully.
I'm ashamed of 1 year older me xD6 -
My first AI program in the 1985 on Apple IIe (64kb ram computer) was answering simple questions with yes and no. Everyone were shocked with precision of about 100% when I was typing and 70-80% when others were typing. My parents were scared and skeptical. How it works? Store the time between the first key pressure and the following, when it is larger than 1 second the answer is yes, otherwise no. They say the question, you know the answer and type accordingly. When they want to write the question themselves, you try to force their typing speed if possible. I was 12 years old and it was very funny.3
-
My first Windows rant.
I use Spotify heavily. (After all, I am paying for it every fucking month.) In fact, it's safe to say I use it upwards of 12+ hours a day.
My birthday was a few weeks ago. I got a new mechanical keyboard using some money i received as a gift. This keyboard has a function key to launch your media player. Odd function in my opinion. But I figured I would try it out for a week or so.
My problem is: the default media center is that god forsaken piece of shit groove music (not only is it shit, I also have 0 mp3 files on my computer).
No problem, I'll just change the default media center. Fucking Windows doesn't let me change it to Spotify. Odd. Well, I did download it from Spotify's website. Let's try downloading it from the Windows store.
I download Spotify from the Windows store. It still cannot be set to the default media center.
For fuck sake, if Google can let me set Spotify as my default over their shitty YouTube Music that I know damn well they're trying to make as the default for all Android, then you can let me change it Windows.
Yes, I know Spotfiy isn't exactly a media center, but it's basically the same fucking thing.16 -
The solution for this one isn't nearly as amusing as the journey.
I was working for one of the largest retailers in NA as an architect. Said retailer had over a thousand big box stores, IT maintenance budget of $200M/year. The kind of place that just reeks of waste and mismanagement at every level.
They had installed a system to distribute training and instructional videos to every store, as well as recorded daily broadcasts to all store employees as a way of reducing management time spend with employees in the morning. This system had cost a cool 400M USD, not including labor and upgrades for round 1. Round 2 was another 100M to add a storage buffer to each store because they'd failed to account for the fact that their internet connections at the store and the outbound pipe from the DC wasn't capable of running the public facing e-commerce and streaming all the video data to every store in realtime. Typical massive enterprise clusterfuck.
Then security gets involved. Each device at stores had a different address on a private megawan. The stores didn't generally phone home, home phoned them as an access control measure; stores calling the DC was verboten. This presented an obvious problem for the video system because it needed to pull updates.
The brilliant Infosys resources had a bright idea to solve this problem:
- Treat each device IP as an access key for that device (avg 15 per store per store).
- Verify the request ip, then issue a redirect with ANOTHER ip unique to that device that the firewall would ingress only to the video subnet
- Do it all with the F5
A few months later, the networking team comes back and announces that after months of work and 10s of people years they can't implement the solution because iRules have a size limit and they would need more than 60,000 lines or 15,000 rules to implement it. Sad trombones all around.
Then, a wild DBA appears, steps up to the plate and says he can solve the problem with the power of ORACLE! Few months later he comes back with some absolutely batshit solution that stored the individual octets of an IPV4, multiple nested queries to the same table to emulate subnet masking through some temp table spanning voodoo. Time to complete: 2-4 minutes per request. He too eventually gives up the fight, sort of, in that backhanded way DBAs tend to do everything. I wish I would have paid more attention to that abortion because the rationale and its mechanics were just staggeringly rube goldberg and should have been documented for posterity.
So I catch wind of this sitting in a CAB meeting. I hear them talking about how there's "no way to solve this problem, it's too complex, we're going to need a lot more databases to handle this." I tune in and gather all it really needs to do, since the ingress firewall is handling the origin IP checks, is convert the request IP to video ingress IP, 302 and call it a day.
While they're all grandstanding and pontificating, I fire up visual studio and:
- write a method that encodes the incoming request IP into a single uint32
- write an http module that keeps an in-memory dictionary of uint32,string for the request, response, converts the request ip and 302s the call with blackhole support
- convert all the mappings in the spreadsheet attached to the meetings into a csv, dump to disk
- write a wpf application to allow for easily managing the IP database in the short term
- deploy the solution one of our stage boxes
- add a TODO to eventually move this to a database
All this took about 5 minutes. I interrupt their conversation to ask them to retarget their test to the port I exposed on the stage box. Then watch them stare in stunned silence as the crow grows cold.
According to a friend who still works there, that code is still running in production on a single node to this day. And still running on the same static file database.
#TheValueOfEngineers2 -
Today I learned the hard way that losing your app's key store means no more updating , bug fixing , performance boosting , features adding ...
The app had like 5k downloads on the play store ..
Lost the key when one of my hard drives burned ..
Lesson of the day : keep your keys safe .
*trying to stay strong*3 -
Im back to anyone that may cared a little, so I was offline for 6 days since my ISP Ultra Hilarious to crash my state records of their paying customers and some other stuff that It took 5ever to get back, anything you guys want to share with me that may happen lately here on DevRant? I personally my classic Amazon bashing news and Perhaps giving away some Steam Keys that one Reviewer user of my site give us out to promote the site along side the devs.
For the Amazon News there is:
Amazon in talks to buy cybersecurity startup Sqrrl and also group of New Jersey Amazon Warehouse workers stood in the cold outside an Amazon Books store in Manhattan on Wednesday to remind shoppers that their online purchases are made possible by warehouse employees who often are underpaid and denied normal workplace benefits. More info at: https://legionfront.me/pages/news
No about Free Steam gamuz:
Gravity Island Key: AACA7-CYFVW-N775L
For more free keys drop by:
https://legionfront.me/pages/gaming
https://legionfront.me/ccgr 6
6 -
So I Bought this bio metric pad lock for my daughter. She excitedly tried to set it up without following the directions( they actually have good directions on line) first thing you do is set the "master print" she buggered that up setting her print. So when I got home I was thinking, no problem I'll just do a reset and then we cant start again.
NOPE !!! you only have one chance to set the master print! after that if you want to reset the thing you need to use the master print along with a physical key that comes with it.
What sort if Moron designs hardware / software that is unable to be reset. Imagine how much fun it would be if once you set your router admin password it was permanent unless you can long back in to change it. Yea nobody has ever forgotten a password.
Well they are about to learn a valuable financial lesson about how user friendly design will influence your bottom line. people (me) will just return the lock to the store where they bought it, and it will have to be shipped back to the factory and will be very expensive for them paying for all of the shipping to and from and resetting and repackaging of the locks and finally shipping again to another store. Meanwhile I'll keep getting new locks until at no cost until she gets it right.
poor design 34
34 -
At an auto parts store and was taking a look at the UI.
I FOUND A DINOSAUR!
More realistically I saw F20 as a shortcut key. How I know it wasn’t a typo? There was also F16. Wow. Even their keyboard stop at F12.
Talk about legacy program.2 -
Want to make someone's life a misery? Here's how.
Don't base your tech stack on any prior knowledge or what's relevant to the problem.
Instead design it around all the latest trends and badges you want to put on your resume because they're frequent key words on job postings.
Once your data goes in, you'll never get it out again. At best you'll be teased with little crumbs of data but never the whole.
I know, here's a genius idea, instead of putting data into a normal data base then using a cache, lets put it all into the cache and by the way it's a volatile cache.
Here's an idea. For something as simple as a single log lets make it use a queue that goes into a queue that goes into another queue that goes into another queue all of which are black boxes. No rhyme of reason, queues are all the rage.
Have you tried: Lets use a new fangled tangle, trust me it's safe, INSERT BIG NAME HERE uses it.
Finally it all gets flushed down into this subterranean cunt of a sewerage system and good luck getting it all out again. It's like hell except it's all shitty instead of all fiery.
All I want is to export one table, a simple log table with a few GB to CSV or heck whatever generic format it supports, that's it.
So I run the export table to file command and off it goes only less than a minute later for timeout commands to start piling up until it aborts. WTF. So then I set the most obvious timeout setting in the client, no change, then another timeout setting on the client, no change, then i try to put it in the client configuration file, no change, then I set the timeout on the export query, no change, then finally I bump the timeouts in the server config, no change, then I find someone has downloaded it from both tucows and apt, but they're using the tucows version so its real config is in /dev/database.xml (don't even ask). I increase that from seconds to a minute, it's still timing out after a minute.
In the end I have to make my own and this involves working out how to parse non-standard binary formatted data structures. It's the umpteenth time I have had to do this.
These aren't some no name solutions and it really terrifies me. All this is doing is taking some access logs, store them in one place then index by timestamp. These things are all meant to be blazing fast but grep is often faster. How the hell is such a trivial thing turned into a series of one nightmare after another? Things that should take a few minutes take days of screwing around. I don't have access logs any more because I can't access them anymore.
The terror of this isn't that it's so awful, it's that all the little kiddies doing all this jazz for the first time and using all these shit wipe buzzword driven approaches have no fucking clue it's not meant to be this difficult. I'm replacing entire tens of thousands to million line enterprise systems with a few hundred lines of code that's faster, more reliable and better in virtually every measurable way time and time again.
This is constant. It's not one offender, it's not one project, it's not one company, it's not one developer, it's the industry standard. It's all over open source software and all over dev shops. Everything is exponentially becoming more bloated and difficult than it needs to be. I'm seeing people pull up a hundred cloud instances for things that'll be happy at home with a few minutes to a week's optimisation efforts. Queries that are N*N and only take a few minutes to turn to LOG(N) but instead people renting out a fucking off huge ass SQL cluster instead that not only costs gobs of money but takes a ton of time maintaining and configuring which isn't going to be done right either.
I think most people are bullshitting when they say they have impostor syndrome but when the trend in technology is to make every fucking little trivial thing a thousand times more complex than it has to be I can see how they'd feel that way. There's so bloody much you need to do that you don't need to do these days that you either can't get anything done right or the smallest thing takes an age.
I have no idea why some people put up with some of these appliances. If you bought a dish washer that made washing dishes even harder than it was before you'd return it to the store.
Every time I see the terms enterprise, fast, big data, scalable, cloud or anything of the like I bang my head on the table. One of these days I'm going to lose my fucking tits.10 -
I grew up on a farm in western KS. My parents bought PCs when I was in grade school. First was a trs80 , then an Epson Equity 1+, where I built a spare key for it, and built levels in willy for my brother to beat. Then a 486 and pentium which I broke often. I ended up working at the same store in college for extra cash. While I'm an adverage developer, I do on and make decent $$. I still help them out with keeping their PCs running, for moms sewing, and dads Linux box. I figure I owe them for their investment in me. They gave me the tools to figure out what I want to do with my career and my life.2
-
Working with atlassian products....
Possibility 1
You can either use exactly this one way and only with these specific instructions ...
Which will certainly not work for the project you have.
Possibility 2
There is an feature request which gets ignored for years, someone made a plugin...
But plugin was removed as inactive. :-)
Possibility 3
Atlassian provided in their endless graciousness a plugin.
After hours of deciphering Kotlin / Java code as the documentation is either useless or lacking details...
You did it. You got the REST shit working.
Well.
You just needed a script which wraps the underlying command, parses the commands well defined format like XML with specification.... To a completely gobbled up JSON, that looks like undecipherable shit.
I really hate Atlassian.
https://bitbucket.org/atlassian/...
I just wanted to add code coverage via the REST API by the way.
A really unnecessary and seldomly used future as it seems.
And yeah... The JSON contains a coverage element which contains a semicolon separated key value store, value being a comma separated list of line numbers.... 4
4 -
So......... there's this company who HATE to return data in json, yml or xml. Their "RESTFul api" returns .ini file as string and all requests are 200 ! even though it is failed , still return 200.
And the structure are inconsistent af.
The PIC literally solve every issue by store data in .ini file locally
LocalStorage? .ini
SharedPreferences? .ini
Api response type ? .ini
Caching? .ini
UI key=value handling? .ini
hotel? trivago.6 -
XCode you fucking piece of shit...
So I just wanted to process my ios app to the app store and start the archive process. All of the sudden:
Command CodeSign failed with a nonzero exit code
What? So there is an error and you cannot tell me the error code? All information you give me that it isn't zero!? Wow... Amazing... What a great user experience. Maybe it cannot resolve the error? Maybe it is some external tool Apple has no access to and that is the only valid error they can throw at us?
Oh hell no! It has something to do with the keychain access! But why tell the user? That wouldn't be as much fun as just tell it is a nonzero error, isn't it apple?!
In the end locking and unlocking my key chain solved the problem... Thanks for nothing XCode!2 -
Dear theme designers, unless you are designing an app specifically with OLED in mind... Do not use black as a main background colour.
It just looks horrible IMO, key example on good dark theme is the windows store and a example of horrible dark theming is the settings app.
And mini rant over.2 -
There's very little good use cases for mongo, change my mind.
Prototyping maybe? Rails can prototype, create/update/destroy db schemas really quickly anyways.
If you're doing a web app, there's tons of libs that let you have a store in your app, even a fake mongo on the browser.
Are the reads fast? When I need that, use with redis.
Can it be an actual replacement for an app's db? No. Safety mechanisms that relational dbs have are pretty much must haves for a production level app.
Data type checks, null checks, foreign key checks, query checks.
All this robustness, this safety is something critical to maintain the data of an app sane.
Screw ups in the app layer affecting the data are a lot less visible and don't get noticed immediately (things like this can happen with relational dbs but are a lot less likely)
Let's not even get into mutating structures. Once you pick a structure with mongo, you're pretty much set.
Redoing a structure is manual, and you better have checks afterwards.
But at the same time, this is kind of a pro for mongo, since if there's variable data, as in some fields that are not always present, you don't need to create column for them, they just go into the data.
But you can have json columns in postgres too!
Is it easier to migrate than relational dbs? yes, but docker makes everything easy also.11 -
# NEED SUGGESTIONS
I am working on a secure end to end encrypted note taking web application. I am the sole developer and working on weekends and will make it open source.
The contents you save will be end to end encrypted, and server won't save the key, so even I can't read or NSA or CIA.
So I wanted to know if the idea is good? There are lot of traditional note sharing apps like Google Keep and Evernote. But they store your stuff in plaintext. So as a user will u switch to this secure solution?14 -
I just got my third 128GB MicroSD card off Amazon, this time SanDisk. Yet again, trying to do anything not involving the OEM full-disk exFAT partition staying intact (which, fuck that, all that uses that is Windows and Linux, i'm looking for splitting this thicc bih up) shifts EVERYTHING, including MBR+PT/GPT down the disk by 16MB exactly inserting data from... the atmosphere? whatever's using it? ...do SD cards have that secure key/DRM store space thing still?
(EDIT: I do verify that they ARE genuinely the right size after purchasing before reformatting or repartitioning, by the way.)
First it was a Silicon Power card, then a Samsung card, now a SanDisk.
(Also, why all S?)
Luckily, this time it wasn't a pain in the ass to get it to read as anything but "Bad Card" or a 0-byte/empty/non-existent device in Windows/Linux (respectively) so I was able to see that it was indeed the same issue without taking 3 days to jump through device hoops to finally get it to do it again but in such a way that it shifts out and back in all zeroes.2 -
I had a booth at a small event to represent my business. I had prepared a web-based game for people to play to win a prize. I had it running on a PC mirrored on a TV so I could do my work on my Mac separately between visitors.
During a speaker’s presentation, someone bored with it came up to my booth and I introduced her to the game. She started playing it but the sound was up too loud and drew attention to her. I quickly used volume key on the top row, but nothing happened. So I thought the fn key needed to be pressed and held to change the volume. Nope. Then I thought I’ll just use the volume control in the dock. But the browser was full screen, and when I tried to quickly change that, some other unknown thing happened and some other stupid MS configuration screen filled the screen. She gave up trying to play at that point and I felt super stupid.
When did it become so hard to use Windows machines and software? I’ve been on a Mac for about 8 years now and using this Windows laptop just feels ridiculous to me. Like some broken toy that came from a bargain bin at a dollar store. The whole thing feels cheap and like it’ll break in half if I twist it accidentally. Other Windows laptops I look at in the stores occasionally just don’t measure up in build quality. Like the companies know you’ll get max 2 years useful life and throw it away.6 -
So just now I had to focus on a VM running in virt-manager.. common stuff, yeah. It uses a click of le mouse button to focus in, and Ctrl-Alt-L to release focus. Once focused, the VM is all there is. So focus, unfocus, important!
Except Mate also uses Ctrl-L to lock the screen. Now I actually don't know the password to my laptop. Autologin in lightdm and my management host can access both my account and the root account (while my other laptop uses fingerprint authentication to log in, but this one doesn't have it). Conveniently my laptop can also access the management host, provided a key from my password manager.. it makes more sense when you have a lot of laptops, servers and other such nuggets around. The workstations enter a centralized environment and have access to everything else on the network from there.
Point is, I don't know my password and currently this laptop is the only nugget that can actually get this password out of the password store.. but it was locked. You motherfucker for a lock screen! I ain't gonna restart lightdm, make it autologin again and lose all my work! No no no, we can do better. So I took my phone which can also access the management host, logged in as root on my laptop and just killed mate-screensaver instead. I knew that it was just an overlay after all, providing little "real" security. And I got back in!
Now this shows an important security problem. Lock screens obviously have it.. crash the lock screen somehow, you're in. Because behind that (quite literally) is your account, still logged in. Display managers have it too to some extent, since they run as root and can do autologin because root can switch user to anyone else on the system without authentication. You're not elevating privileges by logging in, you're actually dropping them. Just something to think about.. where are we just adding cosmetic layers and where are we actually solving security problems? But hey, at least it helped this time. Just kill the overlay and bingo bango, we're in!2 -
Can anyone help me with this theory about microprocessor, cpu and computers in general?
( I used to love programming when during school days when it was just basic searching/sorting and oop. Even in college , when it advanced to language details , compilers and data structures, i was fine. But subjects like coa and microprocessors, which kind of explains the working of hardware behind the brain that is a computer is so difficult to understand for me 😭😭😭)
How a computer works? All i knew was that when a bulb gets connected to a battery via wires, some metal inside it starts glowing and we see light. No magics involved till now.
Then came the von Neumann architecture which says a computer consists of 4 things : i/o devices, system bus ,memory and cpu. I/0 and memory interact with system bus, which is controlled by cpu . Thus cpu controls everything and that's how computer works.
Wait, what?
Let's take an easy example of calc. i pressed 1+2= on keyboard, it showed me '1+2=' and then '3'. How the hell that hapenned ?
Then some video told me this : every key in your keyboard is connected to a multiplexer which gives a special "code" to the processer regarding the key press.
The "control unit" of cpu commands the ram to store every character until '=' is pressed (which is a kind of interrupt telling the cpu to start processing) . RAM is simply a bunch of storage circuits (which can store some 1s) along with another bunch of circuits which can retrieve these data.
Up till now, the control unit knows that memory has (for eg):
Value 1 stored as 0001 at some address 34A
Value + stored as 11001101 at some address 34B
Value 2 stored as 0010 at some Address 23B
On recieving code for '=' press, the "control unit" commands the "alu" unit of cpu to fectch data from memory , understand it and calculate the result(i e the "fetch, decode and execute" cycle)
Alu fetches the "codes" from the memory, which translates to ADD 34A,23B i.e add the data stored at addresses 34a , 23b. The alu retrieves values present at given addresses, passes them through its adder circuit and puts the result at some new address 21H.
The control unit then fetches this result from new address and via, system busses, sends this new value to display's memory loaded at some memory port 4044.
The display picks it up and instantly shows it.
My problems:
1. Is this all correct? Does this only happens?
2. Please expand this more.
How is this system bus, alu, cpu , working?
What are the registers, accumulators , flip flops in the memory?
What are the machine cycles?
What are instructions cycles , opcodes, instruction codes ?
Where does assembly language comes in?
How does cpu manipulates memory?
This data bus , control bus, what are they?
I have come across so many weird words i dont understand dma, interrupts , memory mapped i/o devices, etc. Somebody please explain.
Ps : am learning about the fucking 8085 microprocessor in class and i can't even relate to basic computer architecture. I had flunked the coa paper which i now realise why, coz its so confusing. :'''(14 -
StackOverflow locked my account. I'm hoping someone here might be kind enough to help me with a bash script I'm "bashing" my head with. Actually, it's zsh on MacOS if it makes any difference.
I have an input file. Four lines. No blank lines. Each of the four lines has two strings of text delimited by a tab. Each string on either side of the tab is either one word with no spaces or a bunch of words with spaces. Like this (using <tab> as a placeholder here on Devrant for where the tab actually is)
ABC<tab>DEF
GHI<tab>jkl mno pq
RST<tab>UV
wx<tab>Yz
I need to open and read the file, separate them into key-value pairs, and put them into an array for processing. I have this script to do that:
# Get input arguments
search_string_file="$1"
file_path="$2"
# Read search strings and corresponding names from the file and store in arrays
search_strings=()
search_names=()
# Read search strings and corresponding names from the file and store in arrays
while IFS= read -r line || [[ -n "$line" ]]; do
echo "Line: $line"
search_string=$(echo "$line" | awk -F'\t' '{print $1}')
name=$(echo "$line" | awk -F'\t' '{print $2}')
search_strings+=("$search_string")
search_names+=("$name")
done < "$search_string_file"
# Debug: Print the entire array of search strings
echo "Search strings array:"
for (( i=0; i<${#search_strings[@]}; i++ )); do
echo "[$i] ${search_strings[$i]} -- ${search_names[$i]}"
done
However, in the output, I get the following:
Line: ABC<tab>DEF
Line: GHI<tab>jkl mno pq
Line: RST<tab>UV
Line: wx<tab>Yz
Search strings array:
[0] --
[1] ABC -- DEF
[2] GHI -- jkl mno pq
[3] RST -- UV
That's it. I seem to be off by one because that last line...
Line: wx<tab>Yz
never gets added to the array. What I need it to be is:
[0] ABC -- DEF
[1] GHI -- jkl mno pq
[2] RST -- UV
[3] wx -- Yz
What am I doing wrong here?
Thanks. 13
13 -
So... I’ve recently started a new role, and luckily I’ve established myself as someone that knows his shit (more or less) TM.
I’m leading the charge on tech debt, and raising issues about it, first on my radar is the monstrosity of their approach to app config.
It’s a web app, and they store config in a key-value table in the database.
Get this. The key is the {type}.{property} path and this is fetched from the database and injected *at construction* via reflection.
Some of these objects get instantiated dozens of times per-request. Eurgh. -
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
Noob question
I’m trying to deploy my front end web app (my personal website) to GitHub pages.
In my app, I used react environment variables to store a api key I need in my app.
When I deploy my app with GitHub pages, will the app still be able to access the react env variables?
Let me know if that doesn’t make sense. Thanks!7 -
Opinions please.
I want to share a small model in my iOS app. Now on android I'd do with with ViewModelProviders, but on iOS I'm going with SharedDataContainer which is basically a singleton class that store key value data.
Is there any better approach? Data will not be bigger than 10 list items with guid (key) and int (value)
However; when I have big data I do cache on disk or hello OOM exceptions (or whatever they call that bitch on iOS) -
I hate group project so much.
I yet again successfully stirred up a big drama in my project group. For project, I proposed a CDN cache system for a post only database server. Super simple. I wanted to see what ideas other people come up with. So I said I am not good at the content and the idea is dumb. Oh man, what a horrible mistake. One group member wants to build a chat app with distributed storage. We implemented get/put for a terribly designed key value store and now they want to build a freaking chat app on top of a more stupid kV store using golang standard lib. I don't think any of those fools understand the challenges that comes with the distributed storage.
I sent a video explaining part of crdt. "That's way too complicated. Why are you making everything complicated."
Those fools leave too much details for course stuff's interpretation and says
"course stuff will only grade the project according to the proposal. It's in the project description".
I asked why don't they just take baby steps and just go with their underlying terribly designed kV store.
"Messaging app is more interesting and designing kV store with generic API is just as difficult"
😂 Fucking egos
Then I successfully pissed off all group members with relatively respectful words then pissed off myself and joined another group.1 -
Chinese remainder theorem
So the idea is that a partial or zero knowledge proof is used for not just encryption but also for a sort of distributed ledger or proof-of-membership, in addition to being used to add new members where additional layers of distributive proofs are at it, so that rollbacks can be performed on a network to remove members or revoke content.
Data is NOT automatically distributed throughout a network, rather sharing is the equivalent of replicating and syncing data to your instance.
Therefore if you don't like something on a network or think it's a liability (hate speech for the left, violent content for the right for example), the degree to which it is not shared is the degree to which it is censored.
By automatically not showing images posted by people you're subscribed to or following, infiltrators or state level actors who post things like calls to terrorism or csam to open platforms in order to justify shutting down platforms they don't control, are cut off at the knees. Their may also be a case for tools built on AI that automatically determine if something like a thumbnail should be censored or give the user an NSFW warning before clicking a link that may appear innocuous but is actually malicious.
Server nodes may be virtual in that they are merely a graph of people connected in a group by each person in the group having a piece of a shared key.
Because Chinese remainder theorem only requires a subset of all the info in the original key it also Acts as a voting mechanism to decide whether a piece of content is allowed to be synced to an entire group or remain permanently.
Data that hasn't been verified yet may go into a case for a given cluster of users who are mutually subscribed or following in a small world graph, but at the same time it doesn't get shared out of that subgraph in may expire if enough users don't hit a like button or a retain button or a share or "verify" button.
The algorithm here then is no algorithm at all but merely the natural association process between people and their likes and dislikes directly affecting the outcome of what they see via that process of association to begin with.
We can even go so far as to dog food content that's already been synced to a graph into evolutions of the existing key such that the retention of new generations of key, dependent on the previous key, also act as a store of the data that's been synced to the members of the node.
Therefore remember that continually post content that doesn't get verified slowly falls out of the node such that eventually their content becomes merely temporary in the cases or index of the node members, driving index and node subgraph membership in an organic and natural process based purely on affiliation and identification.
Here I've sort of butchered the idea of the Chinese remainder theorem in shoehorned it into the idea of zero knowledge proofs but you can see where I'm going with this if you squint at the idea mentally and look at it at just the right angle.
The big idea was to remove the influence of centralized algorithms to begin with, and implement mechanisms such that third-party organizations that exist to discredit or shut down small platforms are hindered by the design of the platform itself.
I think if you look over the ideas here you'll see that's what the general design thrust achieves or could achieve if implemented into a platform.
The addition of indexes in a node or "server" or "room" (being a set of users mutually subscribed to a particular tag or topic or each other), where the index is an index of text audio videos and other media including user posts that are available on the given node, in the index being titled but blind links (no pictures/media, or media verified as safe through an automatic tool) would also be useful.9 -
What is the reason behind Git Access Tokens being viewable only once after generation on platforms like GitHub? I'm struggling to comprehend this approach as it compels me to store the key in an insecure manner.2
-
Had that moment where I thought to myself I need some sleep.
Working on Android app, using shared preferences (for a lay person, a key value store for settings)
Kept storing data in store and checked repeatedly from different parts of the app for the data. No clue where it went when storing (did store correctly)
Found out I was storing in a store labelled X _Y and was reading from store called XY.3 -
PrestaShop irony:
* Theirs modules have >3500 lines per class (eg. blocklayered.php)
* Theirs controllers have > 5000 lines and contains a LOT of html code inside
AND when I tried to add own module to theirs addons store they declined it because:
* I had unused $key var in foreach and this is "bad practice" as I was told
* In one hook I was returning 1 line of html code (i had to add global Js var) and they told me that I should put it into separate template file
-.-'2 -
I identified the need for a product akin to an ORM that maps an algebraic type system such as that of Rust to a key-value database (my situation dictates lmdb but I'd like to abstract away the store). Can you recommend prior art for me to research?4
-
Have been searching on this topic alot lately, but I cant find any good solution, in my opinion.
I have a system where I want to encrypt some data in the database, so it isn't in plain text, but how would you do it properly?
It has to be decrypted to view the data in the system, but how to manage it?
How can I store the keys in the right way? In my current trial, I have a encryption key and an iv, but wouldn't it be wrong to store the encryption key in the config file?
Can't really see how to grasp this the right way and in the same way have it as secure as possible.
Is it just stupid in general? -
I have to deal with the hardest part of programming: naming things! i fucking hate it, being so incredible uncreative finding a name for a side project..
So heres my idea: I want to build a little cli tool (and probably in the future an app or a web interface) with a rest api on my server for simple storing text snippets. I will be a simple key value store, but my goal is experimenting with new languages and software ;)
I can't imagine a cool name for that thing, do you have an idea? :)3 -
Why are USB passkeys so expensive? I was under the impression that you 1) create a key pair, upload the public key to your google account and 2) store the private key on an old USB drive. But nooo, then you could copy the key I guess. Good luck convincing the average Joe to spend more than $10 on a fido/yubi/whatever key...3
-
In the fast-paced world of retail, understanding customer behavior and optimizing store operations are key to success. Retail footfall analysis provides valuable insights into how shoppers interact with your store, helping you make data-driven decisions to enhance performance and drive growth. Here’s how leveraging footfall analysis can revolutionize your retail marketing analytics consulitng strategy.
What is Retail Footfall Analysis?
Retail footfall analysis refers to the process of measuring and interpreting customer traffic patterns within a retail environment. This analysis involves collecting data on the number of visitors, their movement within the store, and their dwell times. By examining this data, retailers can gain a deeper understanding of shopper behavior, store performance, and the effectiveness of marketing strategies.
Benefits of Retail Footfall Analysis
Optimize Store Layout: By analyzing how customers navigate through your store, you can redesign layouts to improve traffic flow and increase the visibility of high-margin or promotional items. Strategic placement of products can enhance the shopping experience and drive sales.
Enhance Customer Experience: Understanding peak traffic times allows you to manage staffing levels more effectively. Ensuring adequate staff during busy periods can improve customer service and satisfaction, while reducing labor costs during quieter times.
Evaluate Marketing Effectiveness: Footfall analysis helps assess the impact of marketing campaigns and promotions. By comparing traffic data before, during, and after a campaign, you can determine what drives the most foot traffic and adjust future marketing strategies accordingly.
Improve Inventory Management: Analyzing foot traffic data helps with inventory planning by identifying which products attract the most customers. This insight allows you to better manage stock levels and avoid both overstocking and stockouts.
Drive Sales Growth: With detailed insights into customer behavior, you can make informed decisions to boost sales. For example, adjusting store layouts, optimizing product placement, and fine-tuning promotional strategies based on footfall data can lead to increased revenue.
How Retail Footfall Analysis Works
Data Collection: Footfall data is collected using various technologies such as infrared sensors, video cameras, and Wi-Fi tracking. These tools capture information on the number of visitors, their movement patterns, and the time they spend in different areas of the store.
Data Analysis: The collected data is analyzed to uncover patterns and trends. Key metrics include foot traffic volume, peak shopping times, customer dwell times, and the effectiveness of different store areas.
Insights and Recommendations: Based on the analysis, actionable insights are provided. This might include recommendations for store layout changes, staffing adjustments, or marketing strategies to better align with customer behavior.
Implementation: Retailers implement the recommendations to optimize store performance. This may involve reconfiguring store layouts, adjusting staffing schedules, or launching targeted marketing campaigns.
Ongoing Monitoring: Retail footfall analysis is an ongoing process. Continuous monitoring allows retailers to stay responsive to changes in customer behavior and market conditions, ensuring sustained improvements in store performance.
Why Retail Footfall Analysis Matters
Enhanced Customer Understanding: Provides a clear picture of how customers interact with your store, leading to better decision-making.
Increased Efficiency: Helps optimize store operations and resource allocation, improving overall efficiency and effectiveness.
Data-Driven Decisions: Enables retailers to make informed decisions based on concrete data rather than intuition or guesswork.
Conclusion
Retail footfall analysis is a powerful tool for optimizing store performance and driving business growth. By understanding customer behavior and traffic patterns, retailers can make strategic adjustments to store layouts, staffing levels, and marketing efforts, ultimately enhancing the shopping experience and boosting sales.
Leverage the insights from retail footfall analysis to transform your store operations and stay ahead of the competition. With the right approach, you can unlock new opportunities for success and achieve your retail goals. rant store analytics retail store analytics ai in retail retail video analytics store footfall analytics ai in retail industry retail footfall analytics artificial intelligence in retail
rant store analytics retail store analytics ai in retail retail video analytics store footfall analytics ai in retail industry retail footfall analytics artificial intelligence in retail -
Hypoallergenic Dog Breeds
A sizable bit of the American public is really powerless against canines: around 10% (as per America College of Allergy, Asthma, and immunology). Dreadfully, various canine darlings experience the malevolent effects of sensitivities and need to regulate unmistakable extraordinary trickiness assaults as they can't battle the compulsion to assist the four-legged venerating creatures.
This can be an issue for canine darlings who may be experiencing lively troubles and mental issues, as they would have discovered some comfort or settlement in reiterating with their pet canine. Different individuals save a pet subsequently through an ESA letter, which permits these individuals to keep up their psychological achievement. These individuals can additionally profit by express laws and establishments that are set to help those with mental prosperity issues.
In any case, all isn't lost for individuals with sensitivities needing a pet canine as an energized support creature, for there are unmistakable canine arrangements that, at any rate, not 100% hypoallergenic, think about extraordinary trickiness enduring individuals to get or get canines as pets.
What are hypoallergenic canines?
Canines regularly shed their hair dependably and irregularly. The fine hair by then gets joined to any surface it sticks on, particularly on surfaces. Notwithstanding, it isn't normally the shedding that immediately triggers the affectability yet the peril of the canine and other fine particles that catch onto the hair. For various creatures, the allergenic can take various structures, for instance for felines it is in their salivation which gets onto their hair during planning. If you want to keep your pet inside your house you should have an ESA letter for housing.
A hypoallergenic canine is one that doesn't store allergens of any structure through either the dander locking onto the stowaway. Canines, notwithstanding, are not absolutely hypoallergenic, in any case with a blend of a low shedding canine variety and worthwhile getting ready, you can have a canine that makes individuals with hypersensitivities immaterial no difficulty.
Fiery Support Animal Letter(ESA Letter) for your hypoallergenic canine?
The ESA letter is a letter given to the canine proprietor by an affirmed emotional well-being master, in the wake of evaluating the ability of the said proprietor through an assessment. The appraisal will regard if the individual is experiencing mental or anxious distress or hardship and s/he needs the pet canine's connection to lessen the issues and feel regular. If you have a pet you should have an emotional support animal letter.
The ESA Letter joins the quality of the expert and a confirmed stamp and notices explicitly that the individual necessities to have the canine with them dependably for their psychological and lively strength.
This letter will keep on assisting the energized help creature proprietors with profiting by-laws that award their pets to be with them during voyaging or in their lodging.
The particular hypoallergenic canine arrangements
The American Kennel Club, set up in 1885 is one of the authentic voices on canine arrangements, preparing, and success.If you have other creatures, you should have an emotional support dog letter.
It beginning late passed on a diagram of canines that are close to being hypoallergenic and are ideal for individuals with hypersensitivities. A portion of the canines related to the quick overview is:
Affenpinscher
Maltese
Afghan Hound
American Hairless Terrier
Poodle
Yorkshire Terrier
Basenji
Bichon Frise
Shih Tzu
Chinese Crested
Coton de Tulear
Little Schnauzer
Irish Water Spaniel
Kerry Blue Terrier
Alongside these groupings, there are different collections that are reasonable for handily influenced individuals. The key brand name that makes these creatures reasonable is their irrelevant or low shedding stow away. With relentless getting ready and bit by bit brushing, you can get essentially more sure outcomes. It comparatively helps if the hair on the canine is wiry and human-like, for example, the Afghan Hound, or near zero body stow away, for example, the American Hairless Terrier and the Basenji. If you do not have an ESA letter you can apply for ESA letter online. -
REACH OUT TO A POTENTIAL BITCOIN/USDT/ETH RECOVERY EXPERT- HIRE SPARTAN TECH GROUP RETRIEVAL
As a freelancer and part-time cryptocurrency trader, I had built up over $200,000 worth of Bitcoin in my digital wallet. What began as a casual interest in cryptocurrency quickly turned into a profitable venture, helping me cover tuition and living expenses. However, a seemingly small accident during a family holiday in the Maldives nearly led to a catastrophic financial loss. One afternoon, while soaking in the picturesque beauty of the Maldives, I decided to take a selfie to capture the moment. In my excitement, my phone slipped from my hands and shattered on the pavement below. At first, I was upset about losing my device, but soon, a far more alarming realization hit me. I had also lost access to my Bitcoin wallet. My recovery phrase, the key to restoring my funds, had not been stored in a secure location, leaving me with no way to retrieve my wallet. Panic set in as I considered the possibility of losing years of earnings and investments. Determined to find a solution, I began scouring the internet for any service that could help. That was when I came across SPARTAN TECH GROUP RETRIEVAL. Although skeptical about the chances of success, I had nothing to lose, so I reached out to their team on WhatsApp:+1 (971) 4 8 7 -3 5 3 8, explaining my predicament in detail. To my relief, they responded promptly and professionally, assuring me they had the expertise to attempt a recovery. They explained the process clearly, starting with verifying my identity and wallet ownership. Once those steps were completed, their team immediately got to work. Despite the challenges posed by my shattered device and the missing recovery phrase, SPARTAN TECH GROUP RETRIEVAL team demonstrated exceptional skill and persistence. Within just a few days, they successfully recovered my wallet and restored access to my funds. The relief and gratitude I felt were indescribable. This incident was a wake-up call. Beyond recovering my funds, SPARTAN TECH GROUP RETRIEVAL took the time to educate me on the importance of proper security measures. They stressed the need to store recovery phrases in secure offline locations, use hardware wallets, and implement two-factor authentication to safeguard assets against loss or theft. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to avoid a disastrous financial setback. Their professionalism, expertise, and guidance not only saved my investment but also prepared me to navigate the crypto world more securely in the future.
INFO ABOUT THE COMPANY>>>> >>
Email : spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 3
3 -
Gulf Coast Pro Wash, LLC: Enhanced Curb Appeal, Paver Cleaning, and Storefront Cleaning in Port Charlotte, FL
At Gulf Coast Pro Wash, LLC, we understand how important it is to maintain the beauty and cleanliness of your property. Whether you're a homeowner wanting to boost your home's curb appeal or a business owner looking to keep your storefront looking fresh, we offer professional cleaning services tailored to meet your needs. Serving Port Charlotte, FL, and surrounding areas, we specialize in services like enhanced curb appeal, paver cleaning, and storefront cleaning that will help elevate the appearance of your property and make a lasting first impression.
Enhanced Curb Appeal: Make Your Property Stand Out
Your home’s exterior is the first thing people notice, and enhanced curb appeal can make all the difference when it comes to creating a welcoming atmosphere. Whether you're planning to sell your home or simply want to enjoy a beautifully maintained property, increasing your curb appeal is one of the best ways to make a statement.
At Gulf Coast Pro Wash, LLC, we offer a variety of services designed to boost your property's curb appeal. From soft washing your house’s exterior and cleaning your driveway to paver cleaning and pressure washing your fence, our team can handle all of your exterior cleaning needs. Our expert team uses high-quality equipment and safe, eco-friendly cleaning solutions to make sure your property shines, increasing both its beauty and value.
Paver Cleaning: Restore the Beauty of Your Walkways and Patios
Pavers are a popular choice for driveways, patios, and walkways, thanks to their durability and aesthetic appeal. However, over time, dirt, grime, weeds, and algae can build up, causing your pavers to lose their luster. Paver cleaning is an essential service to maintain the appearance and functionality of your paver surfaces.
At Gulf Coast Pro Wash, LLC, we offer specialized paver cleaning services that remove dirt, mold, mildew, and other debris without damaging the paver surface. We use the appropriate pressure and cleaning techniques to safely restore the color and texture of your pavers, leaving them looking as good as new. Our professional cleaning not only improves the appearance of your patios, driveways, and walkways but also helps prevent future buildup, ensuring long-lasting beauty and durability.
Storefront Cleaning: Keep Your Business Looking Its Best
As a business owner, your storefront is the first thing potential customers see when they approach your store. A clean, well-maintained storefront is key to making a positive first impression and encouraging customers to walk in. Over time, dirt, grime, and other contaminants can accumulate on windows, doors, sidewalks, and walls, diminishing your business's curb appeal.
Storefront cleaning is a vital service to maintain the cleanliness and professionalism of your commercial property. At Gulf Coast Pro Wash, LLC, we offer expert storefront cleaning that includes cleaning windows, pressure washing the exterior, and removing dirt and debris from walkways. Our team uses safe, effective techniques to ensure your storefront shines, making it inviting for customers and giving your business a polished, professional look. Whether you run a restaurant, retail store, or office, we’ll help you make a lasting impression with a spotless storefront.
Why Choose Gulf Coast Pro Wash, LLC?
When you choose Gulf Coast Pro Wash, LLC for your enhanced curb appeal, paver cleaning, and storefront cleaning needs, you're choosing a team of experienced professionals who care about delivering exceptional results. Here’s why we’re the trusted choice for property owners in Port Charlotte, FL:
Experienced Technicians: Our team is highly trained in the latest cleaning techniques, ensuring safe and effective results for all surfaces.
State-of-the-Art Equipment: We use high-quality equipment and eco-friendly cleaning solutions to achieve the best results without harming the environment.
Affordable Pricing: We offer competitive pricing with transparent, no-hidden-fee estimates so you know exactly what to expect.
Customer Satisfaction Guaranteed: We are committed to providing outstanding service and ensuring that you are completely satisfied with the results.
Contact Gulf Coast Pro Wash, LLC Today!
If you want to enhance your curb appeal, restore the beauty of your pavers, or maintain a spotless storefront, Gulf Coast Pro Wash, LLC is here to help. We are proud to serve Port Charlotte, FL, and surrounding areas with professional cleaning services that will leave your property looking its best.
Call us today at +1 (941) 830-5630 to schedule an appointment or request a free estimate. Let us help you boost your property’s appearance with our expert cleaning services! 1
1 -
The Bravo CX 7000 ID Card Printer is a highly versatile printing solution for organizations seeking to create professional-quality ID cards with advanced security features. The Bravo ID card printers feature a modular, cube design that allows for easy configuration and scalability and can be used to print single and dual-sided cards with high-resolution images and text.
One of the key features of the Bravo CX 7000 ID Card Printer is its re-transfer printing technology, which ensures that images are printed onto the card surface with exceptional accuracy and durability. This technology also enables the printer to print onto various card types, including PVC, ABS, and PET materials. The Bravo ID Card Printer also includes advanced security features such as UV printing, which allows for the inclusion of invisible security elements such as watermarks or micro text, and magnetic stripe encoding, which can be used to store sensitive information on the card.
The Bravo ID Card Printers are an excellent choice for organizations that require a versatile and secure ID card printing solution. Its modular design, re-transfer printing technology, and advanced security features make it an ideal choice for a wide range of applications, including government, healthcare, and corporate settings. -
LOST WAILLET PRIVATE KEY RECOVERY HIRE DUNAMIS CYBER SOLUTION
I spend my days unraveling the mysteries of the universe, trying to make sense of quantum entanglement, Schrödinger's cat, and the nature of reality itself. But despite my expertise in the fundamental forces of the cosmos, I somehow managed to completely lose access to my own Bitcoin wallet.
Now, I thought myself a prudent man. Of course, I knew better than to write down my private keys in some kind of digital file that could get hacked, and I certainly was not about to trust my notoriously bad human memory. So I came up with what I figured was a brilliant security scheme: I wrote down my wallet credentials on a strip of paper, and then proceeded to bury that paper deep within my favorite book on physics, A Brief History of Time, by Stephen Hawking. A perfect plan. Wrong. One day, in a moment of charity-or maybe even utter absent-mindedness-I decided to donate a box of books to a local charity. Noble, noble act. Well, you might have guessed it: my whole financial future was tucked inside one of those books. It wasn't until weeks later that I realized the horrifying truth: my $500,000 in Bitcoin was now floating around in some secondhand bookstore, completely out of my reach.
Cue existential crisis. I tore my apartment apart, retracing every step I had taken over the past month. I even went back to the bookstore and bought back as many of my donated books as I could find. But A Brief History of Time? Gone. Vanished. Probably sitting on someone's bookshelf, holding a fortune they didn't even know existed. When the loss seemed total-when I'd even considered the possibility that quantum tunneling might somehow return the book to me-I called in DUNAMIS CYBER SOLUTION. I was skeptical-if I couldn't even recover my own password, how could they? But their team was reassuring, methodical, and oddly calm about my ridiculous mistake. They assured me they'd seen worse (which I still refuse to believe), and they got to work. Weeks passed, and just when I was about to come to terms with financial realities, they cracked it-somehow, through sheer digital DUNAMIS CYBER SOLUTION my lost Bitcoin. Indescribable relief-I felt like I had just solved the Unified Field Theory.
The moral of the story? Never trust your memory. Never store your fortune in a book. And if you ever lose access to your Bitcoin, call DUNAMIS CYBER SOLUTION. They don't just perform miracles-they undo the kind of mistakes that even quantum physics can't explain 1
1 -
Candle Packaging: The Ultimate Guide to Elevate Your Brand
Why Candle Packaging Matters
Candle packaging plays a crucial role in both protecting the product and enhancing its aesthetic appeal. In today’s competitive market, attractive and functional packaging is essential for capturing customer attention, ensuring product safety, and reinforcing brand identity.
Key Elements of High-Quality Candle Packaging
1. Material Selection
The material used in candle packaging is critical in maintaining product integrity, durability, and aesthetic appeal. Some of the most commonly used materials include:
Cardboard and Paperboard: Lightweight, eco-friendly, and customizable for different styles.
Glass Jars: Ideal for luxury candles, offering a sophisticated and protective housing.
Metal Tins: Travel-friendly and durable, suitable for compact packaging.
Plastic Containers: Cost-effective and versatile, though less eco-friendly.
2. Branding and Customization
Strong branding elements on packaging create a lasting impression. Effective branding strategies include:
Embossed or Foil Stamping: Adds a luxurious touch to your packaging.
Minimalist Designs: Clean and modern looks that appeal to high-end consumers.
Personalized Labels: Custom labels with unique typography and graphics enhance the visual appeal.
Window Cutouts: Allow customers to see the candle inside without opening the package.
3. Sustainable and Eco-Friendly Options
With the increasing demand for sustainable packaging, brands should consider:
Biodegradable Materials: Such as kraft paper and recycled cardboard.
Reusable Packaging: Containers that customers can repurpose.
Soy-Based Inks: An eco-friendly printing option.
Types of Candle Packaging
1. Luxury Candle Packaging
Premium candles require high-end packaging that reflects the exclusivity of the product. Features include:
Rigid boxes with magnetic closures for a sleek unboxing experience.
Velvet or satin lining for added elegance.
Gold or silver foil accents for a sophisticated appeal.
2. Gift Candle Packaging
Candle packaging designed for gifting should be visually appealing and ready for presentation. Common features include:
Decorative boxes with ribbons and bows.
Themed packaging for seasonal gifts (Christmas, weddings, birthdays).
Custom messages or engravings for personalization.
3. Wholesale and Bulk Candle Packaging
For businesses selling candles in bulk, efficiency and cost-effectiveness are key. Features include:
Stackable and compact designs for easy shipping.
Corrugated cardboard for added durability.
Minimalist branding to reduce production costs.
Candle Packaging Design Trends
1. Minimalist and Elegant Designs
Simplicity is the new luxury. Many brands opt for clean lines, neutral tones, and minimal text to create an elegant and modern look.
2. Sustainable and Eco-Conscious Packaging
More consumers are leaning towards zero-waste and biodegradable materials, making sustainable packaging a priority for many brands.
3. Interactive and Innovative Packaging
Unique and functional packaging elements, such as hidden compartments, scented boxes, and reusable containers, help brands stand out.
4. Personalization and Customization
Personalized packaging with handwritten notes, custom scents, or tailored designs enhances customer engagement and loyalty.
Best Practices for Candle Packaging
Ensure Proper Labeling: List essential information such as scent, burn time, safety warnings, and ingredients.
Protect Against Heat and Damage: Use heat-resistant materials and secure sealing to prevent wax melting.
Prioritize User Experience: Packaging should be easy to open, store, and recycle.
Focus on Aesthetic Appeal: Visually appealing packaging attracts impulse buyers and repeat customers.
Conclusion
Investing in well-designed candle packaging not only enhances product safety but also boosts brand recognition and customer appeal. Whether opting for luxurious, eco-friendly, or cost-effective packaging, brands should prioritize quality, innovation, and sustainability to stand out in the competitive market.2 -
What are the parts of the CNC Wire Bending Machine?
A CNC wire bending machine is a complex piece of equipment used to bend the wire into various shapes and configurations with precision. It consists of several key parts and operates based on the instructions provided by a computer program. Here are the main parts of a CNC wire-bending machine and an overview of how it works:
1. Wire Feeding Mechanism:
This part of the machine is responsible for feeding the wire from a coil or spool into the bending area.
Wire feeding mechanisms can include rollers, pulleys, or servo-driven motors that control the wire's movement.
2. Straightening Unit:
- Before bending, the wire may pass through a straightening unit, which ensures that the wire is free from kinks and bends.
- This step helps produce precise bends by starting with a straight wire.
3. Bending Head and Tooling:
- The bending head contains the tools and dies needed to shape the wire.
- Tooling includes various components such as clamps, rollers, and mandrels that hold and shape the wire according to the desired design.
4. Guide Rollers and Pulleys:
- These components help guide the wire through the bending process, ensuring it follows the correct path and angles.
5. Control Panel or Interface:
- CNC wire bending machines are typically equipped with a control panel or computer interface.
- Operators input the design specifications, such as bend angles, lengths, and shapes, through this interface.
6. Computer Control System:
- The heart of the CNC wire bending machine is its computer control system.
- It interprets the design specifications and converts them into precise movements and commands for the machine.
- CNC software programs are used to create and store the bending instructions.
7. Servo Motors and Actuators:
- These components are responsible for moving the bending head, tooling, and other parts of the machine with high precision.
- Servo motors and actuators receive commands from the control system to carry out specific movements.
8. Sensors and Feedback Mechanisms:
- Sensors placed throughout the machine monitor various parameters, such as wire position, tension, and tooling alignment.
- Feedback from these sensors allows the machine to make real-time adjustments, ensuring accuracy and quality in the final product.
-
Custom Lip Gloss Boxes: The Ultimate Guide to Stylish and Functional Packaging
In the beauty industry, packaging is just as important as the product itself. It serves not only to protect and preserve the product but also plays a pivotal role in branding, marketing, and influencing consumer choices. When it comes to lip gloss, custom packaging offers endless possibilities to create a unique brand presence. Custom lip gloss boxes are a key element in delivering that first impression, helping brands stand out in a competitive market.
This article delves into the importance of custom lip gloss boxes, their benefits, design considerations, and the latest trends shaping this packaging solution.
Why Custom Lip Gloss Boxes Matter
Lip gloss is a beauty staple, often viewed as a small, portable item, but its impact on a brand’s image can be significant. Custom lip gloss boxes elevate the product’s appeal, making it more attractive to consumers while offering protection during transport and storage. These boxes not only serve a practical purpose but also communicate a brand's values, creativity, and quality.
Key Benefits of Custom Lip Gloss Boxes
Brand Differentiation Custom packaging allows brands to create a distinct identity in the crowded beauty industry. With a range of customization options including colors, shapes, finishes, and design elements, brands can craft packaging that reflects their personality and vision, ensuring that their lip gloss stands out on store shelves.
Effective Marketing Tool A well-designed lip gloss box doubles as a marketing tool. With space for logos, taglines, product descriptions, and even social media handles, custom packaging reinforces brand recognition and helps consumers remember your product long after purchase.
Enhanced Product Protection While lip gloss tubes are often sturdy, custom boxes provide an added layer of protection, especially during shipping and handling. These boxes ensure the product arrives in perfect condition, preventing damage from impact, exposure to sunlight, or moisture.
Improved Consumer Experience Attractive and thoughtfully designed packaging enhances the unboxing experience, making it memorable for customers. This can lead to positive word-of-mouth, repeat purchases, and social media shares, all of which contribute to brand loyalty.
Eco-Friendly Options Many beauty brands are now shifting toward sustainable packaging solutions. Custom lip gloss boxes can be made from eco-friendly materials such as recycled cardboard or biodegradable paper. This not only reduces the environmental impact but also appeals to environmentally-conscious consumers.
Cost-Effective and Scalable Custom lip gloss boxes can be produced at scale, making them cost-effective for brands. Bulk production reduces the per-unit cost, making it an affordable option for businesses of all sizes, from boutique brands to large cosmetic companies.
Design Considerations for Custom Lip Gloss Boxes
Creating custom packaging involves several design elements that must be carefully thought out to achieve the desired look and functionality. Here are key aspects to consider:
Material Choice The material used for the custom lip gloss boxes should be durable yet lightweight. Popular materials include cardboard, kraft paper, and rigid boxes. Brands focused on sustainability may opt for eco-friendly or recycled materials, which can still deliver a high-end feel.
Size and Shape The size of the box should fit the lip gloss container snugly to avoid unnecessary movement and potential damage. While traditional rectangular boxes are common, unique shapes such as hexagonal or cylindrical boxes can make your packaging stand out.
Branding Elements Incorporating your brand’s logo, color palette, and fonts is essential in creating packaging that resonates with your target audience. Consistent use of branding elements across all your products helps build brand identity and consumer trust.
Printing and Finishing Options Various printing techniques and finishes can enhance the look and feel of your custom lip gloss boxes
Window Cutouts Adding a transparent window to your lip gloss boxes allows consumers to see the actual product without opening the packaging. This feature is particularly appealing when showcasing different lip gloss shades, helping consumers make purchasing decisions quickly.
Sustainability As consumers become more eco-conscious, brands can differentiate themselves by using recyclable, compostable, or biodegradable packaging materials. Eco-friendly packaging not only reduces your brand's carbon footprint but also enhances its image as a socially responsible entity.
Conclusion
Custom lip gloss boxes are a crucial element in building a strong brand presence and ensuring that your product catches consumers' attention. 2
2 -
Losing access to your cryptocurrency can be a devastating experience, whether due to forgotten passwords, hacking, scams, or technical errors. Fortunately, professional recovery services like BITCRACK RECOVERY EXPERTS specialize in retrieving lost or stolen crypto assets. If you’ve lost your Bitcoin or other cryptocurrencies, here’s how BITCRACK RECOVERY EXPERTS can help you recover your funds.
Why Choose BITCRACK RECOVERY EXPERTS?
BITCRACK RECOVERY EXPERTS is a trusted name in cryptocurrency recovery, offering advanced techniques to help victims of crypto theft, fraud, or accidental loss. Their team of blockchain forensic experts uses cutting-edge tools to trace transactions, identify wallet vulnerabilities, and recover inaccessible funds.
Services Offered by BITCRACK RECOVERY EXPERTS
Wallet Recovery – Regaining access to locked or lost crypto wallets.
Scam Investigation – Tracing stolen funds from fraudulent schemes.
Phishing & Hacking Recovery – Recovering crypto lost to cyberattacks.
Private Key Retrieval – Helping users restore lost or corrupted private keys.
Exchange & ICO Scam Recovery – Assisting victims of fake investment platforms.
Steps to Recover Your Lost Cryptocurrency
1. Contact BITCRACK RECOVERY EXPERTS
Reach out to their support team via email:
📧 bitcrackrecoveryexperts@bitcrack.co.site
Provide details such as:
The type of cryptocurrency lost (Bitcoin, Ethereum, etc.)
How the funds were lost (hack, scam, forgotten password, etc.)
Transaction details (wallet addresses, TXIDs, if available)
2. Initial Consultation & Case Evaluation
Their team will analyze your situation and determine the best recovery approach. They may request additional information to strengthen the investigation.
3. Recovery Process
Using blockchain forensics and legal methods, BITCRACK RECOVERY EXPERTS will trace the movement of your funds and attempt to recover them. This may involve:
Working with exchanges to freeze stolen assets
Identifying security breaches in wallets
Utilizing legal channels if necessary
4. Fund Retrieval & Secure Return
Once recovered, your cryptocurrency will be securely returned to a wallet under your control. The team ensures transparency throughout the process.
Tips to Avoid Future Crypto Losses
Use Hardware Wallets – Store crypto offline for maximum security.
Enable 2FA – Add an extra layer of protection to exchange accounts.
Beware of Scams – Avoid suspicious investment schemes and phishing links.
Backup Private Keys – Store keys securely in multiple locations.
Final Thoughts
Losing cryptocurrency doesn’t always mean it’s gone forever. With professional help from BITCRACK RECOVERY EXPERTS, there’s a strong chance of recovery. If you’ve fallen victim to theft, hacking, or accidental loss, don’t hesitate to contact them at:
✉️ bitcrackrecoveryexperts@bitcrack.co.site
Act quickly—the sooner you start the recovery process, the higher the chances of success2 -
Discover the Best Organic Honey at Dino Kelulut Organic Trigona Honey
At Dino Kelulut Organic Trigona Honey, we specialize in providing the finest quality organic honey, sourced from the stingless Trigona bees that produce Kelulut honey. Based in Petaling Jaya, Selangor, Malaysia, we are proud to be a leading provider of organic honey wholesale, catering to both local and international customers. Whether you're looking to buy organic honey for personal use or interested in purchasing in bulk, we offer a variety of options that ensure you're getting the purest, most nutritious honey available.
Why Choose Organic Honey?
Organic honey is produced without the use of harmful chemicals, pesticides, or artificial additives, making it a healthier and more natural alternative to conventional honey. The benefits of organic honey go beyond just being a natural sweetener—it is rich in antioxidants, vitamins, and minerals that support overall health.
At Dino Kelulut, our Kelulut honey is raw and unfiltered, meaning it retains all of its natural enzymes, nutrients, and health-promoting properties. Trigona honey, especially our organic honey, has a unique taste and texture, making it a prized product in the world of natural sweeteners.
The Benefits of Kelulut Honey
Kelulut honey is a special variety of honey produced by stingless bees, and it has several advantages over traditional honey. This honey is prized for its rich, tangy flavor and smooth consistency. Some key benefits of Kelulut honey include:
Rich in Antioxidants: Our Kelulut honey is packed with natural antioxidants, which help protect the body from oxidative stress and support the immune system.
Supports Digestive Health: The enzymes in Kelulut honey aid in digestion, making it a great choice for those seeking to improve gut health.
Natural Antibacterial Properties: The antimicrobial effects of Kelulut honey make it an excellent choice for soothing sore throats and promoting wound healing.
Boosts Energy: As a natural sweetener, Kelulut honey provides a quick energy boost without the harmful effects of refined sugars.
Whether you're using it in your daily tea, smoothies, or as a natural remedy, Kelulut honey offers a unique way to improve your health naturally.
Organic Honey Wholesale: A Trusted Source for Bulk Orders
At Dino Kelulut, we are a trusted organic honey wholesale supplier. Whether you are a retailer, distributor, or simply a large-scale consumer looking to buy in bulk, we can provide you with high-quality organic honey that meets your needs. We offer competitive pricing for wholesale orders, ensuring that you receive the best value without compromising on quality.
Our honey is harvested with care, ensuring that it maintains its natural purity, flavor, and health benefits. With our organic honey wholesale option, you can stock up on Kelulut honey and share its benefits with others, whether through your store or as a part of your product line.
Buy Organic Honey: Taste the Natural Sweetness
Looking to buy organic honey for personal use or as a healthy alternative to refined sugars? Dino Kelulut Organic Trigona Honey offers a range of honey products that cater to different tastes and preferences. Whether you are new to Kelulut honey or a long-time fan, our products offer the ideal choice for anyone who values purity, flavor, and health.
Our Kelulut honey is perfect for those who want to enjoy a natural sweetener that not only satisfies their cravings but also supports their overall health. Unlike processed sugars or syrups, Kelulut honey is packed with nutrients and antioxidants that can help maintain a balanced diet and boost your immune system.
Understanding Kelulut Honey Price
When it comes to the Kelulut honey price, you can be assured that you're paying for the highest quality. Kelulut honey is often priced higher than traditional honey due to its unique production process, limited availability, and the specialized care required to harvest it from stingless bees. However, the benefits far outweigh the price.
At Dino Kelulut, we are committed to offering Kelulut honey at a competitive price while maintaining its high standards of quality. Whether you’re purchasing a small jar for personal use or a bulk order for resale, you’ll find that our prices reflect the value and purity of the product.2
