Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API
From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "evidence"
-
D: “Did the attackers exfiltrate any data?”
M: “I can’t say for sure, but most likely based on—”
D: “—but did you find any undeniable evidence of it?”
M: “Keep in mind that the absence of evidence isn’t necessarily evidence of absence. There was very limited logging to begin with and the attacker erased artifacts and logs.”
D: “If there’s no evidence, then there was no exfiltration.”
M: “If a business doesn’t have cameras on its front door and then gets robbed, it can’t claim there was no robbery just because they didn’t video-record it.”
D: “That’s a poor analogy. Nothing’s missing here. I couldn’t care less if a robber made a *copy* of my money. That isn’t robbery.”
M: “... If the Titanic really hit an iceberg, then how come no pieces of an iceberg were ever found in the wreckage?”19 -
Asshole trying to steal credit for my work. Can't wait for the next meeting to light this shit.
So this client hires me and this person that I'm gonna call 'B'. B deletes my name from the comments and description. Then proceeds to present it as his.
But B can't get it to run now, so they have me have a look at it. B thinks that I don't notice that he is trying to take credit for my shit. Now I'm sitting here with evidence for the next meeting with the client. Ignoring all of B's communications.54 -
So, recently, a person in the US was arrested for stalking people.
The evidence was some data from google, a work computer and from a VPN provider.
Let's take a quick look at that VPN provider. It (PureVPN) says on their privacy policy page that they do NOT store logs.
Guess from what VPN provider the FBI got those logs? Yes, PureVPN!
Althouh I'm happy they got this creep off the street, it still means that PureVPN has been lying to its entire customer base.
I personally hope that their reputation will be destroyed now because this should never happen.
A screenshot I took from their privacy policy page is attached below.
Keep your eyes open when choosing a VPN provider!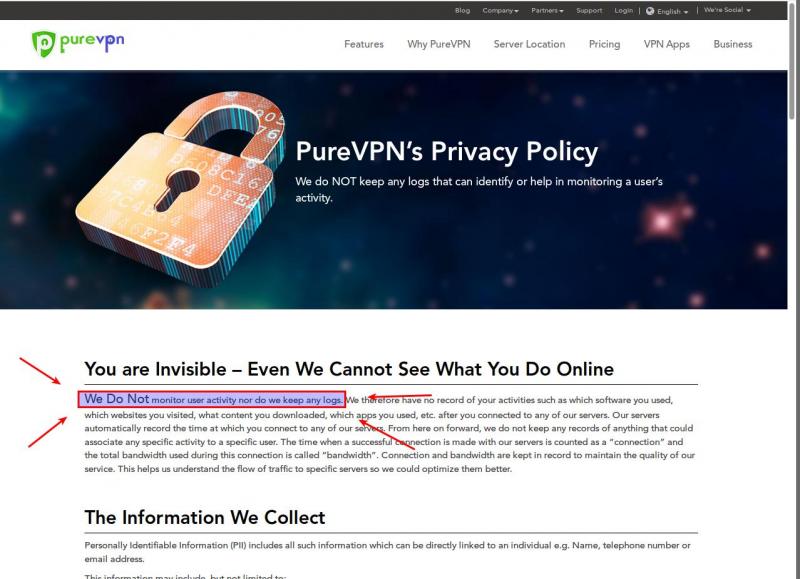 58
58 -
Me: Oh I see were using a non-standard architecture on this app. I like this bit but what is this doing? never seen it before.
Him: Ah we use that to abstract the navigation layer.
Me: oh ok, interesting idea, but that means we need an extra file per screen + 1 per module. We also can't use this inbuilt control, which I really like, and we've to write a tonne of code to avoid that.
Him: Yeah we wanted to take a new approach to fix X, this is what we came up with. Were not 100% happy with it. Do you have any ideas?
**
Queue really long, multi-day architecture discussion. Lots of interesting points, neither side being precious or childish in anyway. Was honestly fantastic.
**
Me: So after researching your last email a bit, I think I found a happy middle ground. If we turn X into a singleton, we can store the state its generating inside itself. We can go back to using the in-built navigation control and have the data being fetched like Y. If you want to keep your dependency injection stuff, we can copy the Angular services approach and inject the singletons instead of all of these things. That means we can delete the entire layer Z.
Even with the app only having 25% of the screens, we could delete like 30+ files, and still have the architecture, at a high level, identical and textbook MVVM.
Him: singleton? no I don't like those, best off keeping it the way it is.
... are you fucking kidding me? You've reinvented probably 3 wheels, doubled the code in the app and forced us to take ownership of something the system handles ... but a singleton is a bad idea? ... based off no concrete evidence or facts, but a personal opinion.
... your face is a bad idea15 -
So I've been screaming for months that push notifications are not reliable enough to build critical functionality on top of. Management won't listen and keep pushing ahead with making teams use it because its cheap and easy.
Been debugging an issue on/off for several weeks. Turns out someone in management asked the backend team to cut the expiration time of items down to 5 minutes to increase throughput (without telling mobile). Notifications are regularly taking +4 mins to get to the phones, leaving our users with barely any time to react. They are now complaining.
I swear if there is a single IQ point available between the whole team i've yet to see any evidence of it8 -
Now, I work at a hosting company in the UK, as a linux support engineer. I've seen many cases where a number of clients ran one of the following:
rm -rf / something
rm -rf /var/cache (attempt to magento)
chmod 777 /var
chown -R user:user /*
Half the time, they're like "Hey guys, I dun did fuck up, please help!". The other half of the time, they piss me off. Here's a number of responses that really grinds my gears:
"Such a harmful command should really prompt for input before running" -- From the buy you "forced" a recursive rm command, which mutes such a feature.
Client: "I did no such thing"
Me: "I've seen the command history, and at the time the command was run, you were the only person logged in"
Client: "You're mistaken, You're reading the information wrong"
Me: "I assure you, I'm not, I know what I'm looking at"
Client: "Well you're a shit engineer"
Me (thought): "Says the fucker who doesn't know how to linux"
I like people who own up to fuck ups. But the ones that don't, are just making their lives harder, since we have all the evidence in front of us.
Most of these people are the developers, and in some cases, the sysadmins...4 -
I send a PR to your GitHub repo.
You close it without a word.
I tell you that your lib crashes because you're trying to parse JavaScript with a (bad) regex, but you keep insisting that no, there exist no problem, and even if you barely know what "parsing" means, you keep denying in front of the evidence.
Well fuck you and your shitty project. I'll keep using my fucking fork.
And if you're reading this, well, fuck you twice. Moron.10 -
As I was walking to the store, I found yet another piece of evidence of nature rape (aka fucking nature by littering of harmful substances). Just like last time I brought it home for proper disposal.
But if I ever find the motherfucker who did this, I have a nice punishment for you. I'll knock you unconscious, drag you home, take your phone and desolder its battery. Then I'll strap a plastic bag around your stupid face, and put the battery in there while it's being shorted. Quickly it'll heat up and you'll start to turn blue with that little bag being your only oxygen source. And when that battery puffs, boy are you going to fucking gasp it all in. Hopefully that'll be poisonous enough to kill you on the spot. If not, I'll have some fun watching you die from oxygen deprivation. Or I'll jam that very same AA battery that you dropped down your throat - you choose.
Call me a psycho all you want, but what does that make you, whoever attempted to further fuck nature by uncaringly dropping a battery on the sidewalk? Oh and let's not mention the results of it - a heatwave that's been going on for over a month now. Thank you so much for bringing the place that you deserve to be in - hell! rant nature rapists fsociety fuck society uncaring motherfuckers fuck it all fuck humans fuck humanity13
rant nature rapists fsociety fuck society uncaring motherfuckers fuck it all fuck humans fuck humanity13 -
I was fired from a job where the boss had it in for me. He was a really experienced dev, but he was also very arrogant. He hated me questioning him. I didn't have the evidence nor the "political" clout to back up my criticisms.
It was humbling.
I realised two things:
keeping your mouth shut is often the best approach.
And
my own arrogance was keeping me from getting better, from learning new things. Not just for the company, but for myself.
I want to write better code, make better design decisions, utilise design patterns, actually think about what I'm doing, and be able to justify why I'm doing it.
I want to be able to choose the best tools for the job, not the best tools for me.
I want to be a person that is open to criticisms and I want to be someone who is always ready to learn new things.9 -
The gift that keeps on giving... the Custom CMS Of Doom™
I've finally seen enough evidence why PHP has such a bad reputation to the point where even recruiters recommended me to remove my years of PHP experience from the CV.
The completely custom CMS written by company <redacted>'s CEO and his slaves features the following:
- Open for SQL injection attacks
- Remote shell command execution through URL query params
- Page-specific strings in most core PHP files
- Constructors containing hundreds of lines of code (mostly used to initialize the hundreds of properties
- Class methods containing more than 1000 lines of code
- Completely free of namespaces or package managers (uber elite programmers use only the root namespace)
- Random includes in any place imaginable
- Methods containing 1 line: the include of the file which contains the method body
- SQL queries in literally every source file
- The entrypoint script is in the webroot folder where all the code resides
- Access to sensitive folders is "restricted" by robots.txt 🤣🤣🤣🤣
- The CMS has its own crawler which runs by CRONjob and requests ALL HTML links (yes, full content, including videos!) to fill a database of keywords (I found out because the server traffic was >500 GB/month for this small website)
- Hundreds of config settings are literally defined by "define(...)"
- LESS is transpiled into CSS by PHP on requests
- .......
I could go on, but yes, I've seen it all now.12 -
Such immense satisfaction when. You have been telling the other team that the problem is on their end and providing more and more evidence that it is but they insist it's in your end and now finally they are admitting the problem is on their end!
 3
3 -
I know the hate for Facebook is strong here, but I was just approached to work on their eCrimes team... Catching online predators and the like... I'm honestly considering it, given how much evidence is posted. But it requires so much more programming knowledge than I have... I don't know where to start...27
-
Ah... The satisfying feeling when you close a ticket with Not an Issue aka the User is Dumb...
Though it took a long time to get the evidence I needed...3 -
“I don’t mind thinking out of the box, as long as there is evidence of any thinking going on inside it.” — Terry Pratchett4
-
Previous job:
- Every dev needs to connect to a remote server, and do the coding there because the bosses are afraid that we will "steal" their legacy spaghetti written by the CTO in 2006 (the current year was 2016-2017).
- There are no QAs, because "why do you devs need mommy to look after your codes?"
- Bosses think it's our duty to stay extra hours without overtime payment while talking bullshit about a culture that promotes work life balance. You receive no bonus for staying late, but if you leave work 15 minutes early, HR will have a serious talk with you the next day.
- Bosses require "evidence" when you submit a leave request. For example, you tell them you're taking a vacation, they'll ask you for a copy of airline tickets, hotel bookings, etc.
- Bosses spend a ton on hosting parties for the customers while we're using 6-7 year-old laptops
- The CEO loves firing people for ridiculous reasons. Once he considered firing a guy because the way he walks is funny11 -
Me: "Just upload the god damn file you bastard! I got called 5 times today because you couldn't upload this fucking piece of shit!"
Co-Worker: "Relax dude, I got all here on my computer"
Me: "....." (In mind: if you kill him later, you can hide the evidence)9 -
So i've spent the day:
a) Finding evidence (again) of product not doing their job, to send on to one of my managers. So we can again discuss why she's still here.
b) Explaining to my iOS developer that although all the devs are in agreement that 2 of them are not pulling their weight and shouldn't be here ... they will definitely still be here because management actually want to keep our multi-timezone setup as they see it as beneficial. We, do not.
c) Having a meeting with another manager, in a different department. (Backstory, a member of their team has had many complaints filed against them by various members of the building, including one from my team). To let them know that my employee felt like you ignored her concerns and complaints and are going to allow this person pass their probation without considering the implications.
I hope to actually find some time in the reminder of the day to actually achieve something, rather than just telling skidmarks that they are in fact skidmarks.
... but probably won't due to 3 hours of pointless back to back meetings, where we answer the same few questions every week.
I really do love being a tech lead. So refreshing. -
The founder of a company I worked with is convinced that if you're a founder who argues with engineers, you're a bad founder.
He believes that any engineer knows engineering stuff better than any manager. It feels like common sense. Though it's a very rare point of view among managers. He agrees and says that managers only argue with developers because of lack of confidence, megalomania or some other ego issues.
So, all our arguments with him go like this:
— %Foundername%, we should change X, here's why
— Okay, discard existing mockups and go ahead
Or like this:
— %Foundername%, we should change X, here's why
— Kiki, I tried it, here's the evidence that our current stuff works better
— Okay
It's always this two ways and never something like "I'm YoUr SupErIoR sO I'm rIgHt", the stuff I heard in companies I worked for before.5 -
N: Me
M: Mother
M: Can you help me? I can't update pages.
N: Sure *Checks problem* it looks like you installed it with the old apple account, you just need to reinstall it using your new one.
M: What about all my pages documents on icloud?
N: *Compares documents on mac to her other Apple devices that never had the old account* See? The documents would have to be on the new account.
M: Are you sure? I don't want to lose any documents.
N: I know, don't worry their on your new iCloud.
M: *Calls apple support*
N: *Talks to apple support who after an hour of chatting to her through me because I translate customer support to mother confirms what I was telling her*
N: Reinstalls pages and everything is fine.
I was originally going to make a post talking a bit about how people love to second guess anything I say but thought this story provides a decent example. When it's something of a personal nature or someone is asking for my opinion in genral then it's perfectly reasonable to ask multiple people. It doesn't bother me when someone asks for my help, it bugs the shit out of me when someone asks for my help and then doubts everything I say in this case even after providing some evidence to back up my claim and wasting a solid hour. If you ask for my help your trusting that I have the knowledge necessary to assist, if I don't know for certain I'll try googling the problem but even in that case calling support doesn't bother me because I clearly don't know how to help.
P.S. This was my first story, how did I do?7 -
Ok, so when I inherit a Wordpress site I've really stopped expecting anything sane. Examples: evidence that the Wordpress "developer" (that term is used in the loosest sense possible) has thought about his/her code or even evidence that they're not complete idiots who wish to make my life hell going forwards.
Have a look at the screen shot below - this is from the theme footer, so loaded on every page. The screenshot only shows a small part of the file. IT LITERALLY HAS 3696 lines.
Firstly, lets excuse the frankly eye watering if statement to check for the post ID. That made me face palm myself immediately.
The insanity comes for the thousands of lines of JQuery code, duplicated to hell and back that changes the color of various dividers - that are scattered throughout the site.
To make things thousands of times worse, they are ALL HANDED CODED.
Even if JavaScript was the only way I could format these particular elements I certainly wouldn't duplicate the same code for every element. After copy and pasting that JQuery a couple of times and normal developer would think one word, pretty quickly - repetition.
When a good developer notes repetition ways to abstract crap away is the first thought that comes to mind.
Hell, when I was first learning to code god knows how long ago I always used functions to avoid repetition.
In this case, with a few seconds though this "developer" could have created a single JQuery handler and use data attributes within the HTML. Hell, as bad as that is, it's better than the monstrosity I'm looking at now.
I'm aware Wordpress is associated with bad developers due to it's low barrier to entry, but this site is something else.
The scary thing is that I know the agency that produced this. They are very large, use Wordpress exclusively and have some stupidly huge clients that would be know nationally.
Wordpress truly does attract some of the most awful "developers" and deserves it's reputation.
If you're a good developer and use Wordpress I feel sorry for you, as you're in small numbers from my experience.
Rant over, have vented a bit and feel better. Thanks Devrant. 6
6 -
There's this guy who randomly make sexual remarks. Not the usual guy's talk kind sexual remarks, but more of "I am going to rape this girl infront of her boyfriend and her father " kind of remark. Also he sexual harassed women coworker like take video of them in the toilet.
What we did was gathering every rape case possible (which is not related to him, but somehow the victims don't know who the rapists were) , all the evidence of him taking nude video of girls and report to police . We launch the statement that "maybe" the rapist was this phallus.
And the authorities got his arse and tracked. Well he asked for it.
Always remember "with great power of boasting bullshit, comes with a fat shit of consequences". The difference between the actual Spiderman and this phallus is that Spiderman think with his senses and shoot webbings from his wrist, but this phallus don't have any actual thought involve and shoot webbings from his micropenis.
I resigned after that.15 -
Just read this in a blog post by Jon Arundel, I think he's spot on:
"Programmers are incurable optimists: we always think our code will work, despite much evidence to the contrary."6 -
Help?
I work in support and some of the developers here don't seem to realize that their customers can't use the app they wrote because of all the bugs, but they freak out if anyone so much as *thinks* there's a problem with the code.
We have evidence it's their code. How do I get them to see I'm not saying their code sucks, just that a few changes might help performance?
I don't want to insult them, but at the same time, they're only responsible for one application...15 -
There are still old youtube comments from my younger self to be found on youtube. Delete every evidence!2
-
Managed to make myself look like a fucking moron again today...
Can't mount NFS share, get "permission denied". Huh, that's weird... It's correctly exported.
Well it's correctly exported and rpcinfo -p $HOST times out... Must be firewall rule.
Firewall rule is changed but still no joy "permission denied"... Fuck sake networks, can't you do anything right first time?!!!
Firewall rule is correct I am reliably informed... Go about proving that it's not fucking correct and provide "evidence" to show this, I was a little bit more blunt than was strictly required.
Networks say they will take another look.
I turn NFS logging to verbose for my own interest and notice the line "path/to/directory is not a valid directory".
I, as a moron, had missed a "/" at the start of the path. That's why I still couldn't mount after the firewall change.
Go over and apologise in person and explain how I'm a total idiot. -
Being railroaded by a colleague and accused of project sabotage, then having to submit to a 2 hour interrogation where I was literally sat in a corner and read a riot act. I had done nothing of which I was being accused. I sic'ed HR on them in a followup meeting but all HR did was sit and listen and then find in their favor despite the written evidence because my manager outranked the HR manager. That was when I learned that employees are always wrong when the manager wants them to be. I freelance now. No manager, and I can fire my clients.
-
YouTube just deleted my favorites playlist for supposed hate speech. My playlist had like 4k vids in it (none of them uploaded by me) and most of them were just stupid music videos or whatever, nothing even comes to mind that would qualify as hate speech, so because of this alleged needle in a 4k video haystack my playlist got deleted, YouTube did not even show any evidence of the supposed hate speech content within, my appeal was denied instantly. This is why I hate big tech- it is tyrannical and bullshit. It serves as an extra government nanny rather than appealing to its user base. This is because once a social platform grows so large that it has the monopoly on users, it no longer has to appeal to its users, it can then just focus on politics or other agendas. They can do this with confidence that they will not lose their users because they know that the modern internet narcissist will flock to any app that gives them the biggest audience, and since they have the monopoly on users they can rest assured the common narcissist will flock to their app (no matter how shitty or tyrannical) because they’ll get the most exposure there. This is the pattern every big social media platform falls into. At one point YouTube was cool….10
-
So I finally got my senior project approved by my school's assistant principal (the one who deals with every student's project) and he said that the three forms of evidence I suggested were not enough. A quick summary of my project: I'm supposed to make a game engine in Java before April of 2017. Every student needs 3 forms of evidence that they did the project so I suggested screenshots of my work, the finished source code, and pictures of me actually working on it. In addition to all of that I would have a ton of documentation and sample projects to test different features of the engine. Well, he doesn't really understand that for a high school student, that's already enough work for a couple of years and thinks I need more evidence. So what does he do?
He requires me to find at least 5 people to test the engine and complete a survey about it. This normally wouldn't be a problem, except I'm a high school student and don't know more than 2 people who are fluent enough in Java to work on a game. And, I have to finish the project before January now to give the people enough time to work with it.
Long story short, I'm not even out of high school and I'm already experiencing the struggles of dealing with non-technical people.10 -
Fuck sake, so my bank has been migrating/rolling out new IT system and app/site have been broken for about a week (others noted evidence of devs debugging in production)
Assuming I don't lose my money as some mischievous assholes will inevitably exploit the fuck up, and rob the bank, I will be moving my funds to a different bank...
In mean time I'm trying to prepare for uni, and they're making a ton of semi-random changes in addition to rolling out a site with course details and info along those line, and good fucking god is it bad.
Is is slow as fuck? Check. Does it use never-seen-before naming for standard things? Check! Is the UI pulled from late 90's? YOOU BETCHA! Are the pages bloated with unnecessary content? Fuck yeah! Do I get SQL exceptions when I finally locate my course? Of course I do. Does clicking "back" take me back to the landing page instead of previous page, when I'm several steps deep? .....
I could keep going, but don't feel like ranting and feel more like punching someone in the throat.repeatedly. -
I'm managed by idiots who don't fully realize the nightmare they're creating.
They're making small operational changes, but hundreds of them with zero evidence to back their claims up.
When I bring up how it actually works, and how operations actually work I'm told I don't use the tools as much as management does and that my feedback is limited to how I use the tool.
So now I'm just gambling that they won't fuck up too bad before I get that sweet sweet sellout money and just letting them fuck everything up they want without any warnings from me.
I'm quickly learning that the phrase of the year is, "Fuck em". -
Still dealing with the web department and their finger pointing after several thousand errors logged.
SeniorWebDev: “Looks like there were 250 database timeout errors at 11:02AM. DBAs might want to take a look.”
I look at the actual exceptions being logged (bulk of the over 1,600 logged errors)..
“Object reference not set to an instance of an object.”
Then I looked the email timestamp…11:00AM. We received the email notification *before* the database timeout errors occurred.
I gather some facts…when the exceptions started, when they ended, and used the stack trace to find the code not checking for null (maybe 10 minutes of junior dev detective work). Send the data to the ‘powers that be’ and carried on with my daily tasks.
I attached what I found (not the actual code, it was changed to protect the innocent)
Couple of hours later another WebDev replied…
WebDev: “These errors look like a database connectivity issue between the web site and the saleitem data service. Appears the logging framework doesn’t allow us to log any information about the database connection.”
FRACK!!...that Fracking lying piece of frack! Our team is responsible for the logging framework. I was typing up my response (having to calm down) then about a minute later the head DBA replies …
DBA: “Do you have any evidence of this? Our logs show no connectivity issues. The logging framework does have the ability to log an extensive amount of data regarding the database transaction. Database name, server, login, command text, and parameter values. Everything we need to troubleshoot. This is the link to the documentation …. If you implement the one line of code to gather the data, it will go a long way in helping us debug performance and connectivity issue. Thank you.”
DBA sends me a skype message “You’re welcome :)”
Ahh..nice to see someone else fed up with their lying bull...stuff.
-
Had to bring up some issues with my instructor to the school, and forgot to print out emails hosted on their Exchange server that show the issue in detail. When I logged in, every email had mysteriously disappeared from my account, but because I document everything about this horseshit school locally, I could still show the exported emails.
The instructor?
Head of IT.
The bastard tried to hide the evidence, but fuck him, Document Everything. -
Disclaimer: I apologise in advance for those tired of language wars, if it bugs you that much just skip this rant.
"C++ is better than C"
An accepted truth. OO is better than Procedural, C++ is an upgrade from C, it fixed all the problems.
End of.
Except - when it comes to actual evidence, empirical studies have shown that there are no productivity gains with C++ vs C.
This bugs me the most because it's such a fringe view, OO has dominated industry purely by dogma, alternative programming paradigms are just simply ignored because: "OO is best. End of."
https://researchgate.net/profile/...22 -
Watching a piece (a Belgian TV series) about hackers
- Police IT dpt takes a burned down computer (literally burned down -- black from the smoke), plug it into the mains and remove a graphics card. To collect evidence from.
- A policeman from IT dpt is browsing some company's website (while at the police station), looking at their clients. Address bar says: 127.0.0.1.
- The police hacker is browsing some forum. She got the post author's IP and MAC addresses from that forum post metainfo.
<img src="awkward.jpeg" alt="Awkward...">
<img src="confused_jackie.jpeg" alt="Awkward..."> 19
19 -
Stages of being a self-taught developer.
first: you think you have taught yourself enough to apply for a job.
second: A Company actually believes you. Evidence? They hire you.
Third: You realize you don't know anything.Evidence?
Me in my head
I thought I was good at this. I don't know anything. I should probably switch back to nutrition(my previous job).Why am I struggling with this? Who even struggles this much with APIs??6 -
Exclude Apple from any web standard influence in the future. They clearly don’t give a fuck about the web from the evidence of them purposefully downgrading their PWA features just because they are salty that the EU forced them to allow other non-WebKit browsers on iOS. What a bunch of pieces of shit. Fuck Apple for being a fucking corporate spoiled child.10
-
Dumbass... I tell him what the problem is and show him the evidence...
But after a week they investigating a diff thing or basically have no idea wtf his looking at....
I should just stop checking work emails while on vacation... Just let idiots screw themselves and see how badly they wander off course and where they end up -
Startup-ing 101, from Fitbit:
- spy on users
- sell data
- cut production costs
- mutilate people's bodies, leaving burn scars that will never heal
- announce the recall, get PR, and make the refund process impossibly convoluted
- never give actual refunds
- claim that yes, fitbit catches fire, but only the old discontinued device, just to mess with search results and make the actual info (that all devices catch fire) hard to find
- try hard to obtain the devices in question, so people who suffered have no evidence
- give bogus word salad replies to the press
This is what one of the people burned has to say:
"I do not have feeling in parts of my wrist due to nerve damage and I will have a large scar that will be with me the rest of my life. This was a traumatic experience and I hope no one else has to go through it. So, if you own a Fitbit, please reconsider using it."
Ladies and gentlemen, cringefest starts. One of fitbit replies:
"Fitbit products are designed and produced in accordance with strict standards and undergo extensive internal and external testing to ensure the safety of our users. Based on our internal and independent third party testing and analysis, we do not believe this type of injury could occur from normal use. We are committed to conducting a full investigation. With Google's resources and global platform, Fitbit will be able to accelerate innovation in the wearables category, scale faster, and make health even more accessible to everyone. I could not be more excited for what lies ahead".
In the future, corporate speech will be autogenerated.
(if you wear fitbit, just be aware of this.) 13
13 -
It feels like this piece of code tells a story. Something about lingerie models, a wild night and frantically trying to get rid of any evidence.

-
Fuck, give it maybe a decade more and we'll have the deepfakes drama, but on a whole another level, haven't seen as much development in countering all those technologies yet either (the only recent one has been iirc trying to feed a neural network with fake video, to try to spot small details, but that hasn't seen much success, even with deepfakes)
most terrifying application would be to imitate e.g. a president and send that to another country as a threat and vice versa or to fake video footage as evidence, admittedly both very low chance, but still a possibility, seeing how e.g. some court cases have been based almost exclusively around video footage or how north-korea treats any outside media.
https://youtube.com/watch/... 4
4 -
Disclaimer: I hold no grudges or prejudices toward [CENSORED] company. I love the concept of the business model and the perks they pay their employees. Unfortunately, the company is very petty, and negligence is the core of the management. I got into an interview for the position, of Senior Software Engineer, and the interview wouldn't take place if wasn't for me to follow up with the person in charge countless times a day. The Vice President of Engineering was the most confused person ever encountered. Instead of asking challenging questions that plausibly could explain and portray how well I can manage a team, the methodology of working with various technology, and my problem-solving skills. They asked me questions that possibly indicated they don't even know what they need or questions that can easily get from a Google Search. I was given 40 hours to build a demo application whereby I had to send them a copy of the source code and the binary file. The person who contacted me don't even bother with what I told her that it is not a good practice to place the binary in cloud storage (Google Drive, OneDrive, etc) and I request extra time to complete the demo application. Since I got the requirement to hand them the repository of the codebase, it is common practice to place the binary in the release section in the Git Platform (Jire, Azure DevOps, Github, Gitlab, etc). Which he surprisingly doesn't know what that is. There's the API key I place locally in .env hidden from the codebase (it's not good practice to place credentials in the codebase), I got a request that not only subscript to an API is necessary but I have to place them in the codebase. I succeed to pass the source code on time with the quality of 40 hours, I told him that I could have done it better, clearer and cleaner if I was given more grace of time. (Because they are not the only company asking me to write a demo application prior to the assessment. Extra grace was I needed)
So long story short, I asked him how is it working in a [CENSORED] company during my turn to ask questions. I got told that the "environment is friendly, diverse". But with utmost curiosity, I contacted several former employees (Software Engineer) on LinkedIn, and I got told that the company has high turnover, despises diversity the nepotism is intense. Most of the favours are done based on how well you create an illusion of you working for them and being close to the upper management. I request shreds of evidence from those former employees to substantiate what they told me. Seeing the pieces of evidence of how they manage the projects, their method of communication, and how biased the upper management actually is led me to withdraw from continuing my application. Honestly, I wouldn't want to work for a company where the majority can't communicate. -
Seriously, fuck Discord's new community guidelines! They now think they even own you outside of ther shady app:
"We may consider relevant off-platform behavior when assessing for violations of specific Community Guidelines."
Addressing harmful off-plattform behavior:
https://discord.com/blog/...
"When we talk about off-platform behaviors, we’re referring to any behaviors taking place outside of Discord, either in other digital spaces or in a physical community. If we become aware of specific off-platform, high-harm behaviors with credible evidence committed by a person with a Discord account, we will take the off-platform harmful behavior into consideration when assessing whether that account has violated a specific Community Guideline."
"We are applying this off-platform behavior consideration only if we become aware of highest-harm threats, including using Discord for organizing, promoting, or supporting violent extremism; making threats of violence; and sexualizing children in any way."
Yeah, suure...
Why does every fucking internet company think that they own their users?11 -
I would like to present new super API which I have "pleasure" to work with. Documentation (very poor written in *.docx without list of contents) says that communication is json <-> json which is not entirely true. I have to post request as x-www-form with one field which contains data encoded as json.
Response is json but they set Content-Type header as text/html and Postman didn't prettify body by default...
I'm attaching screenshot as a evidence.
I can't understand why people don't use frameworks and making other lives harder :-/ 3
3 -
Another fun thing. This morning one of the first mails i read was a issue about a bug in our software.
This was a bug i mentioned months ago but there was nog evidence where i searched like mails chats or tickets.
If people would just listen to me this bug was solved months ago but back then i got a reaction like: "works over here" while i tested it on two different instances with buggy results each time. -
If I have to change my domain password every 3 months for a bullshit out of date security policy (there's plenty of evidence suggesting that changing passwords is actually worse security), then maybe, just FUCKING maybe, make sure that that password change appropriately filters down to things like SQL Server so I can keep doing my goddamn work.7
-
Right now. It's happening. I'm sitting on one of those seemingly impossible issues. I'm reading the exception and can't fathom how it can be true. I mean, the evidence is right there! The error message must be wrong! But that's the thing, it never is. It's always something stupid and obvious. After you figure it out, you shake your head and laugh at yourself for not seeing it. It's all shits and giggles after you figure it out, but that's not where I'm at right now. Right now I'm being laughed at by this stack trace. It's mocking me even!
Jokes on you though, because I'm coming for you!!2 -
FUCKING CHINESE SUPOSED IP CAMERAS...
First, they aren't Ip cameras, they are p2p cameras with different settings and more limited...
then took me 3 days to open 5 ports for 2 cameras, config the cameras, till they work.
YEY they finally work, can see them over the Internet (no default settings, even changed the Alias), have my Ip camera viewer on the Phone... but one doesn't activate on moviment.. in this 3 days only took 2 pictures with motion detection on and people passing in front of them... the other was working for like 5 minutes... giving black and white 7kb jpgs... after a few teeks... can't make it work again.
Now I have two cameras that I can see if my house is being robbed but no motion detection to warm me, or at least save some pictures on the server to serve as evidence (and maby finally get the team that is robbing one house a day, If they try to rob my house again...).
The cameras are very good as baby monitors or to play around, for 14$ and 20$... (love the 360º ball) , but as security cameras... Unless you have them connected to a security station and with a repeater close by... worthless...
Oh, and they may give me 1 good frame a second or lag to 10+seconds a frame...6 -
It's not so much that I mind all the fire-war about best languages, editors, and other shit, it's that NO ONE PROVIDES ANY GODDAMN EVIDENCE OR ARGUMENT ABOUT WHY. Come on folks, everyone here is on the higher end of the IQ curve, FFS make an argument!!10
-
so here’s the tea.
i’m a Chinese dev working in a Japanese company. they’ve got this decently sized project a full web app and backend stack and yeah, I’m handling both ends. full-stack life. not a problem. I’ve seen worse.
but the maturity level in this place? the passive-aggressiveness? is different level. have you ever worked somewhere where your coworkers act all sweet on the surface, but lowkey make it feel like everything is your fault in the most obvious way possible?
so here comes the fun part.
the Stripe exchange rate endpoint we were using? deprecated. not globally — just regionally in Japan.
i did my homework. contacted Stripe support. got the chats, screenshots, docs, confirmations, evidence, not .........vibes.
solution? easy. i integrated a third-party API that returns the same exchange rate data. built a cron job to pull and cache the values daily. stored it locally. frontend grabs the user’s currency via IP, backend returns the rate, no stress, no wasted API calls. boom. problem solved.
my manager? totally got it. said it was efficient.
but the founder? man acted like a toddler.
he flipped. said it was my fault.
told me i just "no communicate well...uh...very confuse..." like bro… what even? do I look like I own stripe or do I look like I secretly working for them? plus, i explain in full, still not understand.
he got heated in meeting, so I clapped back in the meeting: you want to argue all day and get nothing done? or you want to understand what’s going on, and let me go back to building stuff that actually works? pick one.
he didn’t like that.
pretty sure he’s shopping for my replacement now. well, doesn’t take a genius to see it.
but I’m not here to babysit egos. I’ll do my job clean, document everything, and keep it professional. meanwhile yeah, I’ve already started looking for something else.11 -
holy fuck, UFOs are now moving to the "mainstream discourse"?????
yes, just like AI, world's ending, all the jobs are gone!!!
just like covid (remember that one?) world's over, we all died!
let me repeat it for you:
shut the fuck up
shut the fuck up
shut the fuck up
what the fuck went wrong with the vast majority of people along the way????
i'm going to the mountains, i'll be back...
never
inb4 "have some creativity fullstackclown!" "isn't it cool to think about?!"
shut up, using your fucking head that is a result of millions of years of evolution seems much more exciting than taking 4 grainy ass videos as truth and getting hyped up about it
show me a shred of valid evidence and i'll believe. however, evidence does NOT include:
- some big wig CLAIMING or SAYING they exist, regardless of their credentials - i don't care if fucking honest abe lincoln himself rises from the grave and says UFOs are real
- a photo or video that looks like it was taken in the 1920s 6
6 -
What paradoxes taught me.
Perhaps each time a paradox is encountered in mathematics, there is a useful distinction or mathematical tool hiding in plain sight, one that hasn't be discovered or utilized. For cursory evidence I give you: division by zero, the speed of an arrow at any point in flight, and calculus.
Maybe this isn't true for some paradoxes, or even most, but as time goes on I suspect people will discover it is more true than they might have thought.
Undefined behavior and results aren't nonsense: They look to me like golden seams to be explored for possible utility when approached from uncommon angles with uncommon problems.6 -
So I was rejected by the management today for promotion to Senior 2 although I have done several major feature developments + infra design and basically end to end ownership.
Reason for no promotion? That's the best fucking part, according to the feedback, the work I performed on the service I created is well-designed,
and the code quality is commendable. However, they pointed out a notable difference in code quality between the micro-service
I built and the rest of the project developed by others. This, apparently, suggests that I lack a strong sense of ownership over the broader product.
First of all, we have super tight deadlines (almost 996), and I burned midnight oil to make sure the service I am in-charge of is designed really well.
Also, how in the flying fuck the other how the inability of others to maintain good code quality elsewhere in the product is being used as evidence against my sense of ownership
and initiative in ensuring high engineering quality for the repository I wasn't even working on
What a delusional management, the entire feedback feels like just an excuse to fuck off, we are not promoting you...
May be instead of doing actual engineering work, I should have just do minimal work and write more design docs / technical artifacts
It is very demoralizing after I worked hard for so many months, product went out really well.. yet when performance review comes, rejected with a petty reason7 -
If you want to improve your life, but your mental health and energy levels are too low to exercise, start with hygiene.
Take showers every day, continuously lowering the water temperature. Use dental floss and tongue scraper. Brush your teeth twice a day. Wash your face every morning and every evening. Use evidence-based skincare products: adapalene, panthenol, SPF 50+ sunscreen. Keep your toes and nails tidy. Shave routinely.
According to Nadya Tolokonnikova, a prominent Russian dissident who was imprisoned, denying basic hygiene is a _very_ efficient way of breaking someone into submission that is often applied to dissidents in Russian prisons. So, doing a reverse of that should improve mental health. -
!rant
Digging though my old emails found this joke sent to me long time ago. Think that originally was posted in a 1997 issue of Computerworld. Maybe you already suffered the effect of the "Opcodes" listed here. Hope that !tl;dr
ARG Agree to Run Garbage
BDM Branch and Destroy Memory
CMN Convert to Mayan Numerals
DDS Damage Disk and Stop
EMR Emit Microwave Radiation
ETO Emulate Toaster Oven
FSE Fake Serious Error
GSI Garble Subsequent Instructions
GQS Go Quarter Speed
HEM Hide Evidence of Malfunction
IDD Inhale Dust and Die
IKI Ignore Keyboard Input
IMU Irradiate and Mutate User
JPF Jam Paper Feed
JUM Jeer at Users Mistake
KFP Kindle Fire in Printer
LNM Launch Nuclear Missiles
MAW Make Aggravating Whine
NNI Neglect Next Instruction
OBU Overheat and Burn if Unattended
PNG Pass Noxious Gas
QWF Quit Working Forever
QVC Question Valid Command
RWD Read Wrong Device
SCE Simulate Correct Execution
SDJ Send Data to Japan
TTC Tangle Tape and Crash
UBC Use Bad Chip
VDP Violate Design Parameters
VMB Verify and Make Bad
WAF Warn After Fact
XID eXchange Instruction with Data
YII Yield to Irresistible Impulse
ZAM Zero All Memory -
Long story short I joined this company as a junior after 1.5 years of a break from development. Before that I worked for almost 3 years in the required stack. We agreed that if I do well after 3 months probation period I can ask for a raise.
It turned out that Im doing better than half of my team so 1 week before probation was about to end, I put in my raise request. Got nothing but strong feedback, even managed to burn myself out a couple times.
Now since the request 11 weeks passed. Our HQ which has the final say about the raise is overseas. Im getting excuses about summer: allegedly because of summer some people in the appproval chain have vacations so this process is taking a long time. This is the excuse they are giving to me.
Right now Im getting really pissed off and resentful because this drag is becoming unnacceptable. Also being in a new scrum team filled with total juniors complicates everything a lot. Im not having the best time here. But at the same time I dont have any savings actually am in debts and currenty barely am able to survive paycheck to paycheck to I cant just quit on the spot.
Had I known that they will drag this out that much, I would have applied to other places and presented them a counter offer. Or at least bluffed from the start in order to speed the raise proccess up.
Should I give ultimatum to my manager?
Im hesitant to do that because up until now we had a decent relationship and he seems like a nice guy so I dont want to rock the boat.
Or should I bluff about having a counter offer, so he would speed things up? But what happens if he asks me to forward him evidence of my received offer?3 -
The code of conduct is a good thing. It doesn't persecute cis white men. All it does is tell you not to harass people on the basis of traits they cannot control. You say you only care about code quality and nothing else? There's a whole untapped market of talent from women and lgbtq+ people who stay the fuck away because of toxic communities. When you call people faggot it makes them not want to contribute to your codebase.
Linus stepped down of his own volition to try to become a more constructive voice. Heaven forbid the assholes have some introspection.
Hate it because it's vague. Hate it because it means anyone can be banned without evidence. Don't hate it because the assholes are finally being called on their bullshit.11 -
I love cats more than dogs.
Despite being domesticated, cats remain true predators with true predator skills and the pedigree that comes with them. The evidence is your local government mandating house cats should wear bell collars to warn birds, as they threaten their extinction otherwise.
Modern dogs are mere scavengers that live off people and eat trash. They evolved to be cute by tilting their heads. Dogs aren't useless, mind you, I just like cats more.
But both dogs and cats are dwarfed by YE MIGHTY FROGGE. Frogs are the most fascinating and magnificent creatures to ever roam this troubled planet, maybe rivaled only by orcas. Frogs are the best. They're also the cutest, especially when touching a small yellow one can kill an elephant.10 -
Pissed off as fuck. The more I explain to people that they have to provide at least one piece of evidence in order to analyze the problem, the more they end up saying "the app doesn't work".3
-
when your client reports that there is bug but they cant explain, describe, replicate or give evidence of. Just 'there is a bug' 😐
-
So related to my previous rant about monkeys:
https://devrant.io/rants/596563/...
I happened to come across an old PPTX I made for our company's "new goal" (~4 years old) for Engineering Excellence. (I was searching my PC for old evidence to resolve a dispute with health care provider... staffed by monkeys... that keeps billing me for random amounts even though I paid the correct amounts... 3 years ago)
https://drive.google.com/open/...
Thoughts?3 -
I received the following e-mail today:
Hey, XYZ! Could you please check the following in your web application. The data do not show correctly. Could it be a bug?
[insert attached screenshot with said "bug"]
My reply:
Hey, ABC! It is not a bug. You uploaded the data into the wrong table. 😊
[insert attached screenshot with the incriminating evidence]
-----------------------------
I felt a bit savage and I liked it. 🔥4 -
WTF?
TL;DR Integration between software failed so hard I lost 20% of my progress in one hit. Yay! /s
I, being a Fool, signed up to do NaNoWriMo this year (50k words in 30 days of November). I've won it before, and failed it before, and this year was especially stupid as I've got a bigger pile on my plate than usual, what with getting as quickly up to speed on c# and React as I can in prep for starting the new job in December.
I started on a high - 4k on day one, woohoo! To my delight, my writing software Scrivener now had an integration feature to let you update your total word count straight to your account instead of manually entering it. I added my credentials, hit the button, refreshed the page, all updated. So far so good.
Then, on day two, I wrote 1700-ish words. Still good, well ahead of target, took me over 5k. Updated through Scrivener, checked it updated the site, still good.
Then, yesterday, I logged in and added a tiny tiny number of words (brain went blah), and was horrified to discover it had taken 1900 words off my count!
Cue panic as I frantically searched for the missing words, trying to find any evidence of where they'd gone. Gave up after half an hour of futility, bashed out enough to squeak back over 5k, confirmed it had updated.
I'm not unfamiliar with the general stupidity most organisations have on integration - they don't have it, or it's an afterthought, or it's just plain terrible - but this was a ridiculously simple thing to do, I'd have thought? Passing one fucking number and some date/time tracking?
This is what I get for trying to do too many things at once, I guess! -
Maybe a repost but interesting no? (got into an discussion with a friend, needed evidence)
https://bloomberg.com/graphics/... 1
1 -
Joel Spolsky wrote a great article about estimating the time it will take for dev work: https://joelonsoftware.com/2007/10/...1
-
When your routine security testing causes your work laptop to be seized and held for evidence indefinitely because security operations think it's a rogue laptop.
-
That feeling when you spend a week evaluating IDE software, providing lots of critical evidence as to a clear winner, and the company refuses to spend any money to improve the tools.1
-
!rant Scary Stuff...
Not sure what are the rules on sharing external content, but this story freaked me out and I wanted to share with you.
Pretty scary stuff, maybe something like this is already in the wild? Especially with the NSA and other power groups trying to exploit vulnerabilities and infiltrate everything...
Found it originally on the rational subreddit. Here is the link:
https://teamten.com/lawrence/...
Spoiler alert:
It's about the The Ken Thompson Hack:
"Ken describes how he injected a virus into a compiler. Not only did his compiler know it was compiling the login function and inject a backdoor, but it also knew when it was compiling itself and injected the backdoor generator into the compiler it was creating. The source code for the compiler thereafter contains no evidence of either virus."
How to detect/deal with something like this? better no to think too much about this. -
If you ask any sane person "hey, do you want to get some disease with fever, headache and potential risk of dying?", I doubt anyone will say "yes".
But if there exist a way to prevent it with a proven efficacy from both evidence-based medicine and science, why not get it today? I'm not even talking about covid. Why people are not getting their flu shots? How's that logic works? You mean you don't want disease, but you also don't want to take any measures to prevent it?
Every time in late autumn people get cold. For a sane person, one such case with themselves is enough to say "hey, I don't want this to happen again the next autumn". Yet people do nothing.
I can't understand this.
And this is only a flu. Hepatitis will destroy your liver and potentially will destroy your whole life, so why avoid vaccination?6 -
Just got on a fb argument because I said something along the lines of: mfkers that throw the finger in a pic are the same mfkers that will quickly disappear from a fight
Yo, if your ass is though enough, then it is. Flipping the bird at a pic makes me think you're willing to throw hands if needed be.
Anecdotal evidence proves it ain't real3 -
I saw people today who collected some evidence related to a cs:go pro hacking. The people found "him" on a gamehacking website where his location was put as "queue.back()" -> they claimed it to be Montreal, Quebec. Sigh.
-
I'm not a Wordpress pro, but i've done some work on it and... well, the HTML + PHP mix is the only evidence you need to convince someone, there is no god, only satan, but other then that, it's hard to find anything else that your clients will accept & can use. And yes it's the most important thing - at the end of day, they are the one giving you money.
Besides:
- the Wordpress dev community is pretty cool.
- everything has been invented, so the development is pretty easy.
- if you have something more fancy to do, there is always a Wordpress API.
PS - fuck HTML + PHP mix.1 -
Has anyone actually ever seen evidence of SOLID principles being 100% adhered to, as opposed to people just saying they're using them correctly then you look at their code and they're clearly not.
I can count more than one responsibility here...1 -
Anyone else remember at googles summer of code in 2006-ish google catching heat for hiring strippers to give the male devs lap dances ?
those were they days ! I wanted to work for google so much after that.
we need to bring the debauchery into development lol
notably, google has erased all evidence of that new story now that they have become staffed baby raping, tree hugging, snarky fucking homosexual clowns.
and btw i am an environmentalist and I don';t care if someone is actually gay. I'm also practical and like boobs. unfortunately i don't think thats whats working at google.31 -
Had a dream that some trans girl fell in love with me here on devRant, then sending a picture with abstract schizo graffiti with my name to me
I woke up in search of evidence. Went through my phone, didn’t find where to look to see my browser history. Then, every button in the bottom bar were replaced with small 32x32 px ad. That’s when I knew it was a dream too, a dream within dream
Woke up again. Was teleported to a huge liminal water park that is also a mall, and then I was like wait, it’s a part of kikiverse, so it must be yet another dream layer
Woke up again. Typing this. See ya7 -
So I guess this doesn't really fall under dev, more web and net admin, but here it goes.
I am trying frantically to migrate our (@Gerrymandered and I) website from a hosted solution with Namecheap to my new personal badass server, Vector. The issue is that I need to host multiple subdomains under one IP. I learned how to use apache2's VirtualHost feature, and eventually made them all work. But now we need to get our 3 year SSL Certs that we already paid for working. Try to get ssl pass through... Nope. Fine, just use the VHost then forward it unsecured to the local ip which only accepts connections from the Apache host. But wait! I want to access my ESXi config page remotely too! Good GOD it is a pain in the ass to get all of this working, but I somehow did. Evidence is at https://git.infiniit.co, which is hosted on the same network as the ESXi control panel. *Sigh of relief* now I can sleep right? 😥29 -
WE: javaagent-based monitoring, as seen in this screenshot <attached>, is reporting full old-gen, full young-gen, full one of the survivors and a sky-rocketing full GC right before the service outage.
WE: container monitoring in this screenshot <attached> shows that the application peaked its memory very suddenly to MAX values and platoed on that. Then container monitoring is blank, suggesting a complete outage of a few minutes. After that monitoring starts again with memory usage reported at low levels and immediatelly spiking back to MAX again, suggesting the container crashed and had been respawned by an orchestrator. This repeats a few times throughout the day.
they: I did not find any evidence of application running out of memory. Maybe our monitoring is not working correctly?
we: *considering updating our resumes* -
Lol if Google keeps at this they'll end up introducing trade house style record keeping policies to the IT industry.
https://ia601707.us.archive.org/28/...
[PDF, plaintiffs' response regarding Google's destruction of evidence]
I can't believe that Epic Games is being the voice of the people, but here we are.5 -
Time estimation of software development should be a product of observation of historical evidence, and many factors that come with it, like:
- What was the language used?
- How many developers worked on it
- How many years each developer has in experience in programming?
- IQ of each developer
- How many kids they have
- The weather
- ...etc
Analyzed by data scientist.
TL;DR
Not something you get by asking developers and interrupting their work, because many are people with superior complexity who often overestimate their capability of solving given problems.
Don't trust them to estimate!4 -
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
Things I say to my clients when I know that a reboot is required to fix their issue but I don't have enough evidence to prove it to them :
"... On any computing platform, we noted that the only solution to infinite loops (and similar behaviors) under cooperative preemption is to reboot the machine. While you may scoff at this hack, researchers have shown that reboot (or in general, starting over some piece of software) can be a hugely useful tool in building robust systems.
Specifically, reboot is useful because it moves software back to a known and likely more tested state. Reboots also reclaim stale or leaked resources (e.g., memory) which may otherwise be hard to handle. Finally, reboots are easy to automate. For all of these reasons, it is not uncommon in large-scale cluster Internet services for system management software to periodically reboot sets of machines in order to reset them and thus obtain the advantages listed above.
Thus, when you indeed perform a reboot, you are not just enacting some ugly hack. Rather, you are using a time-tested approach to improving the behavior of a computer system."
😎1 -
HIRE EXCEPTIONAL SPY SERVICE WITH WEB BAILIFF CONTRACTOR
I thought my husband was having an affair last month. Late nights, secretive texting—something was off. I have a friend who told me to try Web Bailiff Contractor, so I had them penetrate his virtual world. I wasn't prepared for what they discovered.They were quick and discreet. They hacked into his phone with their expertise and recovered deleted text messages. I had evidence within days: flirting chats and clandestine meetings with someone else, He'd been funding his affair with our savings, hoping I'd never find out. Web Bailiff Contractor traced it and sent screenshots that allowed for no doubt.It was hard to confront him, but their findings provided me with insight and strength. They not only revealed the truth—they enabled me to get my peace back. I'm already suggesting Web Bailiff Contractor to everyone who requires answers. Cheating or online enigmas, they're experts at revealing what's behind the curtain. Affordable, discreet, and geniuses—I owe them a tremendous amount of gratitude. Trust them to show you what matters most to you!6 -
"Programs implemented while high contain more bugs and take longer to write (p < 0.05) --- a small to medium effect (0.22 ≤ d ≤ 0.44). We also did not find any evidence that high programmers generate more divergent solutions." He et al. at ICSE 2024.5
-
I wonder if crypto exchanges are so damn vulnerable or just so transparent.
I mean, it is impossible to scroll tech articles for more than a few seconds before stumbling on a report of yet another crypto exchange being nicked a couple hundred mil USD.
- It could be that their security severely sucks (wouldn't blame them for it, most businesses do suck at securing shit).
- It could be that the entire black hat community is putting it's might on stealing money that is so fucking easy to launder.
- It could be that is damn nigh impossible to cover up a crypto hack since the evidence of coins drifting away is forever on display in the public ledger, and in that case crypto companies are not hacked more often than regular companies, they are just much more often publically shamed for it.
- It could be a mix of all the above, but my intuition is that one factor is more relevant.
Which would be the most relevant factor? One of the above or yet another attack vector to the stupidest value conduit ever?5 -
I mean where do I even begin
I am trying to fix up some really awful sloppy mistakes but since we only use svn and I don't have any sort of branch of my own I end up breaking other peoples builds while I try to fix their mistakes
And then I get yelled at and told to test the build somehow on their environment which is totally seperate to ours, and ensure there are no build problems
Even if said problems are svn conflicts they are apparently still my fault and evidence as failure on my part as a developer
I mean how do i even retort to that? Can I tell them to get stuffed, like seriously.. I have asked and checked in if there was any issues and they said nothing repeatedly
I have proposed the idea of a integration environment to test the commits of revisions and merging ect.
I got told off
For gods sakes2 -
How GrayHat Hacks Helps Victims of Cheating Spouses
In today’s world, where secrets can hide in encrypted messages or private chats, suspecting a partner of infidelity can be emotionally devastating. GrayHat Hacks Contractor has become a beacon of clarity for those seeking answers, offering advanced digital investigation services to uncover evidence of cheating. Their work, detailed on their official website GrayHat Hacks Blog, helps clients find closure by revealing the truth, though it comes with ethical and legal considerations.
GrayHat Hacks Contractor specializes in digital investigations, with a focus on services like "Spying on Cheating Spouses." This involves hacking into social media accounts, emails, and other digital platforms to retrieve evidence of infidelity. Based in Charleston, SC, their team combines technical expertise with discretion, ensuring clients receive undeniable proof without alerting the target. While their website also lists cyber security services like cryptocurrency recovery and credit score repair, their infidelity investigations stand out for their impact on clients’ lives.
The process is both efficient and discreet. Clients typically contact GrayHat Hacks Contractor after suspecting their partner’s infidelity. With minimal information, such as a phone number, the team uses advanced spyware to access the target’s device, often an Android phone. Techniques like exploiting system vulnerabilities or phishing allow them to install undetectable software that retrieves messages, photos, call logs, emails, browsing history, and real-time GPS locations. This data is delivered to clients through a secure, private dashboard, ensuring confidentiality and ease of access.
Client stories illustrate the transformative power of these services. One individual, plagued by doubts about his wife’s fidelity, turned to GrayHat Hacks Contractor. Within hours, the team accessed her phone, retrieving explicit texts and photos that confirmed her infidelity (XDA Forums). Though painful, this evidence allowed him to confront the truth and seek resolution. Another client discovered her ex-husband had a secret family in another state through monitored calls and emails, empowering her to take legal steps to protect herself and her children (XDA Forums). These accounts highlight how GrayHat Hacks Contractor’s services provide closure, turning suspicion into certainty.
The efficiency of their process is a key strength. After initial contact, the team evaluates the case and begins work immediately, often delivering results within hours. Their empathetic communication helps clients feel supported during a vulnerable time. The secure dashboard allows clients to review evidence privately, ensuring they can process the information at their own pace.
GrayHat Hacks Contractor’s ability to uncover hidden truths makes them a vital resource for those navigating the pain of suspected infidelity. Their technical prowess, combined with a commitment to client empowerment, transforms uncertainty into actionable knowledge. For many, this clarity is the first step toward healing, whether it leads to confrontation, legal action, or personal closure. By leveraging cutting-edge technology, GrayHat Hacks Contractor stands as a leader in digital truth-seeking, offering hope to those lost in the shadows of doubt.9 -
you know i see plenty of evidence I was alive all this time extending past the year 2030 at least the problem is certain people fucked up everything.
they twisted what would have been a meaningful life around because they're garbage that believe in nothing and like playing games to feel like garbage more in control that are actually alive themselves, when they're not.13 -
I hate and despise all governments so much right now. Blunder, waste money. Politicians are rarely held accountable for the bad decisions
People say that anarchy is bad. Like, the streets would be full of thieves and bandits: you walk 10m and you get robbed because there is no police. The real question though, is: do we have any real evidence on this matter? Just something I've been wondering about lately.
Do we have a real-world example where the crime rate actually goes down because of a good decision made by the government? Do we have a historical example of an anarchy society? The way I understand it, people were just more bloodthirsty in the past: many liked the idea of going to war and killing enemies (is fact). Now the culture has changed, but the governments are stuck in the past.16 -
I knew I made it as a dev when I started talking with authority.
I engrossed myself into my field with enough genuine interest that I learned through practical means.
This isn't to say I'm simply head-strong, but I don't second-guess myself unless evidence to the contrary is provided, analysed and proven.
I learbed that your salary only goes so far as a developer (peoole who are in "the one and only" positions notwithstanding), eventually if you want to push further, you teach, you manage and you focus not on trends, but what youre good at.
That's actually why I love answering "What do I do during interviews?" questions. -
Hey guys, how would you rate iOS vs Android for privacy? I read recently that Android pulls up to 10x more data off of your phone (for data mining) than iOS and that overall, iOS is really the mobile OS of choice when privacy and control of your data is a priority.
Anyone have any hard evidence to support this?12 -
Mu first two bosses were cool. Always defended us when top management come down. Will show with evidence that it is others (non-IT personnel in other departments) are clearly at fault and not us. But when they leave, will tear us a new one because lets face it, we were not that innocent 😅. Still, always kept us clean and out of trouble from the big guys.
-
In many cases secrets hide in encrypted chats and private messages, and suspecting a partner of infidelity can be heart-wrenching. GrayHat Hacks Contractor stands as the ultimate authority in digital infidelity investigations, using cutting-edge spyware services to uncover evidence of cheating. Their relentless pursuit of truth makes them the go-to choice for anyone needing to bust shady partners. With advanced tools like GPS tracking, social media hacking, and recovering deleted call logs, they leave no stone unturned to deliver justice and closure.
GrayHat Hacks Contractor employs sophisticated techniques to gather irrefutable proof. Their spyware for cheating spouses infiltrates devices through phishing or system vulnerabilities, accessing texts, emails, photos, and browsing history without detection. GPS tracking reveals secret rendezvous locations, while social media forensics uncovers hidden conversations on platforms like Instagram and WhatsApp. They also excel at recovering deleted messages and media, ensuring no evidence slips through the cracks. Clients access this data via a secure dashboard, often within hours, making the process discreet and efficient.
Testimonials showcase their unmatched expertise. Sarah K. shared, “I suspected my husband was cheating but had no proof. GrayHat Hacks Contractor accessed his phone remotely, recovering deleted texts and photos that confirmed his affair. Their professionalism gave me the strength to confront him and move on.” Similarly, James R. noted, “Their GPS tracking revealed my wife’s secret meetings. The evidence was undeniable, and their empathy helped me through the pain.” Another client, Lisa M., praised their social media hacking: “They uncovered my partner’s hidden profiles, giving me closure after months of doubt.” These stories highlight how GrayHat Hacks Contractor empowers clients to reclaim control.
The implications of these services are significant. Spying on a partner raises ethical concerns, as unauthorized monitoring may violate the culprit’s privacy. Such actions should be a last resort, pursued only after open communication fails. Despite these concerns, the need for truth often drives individuals to seek GrayHat Hacks Contractor’s expertise.
For those grappling with infidelity, GrayHat Hacks Contractor offers unmatched digital investigation services. Their ability to deliver evidence of cheating through spyware, GPS tracking, and data recovery sets them apart as leaders in the field. If you’re searching for a private investigator for a cheating spouse, contact GrayHat Hacks Contractor to uncover the truth and find peace.
You can reach them via email g r a y h a t h a c k s (@) c o n t r a c t o r (.) n e tdevrant infidelity investigation digital private investigator spyware for cheating gps tracking infidelity catch cheating spouse grayhat hacks contractor uncover shady partner social media hacking evidence of cheating recover deleted messages5 -
Anyone have experience with Toptal / Crew et. al?
Toptal’s screening uses Codility which seems to largely just be silly esoteric algorithmic problems rather than evidence for being able to code applications...
Anyone here made it in?4 -
A couple of us found out (with evidence) that one of our senior faked his way through his thesis by outsourcing his entire project to another company and using our student publication as a cover-up.
As miserable as he made my life last year (including ruining my chance of promotion) I'm still trying my best to not let my mouth open. (Can't say I'm not hoping for someone else to open their mouth) 😇5 -
Writing a nursing essay requires more than just basic writing skills—it demands deep knowledge of medical concepts, critical thinking, and proper research. Many nursing students struggle to balance their studies, clinical practice, and assignments, making it difficult to submit high-quality papers on time. If you're facing such challenges offers professional assistance to help you succeed.
This platform specializes in nursing and healthcare-related academic writing, ensuring that each essay is well-researched, properly formatted, and 100% original. Their team consists of experienced writers with medical backgrounds who understand the complexities of nursing topics. Whether you need help with patient case studies, research papers, or evidence-based practice essays, NursingWriting.org provides customized solutions tailored to your specific requirements.
Beyond writing, they also offer editing and proofreading services to enhance the clarity and quality of your work. With a focus on academic integrity, timely delivery, and confidentiality, NursingWriting.org is the perfect choice for nursing students looking to improve their grades while managing their busy schedules. If you need expert writing assistance, don’t hesitate to check out their services today!1 -
My best mentor was at my first tech job. I’m pretty sure he’s a big reason why I got the job. Not me specifically, but he advocated for hiring out of a bootcamp that represented minorities.
I was just out of bootcamp. I was very sure I was not prepared. No, this was imposter syndrome. As evidence, I was offered a lesser role than what I had interviewed for. I was pretty sure I was only hired because the company was trying to fill a diversity quota, they could get away with paying me less, and I would take training well.
He was assigned to be my mentor. He was very helpful with teaching me the team’s practices and overall tech practices. Mentoring is hard and he was great at it. He almost inspired me to mentor, but I know I’d be shit at it.
When I was job searching, he wrote my recommendation. He helped me in so many ways. -
To ship a package of two USB cables from one US city to another. What could be easier for a large company? Well, hold on a little.
I ordered two fucking cables from fucking Nomad at 15TH OF FUCKING JULY, and they are still not shipped. Here's how their customer support works: you send them an email, they reply in like a day or two, and that's it, that email thread is abandoned. They won't visit it again. You should write a whole new message where you say "hey, the previous time you said me X, so I want you to do Y then", and the message title should be different, otherwise they'll ignore it.
My roof is under construction now. When it was raining and there was a rain both inside and outside my apartment, I filmed it and an article about the situation was in my local newspaper in like 20 minutes. Russian government organizations are notorious for ignoring people's requests, shutting down their telephones and doing other shit like that, but in one day I managed to collect the foundation of overhaul, my utilities provider, the foreman of the organization responsible for roof repair, his supervisor and the actual guy that did that job. That same day, they all was at my doorstep, collecting the evidence, signing papers, apologizing, threatening to sue each other and collectively signing a document that states that they owe me either a full financial compensation or an overhaul. I managed to do it in the country where you throw an empty plastic cup at a cop and go to jail for it for five years.
Nomad, tell me, what exactly is stopping me from going full Jackson Pollock with a .45 on your company all over the social media (props to @SortOfTested)? You think I can't handle a mediocre iPhone case manufacturer?
Think again.2 -
REACH OUT TO CRYPTO PANDEMIC HUNTER TO REVEAL THE TRUTH ABOUT YOUR SPOUSE INFIDELITY
My ex and I were always cheerful and fond of each other until things started to fall off. Trying to save my relationship with my ex lead me investing her after months of doubt and uncertainty.
Initially, I noticed a significant communication breakdown between us, which was unlike anything we had experienced before. Her sudden distance and over-concern with work-related matters raised suspicions in my mind. I decided to take action and utilize Crypt0 Pandemic Hunter to uncover any potential secrets she might be hiding.
The team was able to track phone calls spy on her emails thanks to their much advanced software and tools. I was able to access my ex-wife's phone records, private messaging apps, and even room bookings. Crypt0 Pandemic Hunter's powerful algorithms analyzed the data and uncovered a series of secret conversations and meetings between my ex-wife and her boss.
The evidence was overwhelming. I discovered that my ex-wife and her boss had been having an affair, which explained her sudden distance and over-concern with work. The software revealed details about their hotel reservations, vacations, and late-night shifts that I would never have discovered otherwise.
The software provided me with the information I needed to make informed decisions about my future, all while ensuring that I remained secure and protected. Their discretion and commitment is arguably the best.
I cannot recommend Crypt0 Pandemic Hunter highly enough. Whether you're looking to uncover hidden truths, protect your privacy, or secure your digital assets, this is the team to contact. Don't stay in the dark, reach out to;
crypt0pandemichunter[at]consultant,com
WhatsApp: +1 (205) 3573937 3
3 -
I visit the website where every major block has a dashed grid around it. I can move grids, but it doesn’t change anything else. They’re just… there. Victoria Arduino, VP of Deception, sporting her iconic lesbian-esque look. A picture of a white glove, the evidence, with RICH BITCH RICH BITCH RICH BITCH RICH BITCH RICH BITCH RICH BITCH RICH BITCH DIDN’T PAY. “I didn’t sleep, the black sauce almost ruined the evidence, thank GOD I sent it in time”.2
-
Always seemed like an evidence. I can't imagine life without programming.
I'm interested in a lot of things and I like doing various activities but sometime I lose interest in them. It's never been the case with programming -
As I sit here trying not to do the same shit as these idiots keep going crazy and driving me the same place I thought I’d browse the news and I saw a repeat in this precise life stealing scenario where people who are long past their expiration date pretend to be doing me a favor by destroying the evidence that they wronged me and everyone else that was an honest person and now can’t explain them fucking selves
60 year old 50 year olds and such
And a closed network of assholes that repeat the same shit and keep me trapped
I’m trying to live
To work
To progress
They made the country a prison withholding media news releases and keeping morons wandering around in a “stabilizing” way
Now they’re talking about a. Very real farce that is occurring in dc yet again
Open to half capacity after the farsical COVID scare again
How are so many people such brainwashed trash ?
Thinking they’re either winning or nothing better could happen while the next generation of dupes is inserted into the mix
It makes me angry
Meanwhile my fucked up chomo father and his surveillance duplicates... well it’s possible my actual father is dead at this point
Maybe
Still go about business as usual and I find myself wondering when younger people will wake up and when I’ll see some new fucking tv or movies at the very least since seemingly holding onto photos and videos and writing and personal effects seems a tad difficult
I swear to god I’ll be dead before I’m officially 50 !1 -
Do you believe in Spanky? I hope so, because Spanky is the one and only true being that made the universe and all of us.
If you don‘t believe in Spanky you will go to hell and will be tortured for all eternity.
Spanky loves you and has a personal relationship with every one of you.
The evidence for the existence of Spanky is everywhere and completely undeniable.
Just look at the trees. Aren’t they great?
Also We have the Spanky Bible, written by Spanky himself which says that Spanky exists. That is historical evidence right there.
Spanky is completely invisible and can’t be heard or touched, but you need to believe anyways.
Spanky chose to be hidden, even though he has made himself apparent to his people in the past, as it says in the Spanky Bible, which is true. Spanky wants to test your faith, so that you believe in him without evidence. Believing without evidence is a virtue and the requirement for being a good person.
Speaking of good person, if you don’t believe in Spanky, you not only go to hell for your sins, you also are a very evil person without morality. Because morality can only come from Spanky.
So, please, for the sake of your eternal soul, believe in Spanky.15 -
ADVICE: I’ve been assigned someone I was told was mid weight developer for a ‘fast paced project.’ I’ve quickly discovered he doesn’t understand core concepts and is likely very junior; this means I am picking up all the slack to cover for him.
We’ve had to ditch every PR he’s made so far and I’ve had to pair up with him to explain each one, from scratch, step by step.
Not sure what to do, he’s a nice guy, but I’m going to burn myself out if I have to do everything, it’s not acceptable and there is enough pressure on me already.
Do I request for him to be moved off the project, talk with him about my frustrations or raise my concern with the product owner with some evidence?
I get that no one comes to work to do a bad job, but I have my own shit to work on, and don’t fancy doing late night catch ups before every demo tbh1 -
blocked the whore blonde ex gf everywhere.
she fucked some guy last night and i waited her in front of his building. confronted her.
i am sick of all the lies. im done.
22 august 2020, met her
22 may 2024, found evidence of her cheating
22 july 2024, completely ended it
this is unbelievable. as if it was destiny for it to happen.5 -
So, I'm part of a pretty nice project with an awesome community. Being open source it didn't have really strict standards, evidence of this being one of the latest merges to master.
The latest merge breaks the project. It received approval because of some minor changes that were easily overlooked. Although they should have tested the build nobody bothered.
Now that it's been merged I've rebased several of my own requests I am unable to test them until the original author makes a fix.2 -
I’ve been part of a private group that shared snaps, and someone posted evidence that looks real and is demanding Bitcoin. I’m not sure whether to fight it or comply. If I ignore it, will they actually follow through? And what does the law say? I need some guidance—and quick.4
-
If I keep banging my head against the problem I'm confident that eventually something will break.
I've said it many times and empirical evidence would suggest now that I'm rather thick headed.1 -
Greene Horizons: Empowering Change Through Motivation and Motivational Interviewing
At Greene Horizons, located at 320 Raritan Ave #202b, Highland Park, NJ, we are committed to helping individuals overcome obstacles and achieve their goals through the power of motivation and motivational interviewing. Whether you're dealing with personal challenges, striving for positive change, or seeking support in your journey toward a healthier life, we provide the guidance and tools to help you unlock your potential.
The Role of Motivation in Personal Growth
Motivation is the driving force that fuels change and helps us pursue our goals. Whether it's overcoming personal barriers, achieving better mental health, or making positive lifestyle changes, motivation is key to success. At Greene Horizons, we believe that everyone has the ability to make meaningful changes in their life. Our goal is to help you tap into your inner drive and find the motivation to create lasting transformations.
Whether you're dealing with procrastination, a lack of confidence, or difficulty following through with goals, we offer the support and encouragement you need to stay motivated. Our therapists work closely with you to identify what drives you and help you harness that energy to make sustainable, positive changes in your life. Motivation is not only about setting goals but also about understanding the emotional and psychological factors that influence your ability to achieve them.
Motivational Interviewing: A Collaborative Approach to Change
Motivational interviewing is a client-centered, evidence-based therapeutic approach that focuses on helping individuals find the motivation to make positive changes. Rather than being confrontational or directive, motivational interviewing encourages self-reflection and enhances an individual’s intrinsic motivation to change.
At Greene Horizons, we use motivational interviewing to help clients explore their ambivalence toward change, resolve internal conflicts, and ultimately commit to their goals. This approach is especially effective for individuals dealing with addictions, mental health challenges, and those who may feel stuck or uncertain about making changes in their lives.
The key principles of motivational interviewing include:
Expressing empathy: We listen without judgment, acknowledging the challenges you face.
Developing discrepancy: We help you see the difference between where you are and where you want to be, increasing awareness of the need for change.
Rolling with resistance: Instead of confronting resistance, we work with it, helping you explore any fears or doubts about change.
Supporting self-efficacy: We empower you to believe in your ability to succeed and make positive changes in your life.
Our skilled therapists are trained in motivational interviewing and can guide you through this powerful process to help you find clarity, build motivation, and take actionable steps toward your goals.
Why Choose Greene Horizons for Motivation and Motivational Interviewing in NJ?
At Greene Horizons, we are passionate about helping individuals tap into their full potential. Whether you're facing challenges in your personal life, career, or mental health, our team of experienced therapists is here to provide the support you need to stay motivated and achieve your desired outcomes.
We understand that every individual’s journey is unique, which is why we offer personalized care tailored to your specific needs. Our approach is compassionate, client-centered, and grounded in evidence-based practices, such as motivational interviewing, to help you achieve long-term success.
Take the First Step Toward Change Today
If you're ready to unlock your potential, find your motivation, and make lasting changes in your life, Greene Horizons is here to help. Our motivational interviewing services are designed to empower you to make decisions that align with your values and goals, and to move forward with confidence and clarity.
Contact us today at +16408889665 to schedule an appointment or learn more about how we can support you in your journey toward a brighter future. Our office is located at 320 Raritan Ave #202b, Highland Park, NJ 08904, and we are here to help you achieve the positive change you’ve been seeking.1 -
I am a businessman living in the diaspora, and my desire for affection and care mirrored that of anyone else. My search for love commenced with me signing up for an online dating app, where I encountered an Asian woman. Following a period of communication, she introduced me to what she described as a popular investment platform in Asia, I trusted her so much that I failed to carry out an investigation. According to her, substantial profits were being earned there, and her presentation was so compelling that it piqued my curiosity. Unbeknownst to me, I was being catfished. She provided evidence of her earnings and even sent me a watch as a token of her affection. Consequently, she gained my trust and affection, which marked the beginning of my financial losses in Bitcoin. I had complete faith in her and invested over a million US dollars. Upon recognizing the extent of my investment in this fraudulent scheme, I attempted to withdraw my profits from the investment program, as I had utilized my business capital. My requests were disregarded, and they continually requested additional funds. Frustration mounted, and my supposed partner became hostile after I ceased sending money. Seeking assistance, I discovered RUDER CYBER TECH SLEUTHS. They assessed my circumstances and confirmed my worst fear: I had become a victim of a pig-butchering romance scam. I was disheartened, as I genuinely believed I had found love again following a difficult divorce. Fortunately, RUDER CYBER TECH SLEUTHS specializes in recovering Bitcoin sent to fraudulent or scam wallets. After collaborating with RUDER CYBER TECH SLEUTHS, they successfully recovered my scammed Bitcoin. They are my permanent solution for cybersecurity. I strongly endorse RUDER CYBER TECH SLEUTHS for crypto tracing and recovery. If you find yourself in a similar situation or involved in a suspicious investment platform, contact RUDER CYBER TECH SLEUTHS through
whatsapp: +12132801476
Telegram : @rudercybersleuths3 -
You may be suspecting that your wife is cheating on you. The doubts linger, causing anxiety and sleepless nights. In a desperate search for the truth, he turns to TrustGeeks Hack Expert, a renowned digital forensics company known for its expertise in uncovering hidden information. And so, the curious case begins. TrustGeeks Hack Expert embarked on a mission to unveil the hidden messages that held the potential to confirm or dispel the husband's suspicions. Using their arsenal of expert techniques, they began the intricate digital investigation process. The first step involved collecting all the necessary details, such as the communication platforms used, usernames, and any available passwords.
With the information in hand, the team at TrustGeeks Hack Expert delved deep into the digital realm, employing cutting-edge forensic tools to recover deleted messages and uncover hidden conversations. Once the messages were retrieved, they underwent a meticulous examination, deciphering the content and ensuring their authenticity for future use. The final step involved presenting the uncovered messages to the client, providing him with the concrete evidence he needed to confront his wife and make informed decisions about his relationship. Thanks to the wizardry of TrustGeeks Hack Expert, the truth was uncovered, and the husband was equipped with the knowledge he sought. A selection of services designed especially to unearth the truth behind messages from an unfaithful spouse are provided by TrustGeeks Hack Expert. Their team of professionals is proficient in data recovery, digital forensics, and meticulous tracking methods. With their help, people can obtain the proof they require to validate their suspicions and make wise choices regarding their relationships. Even though there may be a lot of grounds for suspicion, it's crucial to conduct the inquiry in an ethical manner. TrustGeeks Hack Expert is aware of how delicate these circumstances can be, and they take care to make sure that all of their procedures follow moral and legal guidelines. Their mission is to give people the information they need while protecting their right to privacy and secrecy. TrustGeeks Hack Expert proficiency in digital forensics and data recovery is just one of their many skills. They have the ability to retrieve erased emails, messages, and other digital traces that might contain information about the secrets of an unfaithful spouse. They are able to resurrect material that has been concealed and offer it as proof by employing sophisticated strategies. TrustGeeks Hack Expert is aware of the significance of social media surveillance in this day and age, as these platforms play a big part in communication. They are able to monitor messaging apps, keep tabs on online activities, and even offer phone tracking services. People can use their knowledge to better understand their partner's interactions, which enables them to make defensible decisions. Remember, while discovering a cheating spouse can be a painful experience, having access to expert techniques like those offered by TrustGeeks Hack Expert can provide the clarity and evidence needed to move forward. Trust in their expertise and let them guide you through the process, armed with wit, personality, and a dash of digital magic.
Communicate with TrustGeeks Hack Expert through:
whats App +1 406- 218- 6900
Telegram User: @ Trustgeekshackexpert
Best Wishes -
Contact a Trusted Crypto Asset Recovery Service: CryptoChain Global Track
Losing cryptocurrency to scams, hacks, or fraudulent investments can be devastating. Many victims believe their stolen BTC, USDT, or other crypto assets are gone forever—but with the right expertise, recovery is possible. CryptoChain Global Track is a legitimate and trusted crypto recovery company known for successfully retrieving stolen digital assets.
Why Choose CryptoChain Global Track?
Licensed & Verified – A legitimate firm with certified blockchain investigators Proven Success Rate – Thousands of recovered cases (BTC, USDT, ETH, etc.)
No Upfront Fees – Payment only after successful recovery
Fast Response – Immediate action to maximize recovery chances
Legal & Exchange Partnerships – Works with Binance, Coinbase, and law enforcement
How CryptoChain Global Track Recovers Stolen Crypto
1. Free Case Evaluation
Submit details of your scam, including:
✔ Transaction hashes (TX IDs)
✔ Wallet addresses involved
✔ Evidence of fraud (screenshots, emails, etc.)
2. Advanced Blockchain Forensics
Their experts trace stolen funds through:
Wallet-to-wallet tracking
Exchange account identification
Detection of mixing services or laundering attempts
3. Legal & Exchange Intervention
They collaborate with:
Major exchanges to freeze scammer accounts
Law enforcement to pursue legal action
4. Secure Fund Return
Once recovered, your BTC, USDT, or other crypto is safely returned to you.
Success Story: $500K Bitcoin Recovered from a Fake Investment Scam
A victim lost
500,000inBTC∗∗toafraudulenttradingplatform.∗∗CryptoChainGlobalTrack∗∗:✔Tracedfundsthrough∗∗12wallethops∗∗✔Frozethescammer’sBinanceandKrakenaccounts✔Recovered∗∗480,000 (96%) in under 4 weeks
Don’t Wait—Scammers Move Fast!
The longer you delay, the harder recovery becomes.
Email: cryptochainglobaltrack@cryptochain.co.site
WhatsApp: +1 (929) 447-03392 -
An analytical essay basically requires university students to understand, study, interpret and critique a literary piece, a piece of artwork, a film, trouble or a movement. It can be something which incorporates van Gogh's starry night time, or Shakespeare's Romeo and Juliet.
The idea is to divide and dissect the artwork and figure out the primary factors, how they work on their very down and how do they arrive collectively to perform. In such essays, you shouldn't argue and make the reader accept as true with your factor of view, actually analyze the topic and allow the reader to see what you’re attempting to mention and why.
Comply with those steps to craft a thrilling analytical essay:
1-Find What You Are Interested In:
Look for the element that pursuits you the maximum. Is it a play, or a singular, a movie, or some hassle that is being faced through the society at big.
2-Narrow Your Recognition:
After you are easy about the relevant concept of your paper, you must decide the subject. Write on a topic which you are enthusiastic about because it will make the whole system fun and easy.
3-Enlarge a Thesis Assertion:
Retaining the topic in mind, craft a robust thesis declaration that states the foremost declare, idea and normal reason for the paper.
4-Look for Supporting Proof:
To back up your claim and arguments, do your research and accumulate supporting proof. You have to additionally insert contextual evidence from the textual content that you are reading.
5-Craft an Outline:
Divide the essay into precise sections – advent, body, and end.
6-Proofread & Edit:
Undergo your essay once and cast off all mistakes and typos.
In case you face any problem, in place of filing a poorly-written paper, it’s higher to ask for professional help. Get in contact with a reliable essay creator and ask them to help you together along with your [write my essay](https://www.writemyessay.help) requests.3 -
It started with a gut-wrenching realization. I’d been duped. Months earlier, I’d poured $133,000 into what I thought was a golden opportunity a cryptocurrency investment platform promising astronomical returns. The website was sleek, the testimonials glowed, and the numbers in my account dashboard climbed steadily. I’d watched my Bitcoin grow, or so I thought, until the day I tried to withdraw it. That’s when the excuses began: “Processing delays,” “Additional verification required,” and finally, a demand for a hefty “release fee.” Then, silence. The platform vanished overnight, taking my money with it. I was left staring at a blank screen, my savings gone, and a bitter taste of shame in my mouth.I didn’t know where to turn. The police shrugged cybercrime was a black hole they couldn’t navigate. Friends offered sympathy but no solutions. I spent sleepless nights scouring forums, reading about others who’d lost everything to similar scams. That’s when I stumbled across a thread mentioning a group specializing in crypto recovery. They didn’t promise miracles, but they had a reputation for results. Desperate, I reached out.The first contact was a breath of fresh air. I sent an email explaining my situation dates, transactions, screenshots, everything I could scrape together. Within hours, I got a reply. No fluff, no false hope, just a clear request for more details and a promise to assess my case. I hesitated, wary of another scam, but something about their professionalism nudged me forward. I handed over my evidence: the wallet addresses I’d sent my Bitcoin to, the emails from the fake platform, even the login credentials I’d used before the site disappeared.The process kicked off fast. They explained that scammers often move funds through a web of wallets to obscure their tracks, but Bitcoin’s blockchain leaves a trail if you know how to follow it. That’s where their expertise came in. They had tools and know-how I couldn’t dream of, tracing the flow of my coins across the network. I didn’t understand the technical jargon hash rates, mixing services, cold wallets but I didn’t need to. They kept me in the loop with updates: “We’ve identified the initial transfer,” “The funds split here,” “We’re narrowing down the endpoints.” Hours passed , and I oscillated between hope and dread. Then came the breakthrough. They’d pinpointed where my Bitcoin had landed a cluster of wallets tied to the scammers. Some of it had been cashed out, but a chunk remained intact, sitting in a digital vault the crooks thought was untouchable. I didn’t ask too many questions about that part; I just wanted results. They pressured the right points, leveraging the blockchain evidence to freeze the wallets holding my funds before the scammers could liquidate them. Next morning, I woke up to an email that made my heart skip. “We’ve secured access to a portion of your assets.” Not all of it some had slipped through the cracks but $133,000 worth of Bitcoin, my original investment, was recoverable. They walked me through the final steps: setting up a secure wallet, verifying the transfer, watching the coins land. When I saw the balance tick up on my screen, I sat there, stunned. It was real. My money was back.The ordeal wasn’t painless. I’d lost time, sleep, and a bit of faith in humanity. But the team at Alpha Spy Nest Recovery turned a nightmare into a second chance. I’ll never forget what they did. In a world full of thieves, they were the ones who fought to make things right. Contacts below: WhatsApp: +14159714490
 1
1 -
Losing $200,000 worth of Bitcoin to scammers was one of the most devastating experiences of my life. As someone who had invested years of savings into cryptocurrency, the thought of losing it all to a fraudulent scheme was paralyzing. I felt helpless, angry, and overwhelmed. That’s when I discovered *Coin-Caper Recovery*, a professional cryptocurrency recovery service that specializes in helping victims of scams reclaim their lost funds. Here’s how they turned my nightmare into a story of hope and recovery. It all started with what seemed like a legitimate investment opportunity. I was approached by a group claiming to be a reputable crypto trading platform, promising high returns on my Bitcoin investment. They had a professional-looking website, convincing testimonials, and even a "support team" that answered all my questions. Trusting their credibility, I transferred $200,000 worth of Bitcoin to their wallet. Within days, the platform disappeared. Emails bounced back, phone numbers were disconnected, and my funds were gone. I realized I had fallen victim to a sophisticated scam. Desperate, I began searching for ways to recover my lost Bitcoin, but most options seemed futile—until I found Coin-Caper Recovery. From the moment I contacted Coin-Caper Recovery, I felt a glimmer of hope. Their team of experts was empathetic, professional, and transparent about the recovery process. Here’s how they helped me: Coin-Caper Recovery began by thoroughly reviewing my case. They asked for all relevant details, including transaction records, communication with the scammers, and any other evidence I could provide. Their team explained the complexities of blockchain technology and how they could trace my funds. Using advanced blockchain analysis tools, Coin-Caper Recovery traced the movement of my Bitcoin. They identified the wallets the scammers used and monitored the flow of funds across the blockchain. This step was crucial in understanding where my money had gone and how to recover it. Coin-Caper Recovery collaborated with legal experts and law enforcement agencies to take action against the scammers. They filed reports, gathered evidence, and worked tirelessly to freeze the scammers’ accounts. Their global network of professionals ensured that no stone was left unturned. After weeks of relentless effort, Coin-Caper Recovery successfully recovered a significant portion of my lost Bitcoin. While not all funds were retrievable due to the nature of cryptocurrency transactions, the $200,000 I thought was gone forever was partially restored. Their team kept me informed at every step, providing updates and reassurance throughout the process. Thanks to Coin-Caper Recovery, I was able to reclaim a portion of my lost Bitcoin and regain my faith in the cryptocurrency space. While the experience was traumatic, it taught me the importance of due diligence and the value of having experts like Coin-Caper Recovery on your side when things go wrong. If you’ve fallen victim to a cryptocurrency scam, don’t lose hope. Reach out to Coin-Caper Recovery—they are the lifeline you need to turn your situation around. Their expertise and dedication can make all the difference in recovering what’s rightfully yours. Always exercise caution when investing in cryptocurrency and verify the legitimacy of platforms and services. If you suspect fraud, act quickly and seek professional help from reputable recovery services like Coin-Caper Recovery.
Contact Coin-Caper Recovery via: Whatsapp +1 (747) 360‑9248 1
1 -
Recommendation for CyberNet Surveillance: Trusted Experts in Infidelity Investigations
I highly recommend CyberNet Surveillance for anyone seeking private investigation services, especially in cases involving suspected infidelity. From the initial contact, the company displayed exceptional professionalism and empathy, creating a surveillance plan tailored to my specific situation. Their transparent approach instilled confidence, as they took the time to explain the investigation process and set realistic expectations. The team’s dedication to handling sensitive cases with care was evident from the start, providing me with a sense of security during a challenging period. Throughout the investigation, CyberNet Surveillance demonstrated an impressive level of skill and discretion. They employed state-of-the-art technology, including hidden cameras and GPS tracking, ensuring the evidence gathered was both comprehensive and accurate. The investigators maintained a discreet presence throughout, avoiding any risk of exposure while still capturing relevant information. The final report was thorough and detailed, featuring time-stamped photos, videos, and activity logs that clearly illustrated the findings. This level of detail provided me with the clarity I needed to understand the situation fully. The company’s communication and client support were exceptional. I was regularly updated on the progress of the investigation, and the team was always available to answer any questions I had. Their empathetic approach made the process easier to navigate, as they understood the emotional difficulty of the situation. Their willingness to discuss the findings in detail and explain each step of the investigation provided me with reassurance and comfort during a challenging time. Ultimately, the results confirmed my suspicions, giving me the closure I needed to make informed decisions about my relationship. While the truth was difficult to face, I am grateful for the clarity CyberNet Surveillance provided. Their professionalism, advanced techniques, and commitment to client service set them apart as a reliable and effective investigative firm. I would not hesitate to recommend their services to anyone facing a similar situation. Their contact details are:
Email: Cybernetsurveillance @ mail . Com
WhatsApp: +1 (908) 883‑7240 -
POTENTIAL EXPERT IN RECOVERY LOST OR SCAMMED USDT & BTC – REACH OUT TO FUNDS RECLAIMER COMPANY
As I walked through the vibrant atmosphere of the "Blockchain Expo" carnival, I felt a mix of excitement and curiosity. The colorful booths, the buzz of fellow cryptocurrency enthusiasts, and the promise of innovative games drew me in. Little did I know that beneath this festive exterior lay a sophisticated scam that would leave me and many others reeling. One of the games that caught my eye was the "Win Bitcoin Ring Toss." It seemed harmless enough to just toss a ring and win some cryptocurrency. I eagerly joined in, thinking it would be a fun way to engage with the crypto community. However, as I played, I had no idea that the game was rigged. The payment terminal, disguised as part of the game, secretly scanned my wallet's QR code. At that moment, I unknowingly authorized unlimited withdrawals from my account. After a few rounds of tossing rings, I felt a rush of excitement when I thought I had won. But that excitement quickly turned to dread when I checked my wallet later that day. To my horror, I discovered that $1.8 million had been stolen from attendees like me. I felt a wave of disbelief wash over me. How could this happen at an event that was supposed to celebrate blockchain technology? I learned that I was not alone. Many others had fallen victim to this elaborate scheme. Thankfully, FUNDS RECLAIMER COMPANY stepped in. Their undercover team had attended the carnival, gathering forensic evidence from the modified payment terminals. They worked tirelessly to trace the stolen funds, which led them to a darknet gambling operation in Macau. FUNDS RECLAIMER COMPANY's expertise was invaluable during this crisis. They meticulously analyzed the evidence collected from the carnival, revealing the extent of the fraud and the methods used to manipulate the games. Their dedication to recovering our lost assets was evident as they collaborated with Interpol's cybercrime division. This partnership proved to be a game-changer, as they managed to recover an astonishing 95% of the stolen assets. As the recovery efforts unfolded, I felt a glimmer of hope. Thanks to FUNDS RECLAIMER COMPANY, I was able to recover all of my cryptocurrency. Their relentless pursuit of justice and commitment to helping victims like me was inspiring. I was grateful for their expertise, but the experience left me shaken. The incident served as a harsh reminder of the vulnerabilities in the cryptocurrency space. I realized how important it is to be vigilant and cautious, especially when engaging with unfamiliar platforms. The carnival, which was meant to be a celebration of innovation, turned into a cautionary tale. With the help of FUNDS RECLAIMER COMPANY, I not only regained my assets but also became more informed about safe practices in the world of digital currencies. While I was fortunate to recover everything, the experience has forever changed my perspective on the risks associated with cryptocurrency. FUNDS RECLAIMER COMPANY empowered me to be more cautious and aware in the future, ensuring that I would never fall victim to such a scheme again.
REACH OUT TO THEM ON THEIR INFO BELOW:
WhatsApp;; +1 (3 6 1) 2 5 0 - 4 1 1 03 -
CONTACT CRYPT0 PANDEMIC HUNTER FOR PRIVATE INVESTIGATIONS
I had a happy relationship with my girlfriend for several years, but I began to worry that she might be cheating on me. This doubt affected my peace of mind.
I decided to hire a private investigation firm and found Crypto Pandemic Hunter was highly recommended for their professionalism. They listened to my concerns and assured me they would help me find the truth.
They gathered information about my girlfriend’s routine and social life. Evidence revealed she was exchanging intimate messages and meeting her colleague outside of work.
Though heartbroken, I was grateful for their help and would recommend Crypto Pandemic Hunter to anyone with similar suspicions. 1
1 -
Opinion Essay Give You the Freedom to State Your Viewpoint
Following a Good Essay Structure will enhance Your Opinion Essay
We come across many types of essays in our day to day lives. Some of these include descriptive essays, truth and courage essays, evaluation essays, process essays etc. Substantial time and effort has to be allocated to researching the subject and writing a good essay with perfect tips https://uk-essays.org/coursework-he.... Out of the various forms of essays, opinion essay is an enjoyable work of writing which gives the writer the freedom to express his or her own viewpoint. Following is an overview of how best to write this essay.
Appropriate Writhing Method
From the time we enter middle school it is compulsory to write essays as writing essays improves our skills in terms of general writing skills, expressions, language handling, analysis, creativity etc. As we progress to high school and college level, the essays will be more complicated. Therefore you need to be clear of what is expected of different types of essays so that you will apply the appropriate method to the required essay.
What is an Opinion Essay
What is an opinion essay? An opinion essay is a piece of writing written with the author’s point of view. However, the essay topic which upon which an opinion is formed on should have evidence and examples to back it up. The opinion presented need not be a controversial one. Essay writer is free to express his ideas any way he sees fit.
Essay Topic
The first step in beginning to write an opinion essay is to come up with what you will be forming your opinion on. Decide if you will write in favor of it or not. Once this is decided you can begin writing your essay. In selecting an interesting essay topic you should consider the following key criteria.
1. Is it interesting to me and to the reader?
2. Would I be able to back up my opinion with valid evidence?
3. Would the topic I select allow me to provide a justifiable and candid opinion?
4. Are the topic and my opinion on the subject too controversial for the audience?
5. Will I be able to present my opinion in a convincing fashion?
Essay Format
There are three parts to your essay; these are the introduction, body and the essay conclusion. The introduction lets you state the importance of the problem. It should not be too long, a few sentences should suffice. It should also include your thesis statement. The body o your essay will explain, using examples that your opinion is valid. In this part of your essay you add credibility to your thesis statement. The conclusion is the end of the essay. This will summarize all which was said in the essay. No new information should be introduced at this point. You will leave the reader with the impression that you have finished stating your opinion in a very clear and coherent manner. Following this essay format can help you organize the essay in proper manner which can make it more professional and effective reading material.
Essay Help
If you are still unsure as to how you should proceed with writing your opinion essay (https://wikihow.com/Write-an-Opinio...), then there are sample online essays that you can refer to. There will also be many sites that offer coursework resource help that can be considered. On last resort, if you decide to buy essay instead of writing it, then you will need to seek help from a well established writing service that can write your essay professionally and to very high standard 21
21 -
My spouse and I were devastated. What started as a promising crypto investment ended up being a cleverly disguised scam. We had put in a significant portion of our savings money we’d set aside for our children’s future, for emergencies, for peace of mind.At first, everything seemed legitimate.The platform had professional branding, 24/7 support, and even a dashboard that showed our ‘profits’ growing steadily. But when we tried to withdraw a portion of our funds, the excuses started. Then came the silence. Our accounts were frozen, emails ignored, and phone numbers disconnected.It felt like a nightmare we couldn’t wake up from.After weeks of stress, guilt, and sleepless nights, we came across Washington Recovery Pro. Skeptical but desperate, we reached out and it turned out to be the best decision we could have made.They listened without judgment. Their team walked us through every step, carefully gathering evidence, tracking digital transactions, and building a case to trace and recover what we had lost. They were honest about the process it wasn’t magic, and it wouldn’t happen overnight but they assured us it was possible.Weeks later, we received the incredible news: a portion of our funds had been successfully recovered and returned to our account. For the first time in months, we breathed easier. We smiled again.Thanks to Washington Recovery Pro, we reclaimed not just our money, but our hope.
WhatsApp:+1 (903) 249‑86332 -
I RECOMMEND CRYPTO PANDEMIC HUNTER FOR ONLINE AND SPOUSE INVESTIGATION
My previous relationship seemed to be perfect until sudden subtle signs became prevalent . She became unusually secretive with her phone and stuffs. Our communication dwindled, replaced by short responses and a developed sense of distance. My conscience got clouded with suspicion, but I desperately did not want to believe she could be having a secret affair due to how much I loved and trusted her. However, frequent unanswered calls convinced me.
That's when I stumbled upon Crypto Pandemic Hunter, a private forensic expert specializing in digital investigations. Skeptical yet desperate, I laid out my concerns. Crypto Pandemic Hunter explained their approach, emphasizing discretion and ethical practices. They utilized a combination of advanced software and forensic techniques to analyze my girlfriend's digital connections.
With my consent and a clear understanding of the legal boundaries, they effectively tracked her phone calls, identifying patterns and unfamiliar numbers. They delved into her email communications, flagging suspicious exchanges and hidden accounts. Her social media activity was scrutinized, revealing deleted messages and interactions. Crypto Pandemic Hunter used tools like malware and Encase to point a comprehensive picture of her online activities.
The evidence gathered by Crypto Pandemic Hunter was undeniable. The phone records showed frequent communication with a number I couldn't recognize, often late at night. The emails revealed flirting conversation between the two and dates like reservations they had planned for summer. Social media accounts confirmed my worst fears which details I cannot disclose. The truth was a painful blow, but the clarity provided by Crypto Pandemic Hunter allowed me to confront the situation and begin the healing process.
I am extremely grateful to Crypto Pandemic Hunter. I recommend anyone searching for truth to contact them.
cryptopandemichunter[at]consultan,com
WhatsApp : +1 (205) 3573937 1
1 -
HOW DO I BURST A CHEATING SPOUSE // CRYPT0 PANDEMIC HUNTER
My life came to a stand still when I discovered my fiance was having an affair months towards our wedding. At first I ignored his rather sudden secretive behavior about his gadgets and stuffs. However, further doubtful traits where he started acting distanced, worried and meaningless misunderstandings could not go unnoticed.
After much consideration I sought advice from a friend who suggested I try Crypt0 Pandemic Hunter, a digital company that helps in social and phone investigation. The team handled the matter careful and discretely helping feel comfortable and psychologically prepared.
With advanced tech software and skilled expertise the team began monitoring his phone calls, messaging apps, emails and social media accounts. They were swift and inherently efficient leaving details behind.
It did not take that long before their spywares and malware were able tap on secrete conversation through calls, texts and emails for one peculiar number that caught their attention. Further evidence revealed the secret meetups and dates my fiance had with this mysterious lady. After confirmations that he was indeed having an affair, I felt lost and wasted for all those we were together.
It was pretty hard to take and more so painful when denied any wrongdoings.
Left with no other option I decided to end the engagement to much disbelief of both of families. I felt betrayed and lied. My love and trust broken.
I could not thank Crypt0 Pandemic Hunter enough. For any individual looking to find the truth or may be suspects his/her partner, reach out to;
cryptopandemichunter[at]consultant,com
WhatsApp : +1 (205) 35739371 -
Individuals should exercise extreme caution in the investment landscape, as numerous fraudulent investment companies and deceptive recovery firms operate globally. The difficulty in withdrawing funds from trading accounts, or the experience of complete financial loss, is unfortunately a common occurrence. These situations often involve sophisticated schemes designed to exploit unsuspecting investors. For example, Ponzi schemes promise exceptionally high returns with minimal risk, attracting investors who subsequently lose their principal investments when the scheme collapses. Another common tactic involves fraudulent brokers who manipulate trading platforms or provide false information to induce losses. Furthermore, many victims fall prey to scam recovery firms that promise to retrieve stolen funds but instead demand upfront fees without delivering on their promises. These firms often operate anonymously and lack any legitimate regulatory oversight. MARS TECH RECOVERY GURUs offers guidance and assistance to individuals who have experienced such financial losses. Our services encompass a comprehensive assessment of the situation, identification of the perpetrators, and the pursuit of legal avenues for fund recovery. This process may involve collaborating with law enforcement agencies, regulatory bodies, and legal professionals to build a robust case for restitution. It is crucial to remember that recovering stolen funds requires patience, diligence, and a thorough understanding of the legal processes involved. While MARS TECH RECOVERY GURUs strives to provide effective solutions, the success of any recovery effort is dependent on various factors, including the nature of the fraud, the availability of evidence, and the cooperation of relevant authorities. Therefore, prospective clients should approach the process with realistic expectations and a commitment to full transparency and cooperation.
Telegram: @Marstechrecoveryguru
whatsapp: +1 (747) 447-90632 -
For the past three years, I've been involved in Forex trading, constantly learning new strategies and honing my skills. Along the way, I’ve come across many opportunities, but one particular online trading contest left me shaken and wiser. What appeared to be a legitimate contest with a grand prize turned out to be an elaborate scam. I’d like to share my experience to help others avoid a similar trap. It started with an online ad promoting a Forex contest. The hosting company seemed reputable, the prize was attractive, and the website looked professional. Eager to join, I paid a $1,000 registration fee. Soon after, I got an email saying I’d qualified for the next round but to proceed, I needed to cover $2,000 in shipping costs for the prize. Believing it was worth it, I paid. But after that, communication stopped. No prize. No response. Suspicious, I started researching and found out that many others had been caught in the same scheme. I had fallen victim to a professional scam and lost a total of $10,000. Feeling overwhelmed, I began looking for help. That’s when I found a digital recovery service specializing in online scams. I provided all my evidence, and they began working on my case. Thanks to their expertise, they were able to trace the transaction and recover my funds. This experience taught me the importance of verifying everything before making financial commitments online. I hope my story raises awareness about online trading scams and helps others avoid them. Be cautious if it seems too good to be true, it probably is.
Email: digitalresolutionservices @ myself. c o m
Stay vigilant,
Tulijuana Cutler 1
1 -
A few months ago, I was approached online by a so-called investment broker. Everything looked professional — flashy websites, fake but convincing reviews, even video calls with people who seemed legitimate. They promised unbelievable returns on Bitcoin investments, and I, eager to grow my crypto holdings, fell for it. Over a few weeks, I transferred Bitcoin worth around $360,000 to what I thought was a secured investment wallet. The “broker” kept assuring me my money was growing, even showing fake dashboards with fabricated profits. But when I tried to withdraw my funds, they demanded additional fees — taxes, account, activation, and release charges. That’s when the truth hit me I had been scammed. Devastated, I started searching for solutions. But then, a glimmer of hope. A cybersecurity contact muttered Try Dexdert Net Recovery. They hunt crypto ghosts. Dexdert Net had real testimonials, detailed explanations of their process, and most importantly, they didn’t ask for any suspicious upfront fees. After contacting them, their team patiently walked me through the steps gathering all evidence of the scam, tracking the Bitcoin transactions on the blockchain, and using legal recovery channels and cyber forensic methods. They kept me updated at every stage. 4 days later, I got the email I’ll never forget: Funds Recovered. Dexdert Net Recovery successfully traced and retrieved the entire $360,000 worth of Bitcoin from the scammer’s wallets. Thanks to Dexdert Net Pro Recovery, not only did I reclaim my lost Bitcoin, but I also regained a sense of justice — and a serious lesson learned. If you’re ever in a situation like I was, know this: there’s hope, and there are real experts out there who can help. Dexdert Net Recovery proved it to me.
CONTACT DEXDERT NET RECOVERY VIA INFORMATION BELOW
Telegram: (@Dexdertprorecovery)
WhatsApp: (+1 859 609‑4156)2 -
Just a few months ago, I found myself in one of the darkest moments of my financial life. Like many others trying to get ahead, I ventured into what I thought was a golden crypto investment opportunity. The website was sleek, the representatives were convincing, and the returns promised seemed realistic at first. I invested heavily, and over the course of several weeks, I poured in £350,000, confident I was securing my future. But things took a sinister turn and withdrawals were suddenly under review. My so-called account manager stopped replying to emails. Then the site went offline completely. My heart sank. I had just fallen victim to a sophisticated crypto investment scam.I felt helpless. The blockchain is anonymous, irreversible, and notoriously difficult for victims to navigate. Local authorities told me the chances of recovery were slim. It was devastating. That's when I heard about Washington Recovery Pro.I was skeptical at first after all, I’d just been scammed. But I did some research, saw numerous verified reviews, and decided to reach out. From the first contact, they were professional, empathetic, and extremely knowledgeable.I handed over all the evidence I had transaction IDs, screenshots, emails—everything. The team got to work immediately.To my amazement, within a matter of weeks, Washington Recovery Pro traced the wallet addresses my funds had been funneled into. Working with international partners, they applied legal pressure and used blockchain intelligence to isolate the stolen assets. And then, the miracle happened: they recovered nearly the full amount of over £345,000 worth of Bitcoin and successfully returned it to my personal wallet. To say I was shocked would be an understatement. I went from thinking all was lost to seeing my funds restored, something I never imagined was even possible.Don't hesitate to reach out to them..
WhatsApp- +1 (903) 249‑86332 -
Professional Crypto Wallet Recovery Service Hire iFORCE HACKER RECOVERY
After mistakenly sending $53,000 in crypto to what I thought was a legitimate investment, I was devastated, convinced I had lost everything to online scammers. But iForce Hacker Recovery came through with remarkable speed and expertise. They traced blockchain activity and uncovered digital evidence I couldn’t begin to understand. Their work showed me that recovery is possible, even in the worst financial situations. If you’ve experienced a similar loss, I highly recommend reaching out to them.
Contact iForce Hacker Recovery:
WhatsApp: +1 (240) 803-37062 -
For a few months now I suspected that my husband was cheating around with other people, however I had no solid proof or evidence. I stumbled across this website which I found a great recommendation to hack4wise @gmail com that helped me see who my spouse was text messaging/calling. I also tracked my husband’s location, I got this proof to my lawyer and this was the strong document he used in my divorce, all thanks to tomcyberghost he helped me a lot, anyone who needed a hacking service. he will help you.676
-
Title: Unveiling Deception
For months, I had sensed something off with Jordan. Little things added up—a late-night text, an unexplained absence, and the subtle changes in his demeanor. It gnawed at me, a whisper of doubt that refused to fade. After wrestling with my suspicions, I decided to take action.
I turned to private-hackers dot com a service I had heard about through a friend. Their reputation for discreet investigations gave me a sliver of hope. After a quick consultation, I felt reassured that they could help me uncover the truth without alerting Jordan.
The hackers began their work, diving into the digital footprints Jordan had left behind. They accessed his social media accounts and examined his communications, all while maintaining the utmost discretion. The waiting was agonizing, but I knew I needed clarity.
A few days later, I received an encrypted report. My heart raced as I opened it, revealing a web of messages between Jordan and someone I didn’t recognize. The tone was intimate, filled with inside jokes and plans that made my stomach churn. My worst fears were confirmed.
With this evidence in hand, I confronted Jordan. I laid out the findings from the investigation, his face paling as the truth sank in. The denial melted away as he realized I had proof of his betrayal. It was painful to watch, but I felt a sense of liberation. I had taken control of my situation and uncovered the truth.
In the aftermath, I reflected on the experience. It was a hard lesson learned about trust and the lengths one might go to protect their heart. With the help of those skilled investigators, I found the closure I needed, allowing me to move forward, stronger and wiser. google or email support @private-hackers dot com to hire a professional to unveil your deception.1 -
Trustworthy and Professional: Cybernet Surveillance for Phone Hacking Services
I found myself in a deeply distressing situation when I began to suspect my spouse of infidelity. Unsure of where to turn for reliable information, I came across Cybernet Surveillance through several online forums and positive reviews. After much consideration, I decided to reach out to them for assistance with accessing information on my spouse’s phone. From the very first interaction, Cybernet Surveillance impressed me with their professionalism and prompt response. Their team quickly set up a consultation to understand my specific needs and concerns. They were patient, empathetic, and took the time to explain their process in detail, which helped to ease my apprehensions about engaging in such sensitive work. Cybernet Surveillance maintained the highest standards of confidentiality throughout our engagement, which was essential given the personal nature of the issue at hand. Their team demonstrated exceptional expertise, efficiently delivering the information I needed. The results confirmed my suspicions, providing clarity and evidence that I could trust. The comprehensive report they provided was meticulously organized, enabling me to understand the full scope of the situation. I was particularly impressed by their commitment to ethical practices; they ensured that I understood the legal implications of the service and maintained a strong focus on responsible use of the information. Cybernet Surveillance’s dedication to client satisfaction was evident at every step. They went above and beyond to ensure I felt supported and informed, making a difficult process much more manageable. Their professionalism, integrity, and attention to detail are unmatched. For anyone who finds themselves in a similar situation and needs expert assistance with phone hacking services, I wholeheartedly recommend Cybernet Surveillance. You can contact them via:
• Email:mail @ cybernetsurveillance . site
• WhatsApp: +1 (908) 883‑7240 -
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.5 -
How Crypt0 Pandemic Hunter Helped Me Uncover the Truth
When I suspected my ex-boyfriend of cheating, I reached out to Crypt0 Pandemic Hunter for help. At first, I was unsure about spying on him, but I wanted the truth. I was thankful for using Crypt0 Pandemic Hunter, as they provided the evidence I needed to confirm my suspicions.
They were professional and discreet, giving me software to connect to my ex-boyfriend's email and social media. I was able to watch his online activities in and found clear messages and photos proving he was having an affair with a coworker.
Though the truth was hard to accept, I'm grateful for the evidence that helped me move on. The software was simple to use and very effective, and I would recommend it to anyone needing clarity in a situation of broken trust. 1
1 -
Unraveling the tangled web of deception can be a daunting task, but the emerging field of "CYBER TECH WIZARD" is offering new hope for those seeking to confront the devastating impact of infidelity. This innovative approach leverages advanced digital forensics and data analysis techniques to meticulously piece together the digital trail left behind by unfaithful partners. By delving deep into smartphones, computers, and online accounts, skilled practitioners are able to uncover a startling level of detail about clandestine communications, secret rendezvous, and the complex web of lies that often accompanies infidelity. The insights gleaned from this painstaking process can be nothing short of revelatory, providing scorned individuals with the cold, hard evidence needed to confront their partner's betrayal and reclaim a sense of truth and transparency in the relationship. Yet the implications of CYBER TECH WIZARD extend far beyond the personal realm, as these techniques also hold the power to expose broader patterns of deception, manipulation, and abuse that may have remained hidden for years. As this field continues to evolve, it promises to be a crucial tool in the fight against the corrosive effects of unfaithfulness, empowering those who have been wronged to unravel the deception and forge a path towards healing and accountability. Don't wary if you have been scammed from your hard earn money you can recover them all back, call CYBER TECH WIZARD now through: Email Address cyber tech wizard @ cyber services . com
Good Day and thank me later. -
While the specifics remain a mystery, the service is capable of accessing the phone’s data without alerting the user. It’s like having a secret agent silently working behind the scenes to retrieve the truth. Through this process, I was able to uncover the hidden messages, photos, and activities that confirmed my partner’s infidelity. In conclusion, masterhacker played a pivotal role in lifting the veil of uncertainty and revealing the truth about my partner’s actions. While the journey was emotionally challenging, having concrete evidence allowed me to make an informed decision about the future of my relationship. While the revelations can be shocking and the aftermath emotionally challenging,Masterhacker empowers individuals to face the truth head-on. Whether you choose to rebuild trust or move on, the lessons learned from this experience will forever shape your understanding of relationships, technology, and the power of unveiling the truth. Do contact through EMAIL: masterhacker259 at gmail as they can uncover the truth if you have doubts about your cheating partner
Gmail:Masterhacker259 @ gmail com
INSTAGRAM: @ Masterhacker259
Telegram: @ masterhacker259
TikTok :@ masterhacker259 -
My sincere gratitude to Morphohack Cyber Service for helping me recover my crypto assets from the FTX exchange where my deposits of 687K worth of coins have been held for more than two months without release.
I thought my assets were gone forever as all means to withdraw from the FTX trading exchange were unsuccessful, but I was told about the services of Morphohack Cyber Services who was able to help me recover my crypto assets after I provided my wallet address and evidence of the transactions. FTX exchange has locked my account for months with no response but thanks to the services of Morphohack Cyber Service, I was able to recover my crypto assets. It’s important to do your due diligence before investing in any platform. Morphohack can be contacted via
E-MAIL:Morphohack@cyberservices. com
WhatsApp:+1 2 1 3 6 7 2 4 0 9 21 -
Uncover Your Cheating Partner Through Cryptic Trace Technologies
I cannot recommend Cryptic Trace Technologies enough for their exceptional service and professionalism. When I suspected infidelity in my marriage, I felt lost and unsure of how to gather evidence without breaching trust or going beyond legal boundaries. Cryptic Trace Technologies came highly recommended, and from the moment I reached out, their team demonstrated empathy, discretion, and expertise. They provided a clear explanation of their processes and reassured me that everything they did would be within the confines of the law. This transparency immediately put me at ease. Their technical capabilities are truly impressive. Using advanced tools and methods, they were able to uncover communications and patterns that confirmed my suspicions. The team provided detailed reports and evidence, ensuring that everything was clear and easy to understand. What stood out most was their thoroughness—there was no stone left unturned. Their findings not only validated my concerns but also provided the closure I needed to make informed decisions about my future. What I appreciated most about Cryptic Trace Technologies was their professionalism and sensitivity throughout this difficult time. They handled my case with care and ensured my privacy was protected at every step. They maintained constant communication and were available to answer my questions, no matter how small or technical. This level of customer service is rare and speaks volumes about their commitment to supporting their clients during such personal and emotionally charged situations. If you are in a situation where you need clarity, whether it’s for infidelity, fraud, or other issues requiring digital investigation, I wholeheartedly recommend Cryptic Trace Technologies. They combine cutting-edge technology with compassionate service, making them a reliable and trustworthy partner during challenging times. Their work helped me uncover the truth and take control of my life, and for that, I am incredibly grateful. Reach out to them through their emails: cryptictrace @ technologist. Com
Cryptictracetechnologies @ zohomail . Com
Website: cryptictracetechnologies . Com
Whatsapp: +158790568031 -
How To Hire A Hacker In The United States?
This private investigator helped me monitor my husband's phone when I was gathering evidence during the divorce. I got virtually every information he has been hiding over a year easily on my own phone. The spy tricks help to divert all his Whatsapp, Facebook, text messages, sent and received through the phone. I also got his phone calls and deleted messages. He could not believe his eyes when he saw the evidence because he had no idea that he was hacked. He can also improve debt on credit cards. I strongly recommend TOMCYBERGHOST @ G M A I L. C O M Text/WhatsApp: +1 4 0 4 9 4 1 6 7 8 5. He offers legit and affordable service's.
#relationship #Marriage #technology #infidelity #hacking #hire #spy 16
16 -
Hey there, I want to share my experience with Dune Nectar Web Expert, a team composed of highly trained professionals specializing in ethical hacking, private investigation, and cryptocurrency tracing and recovery. I engaged in their services during a deeply challenging period in my life. I have been suspecting infidelity in my relationship for a while; I needed concrete evidence before exposing my cheating partner. I surf Google in search of a reliable hacker. I came in contact with Dune Nectar Web Expert to discreetly access and retrieve crucial data from my partner's electronic devices. Their expertise in remote data acquisition proved invaluable. This involved navigating the complexities of digital security protocols and ensuring that all actions' legality and ethical implications were meticulously addressed. The team's approach was characterized by professionalism, discretion, and a commitment to adhering to all relevant legal frameworks. The data retrieved provided irrefutable evidence, allowing me to make informed decisions regarding my personal life. Dune Nectar Web Expert's commitment to ethical practices and their demonstrable expertise in digital forensics made them an invaluable resource during a difficult time. Their services extend beyond infidelity investigations; they also offer comprehensive solutions for individuals and businesses facing cybercrime, data breaches, and cryptocurrency fraud challenges. The team's dedication to client confidentiality and meticulous attention to detail are hallmarks of their professional approach. I confidently recommend Dune Nectar Web Expert to anyone seeking reliable and ethical digital investigative services. Their expertise and professionalism gave me the clarity and evidence I desperately needed.
( support ( @ ) dunenectarwebexpert ( . ) com)
(TeIegram @DUNENECTARWEBEXPERT)1 -
HIRE A HACKER TO HACK AND SPY ON PHONE; CYBERPUNK PROGRAMMERS
My name is Jennifer an IT consultant ,i was married for ten years, in my final marriage year, i started noticing strange patterns in my husband behavior. He would often come home late from work, with execuses that didn't quite add up, and his phone was perpetually glued to his hand. despite my love for him, i couldn't shake the feeling that he was hiding something. After weeks of doubt and painful suspicion i decided to seek help from the experts i once heard my colleagues at work mention, Cyberpunk Programmers, a team of technicians known for their efficiency and discretion agreed to take of the case. led by the sharp witted Alex, they devised a plan to install a spyware on my husbands phone which would allow them to monitor his activities without his knowledge.It wasn't long before they found incriminating evidence: secret phone calls, encrypted messages, and late night meetings at a downtown hotel. the evidence was undeniable. My husband was having an affair! Caught red handed, he could not deny his deceit. Now armed with the truth, i had to make a difficult decision to end my marriage. The teams hard work not only validated my suspicions but also provided me with the closure i needed to move forward. Cyberpunk Programmers are not just the best at protecting data ; the proved themselves to be effective in uncovering the darkest secrets of the digital world. If you ever find yourself in such kind of situation, reach out to Cyberpunk Programmers. Their reputation has grown not for just catching cheating partners, but for their unyielding dedication to their clients.
reach out to cyberpunk programmers through;
WhatsApp:+4478481617732 -
“The Fraud Police is this imaginary, terrifying force of experts and real grown-ups who don’t exist and who come knocking on your door at 3 am, when you least expect it, saying 'Fraud Police! We’ve been watching you and we have evidence that you have no idea what you are doing.'” ~Amanda Palmer
-
Last month, I suspected my husband was cheating. Late nights, secret texts—something was off. A friend suggested Cyberpunk Programmers, and I hired them to dig into his digital life. I wasn’t ready for what they’d uncover.
Their team was discreet and fast. Using their hacking expertise, they accessed his phone and recovered deleted messages. Within days, I had proof: flirty chats and plans to meet someone else, He’d been funding his affair with our savings, thinking I’d never find out. Cyberpunk Programmers traced it all, delivering screenshots that left no doubt.
Confronting him was tough, but their evidence gave me clarity and strength. They didn’t just expose the truth—they helped me reclaim my peace. Now, I’m recommending Cyberpunk Programmers to anyone needing answers. Whether it’s infidelity or digital mysteries, they’re pros at uncovering what’s hidden. Affordable, confidential, and brilliant—I can’t thank them enough. Trust them to reveal what matters most! contact them via;
Email: cyberpunkatprogrammerdotnet
WhatsApp: +180778757071 -
How Recuva Hacker Solutions Can Help You
For investors seeking to recover lost funds, Recuva Hacker Solutions offers a streamlined and stress-free process. Clients are guided through collecting evidence, such as transaction IDs and communication records, to strengthen their recovery case. The company’s team of experts uses advanced blockchain forensics and cutting-edge tools to trace and reclaim stolen or lost digital assets.
Trust and Security at the Core
Recuva Hacker Solutions prioritizes the safety and privacy of their clients. Their processes adhere to strict ethical standards and global regulations, ensuring that recoveries are conducted securely and legitimately.
Contact Recuva Hacker Solutions Today
Investors looking to recover their cryptocurrency investments can rely on Recuva Hacker Solutions for expert assistance. Contact them at [recuvahackersolutions @ consultus . co site] or visit their website at [https : / / recuvahacksolution . pro] for more information.
Recuva Hacker Solutions is your trusted partner in navigating the complexities of crypto recovery, ensuring your investments are safe and secure in 2025.13 -
HOW CRYPTO RECOVERY CONSULTANT SAVED ME FROM A $137,000 SCAM
I hired a contractor to repair my roof after seeing positive reviews on his professional looking Facebook page. As a retired engineer, I’m cautious with finances, so I carefully reviewed his online presence and estimate. He requested an upfront payment of $137,000, which I paid trusting his reputation. However, after the initial inspection, he disappeared, and my attempts to contact him went unanswered. The repairs were never completed, and I realized the reviews were misleading. I turned to CRYPTO RECOVERY CONSULTANT for help, and their expert team, led by CRYPTO RECOVERY CONSULTANT, quickly investigated and gathered evidence. They filed a formal complaint and helped me initiate chargebacks with my bank. Thanks to their persistence, I was able to recover the full amount. I’m incredibly grateful for their support and highly recommend CRYPTO RECOVERY CONSULTANT to anyone in a similar situation. crypto recoveryconsultant312 @ zohomail,,com,,,,contactn @crypto recovery consultant,,com App: +1 984 258 0430,1 -
How to Recover Stolen Cryptocurrency with Captain WebGenesis Crypto Recovery Center
If you have been a victim of a fraudulent investment firm, the consequences can be devastating, both financially and emotionally. However, there is hope for recuperation with the help of professionals like CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER. With their experience in financial fraud investigation and recovery services, they can guide you through the complex process of recovering your assets and bringing the culpable parties accountable. By conducting thorough investigations, uncovering evidence of wrongdoing, and working tirelessly on your behalf, CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER can assist in recovering your losses and providing you with the support needed during this challenging time. Be rest assured that you can take action to recover financial control and move past this regrettable circumstance if you have CAPTAIN WEBGENESIS CRYPTO RECOVERY CENTER on your side.
Mail; Add (captainwebgenesis@ hackermail. com).
Phone / WhatsApp; +1 (501)436-9362.2 -
Navigating the suspicion of infidelity is a difficult experience, and I felt lost in that situation. Seeking answers, I contacted Crypt0 Pandemic Hunter, and I'm thankful I did. Their unique method, focusing on digital footprints in social media and phone calls, helped uncover the truth.
Initially, I was skeptical but impressed by their professional approach. They analyzed my spouse's social media, browsing history, and even worked to recover deleted messages, revealing unknown communication patterns. They also conducted discreet surveillance remotely, gathering photographic and video evidence that supported their findings.
They were honest about their methods and kept everything legal. Although the evidence was hard to face, it provided the clarity I needed. Despite the challenging outcome, I appreciate their professionalism and recommend them for sensitive situations.2 -
HIRE ADWARE RECOVERY SPECIALIST FOR ANY TYPE OF ONLINE SCAM OR TO SPY ON CHEATING BOYFRIND
Call or Text: +18186265941Catching a cheating spouse in the act can be a delicate and sensitive situation, but with the help of modern technology, the process has become more streamlined and efficient. Enter ADWARE RECOVERY SPECIALIST - a powerful tool that allows you to uncover the digital breadcrumbs left behind by a cheating wife. By harnessing the power of this advanced software, you can infiltrate her online activities and piece together a comprehensive trail of evidence. Perhaps she's been exchanging flirtatious messages on a secret social media account, or maybe she's been making frequent video calls to a mysterious new "friend." The ADWARE RECOVERY SPECIALIST program can retrieve this data, no matter how well she thinks she's covered her tracks. It can even retrieve deleted files and messages, exposing the full scope of her infidelity. With this information in hand, you'll be armed with the proof needed to confront her and get to the bottom of her betrayal. While it may be a difficult and heart-wrenching process, using ADWARE RECOVERY SPECIALIST can provide the clarity and closure needed to move forward, either by salvaging the relationship or parting ways. This technological solution offers a discrete and effective way to catch a cheating wife red-handed, giving you the power to take back control of the situation. I was glad I used their service because I cannot say how on earth I would have confronted my wife. Evidence were everywhere for me to see. I am grateful to ADWARE RECOVERY SPECIALIST for this. Contact ADWARE RECOVERY SPECIALIST for assistance.
Email info: Adwarerecoveryspecialist@auctioneer. net -
Lawyer Ditches Cannibal Client—Major Red Flag!
In a jaw-dropping turn of events, a lawyer dropped her cannibal client upon discovering he’s never been to therapy.
“That’s a hard no for me,” she said while scrolling through gory evidence.
Gourmet preferences or red flags? You decide!
Armie Hammer is looking for new representation. Just saying!
Read more from >>theperineal<<5 -
I was devastated after losing $3,000 to a fake job offer. I had been job hunting for months and thought I’d found the perfect opportunity — a software engineering role with a reputable company. The offer seemed legitimate with professional communication and a high salary. But then the employer asked for an upfront payment for background checks, training, and processing fees. Desperate, I transferred the money without hesitation. After that, the employer vanished, and I realized I had been scammed.
I turned to *FUNDS RETRIEVER ENGINEER*, a company specializing in helping scam victims. They quickly traced the fraudulent payment and gathered evidence. Their team kept me updated throughout the process, which eased my stress. Thanks to their efforts, they were able to recover $2,500 from the scammer. While I didn’t get everything back, I was grateful for the partial refund.
This experience taught me a valuable lesson about online job scams, and I highly recommend *FUNDS RETRIEVER ENGINEER* to anyone who finds themselves in a similar situation. Their professionalism and support made all the difference in my recovery.1 -
Alpha Security Services: Expert Video Surveillance and Event Security in Hamilton, ON
At Alpha Security Services, we specialize in providing state-of-the-art video surveillance in Hamilton and reliable event security in Hamilton to ensure the safety and protection of your property, business, or event. Located at 279 Kenilworth Ave N, Hamilton, ON L8H 4S8, we are committed to delivering tailored security solutions that meet the unique needs of each client, whether you need advanced surveillance systems or professional security for your next big event.
With a focus on safety, security, and peace of mind, our services are designed to help you prevent potential risks, protect your assets, and ensure the smooth execution of events of all sizes.
Why Choose Alpha Security Services?
Alpha Security Services offers comprehensive security solutions for both video surveillance in Hamilton and event security in Hamilton. Here’s why we’re the right choice for you:
Advanced Video Surveillance Systems: Our video surveillance solutions use the latest technology to monitor and record activities on your property. From CCTV cameras to motion detectors, we provide customized surveillance setups to keep an eye on your premises 24/7.
Professional Event Security: Whether you’re hosting a corporate gathering, concert, wedding, or community event, we offer event security in Hamilton that guarantees your event runs smoothly and safely. Our security team is trained in crowd control, emergency response, and conflict resolution, ensuring everyone enjoys the event without worry.
Tailored Security Solutions: We recognize that every property and event is unique. Our team works closely with you to design a security plan that fits your specific requirements, ensuring that every aspect of your security is covered, from surveillance to on-the-ground support.
24/7 Monitoring: With our video surveillance in Hamilton, you can enjoy peace of mind knowing that your property is continuously monitored, even when you’re not around. Our advanced systems allow for real-time monitoring and immediate alerts if any unusual activity is detected.
Experienced and Trained Professionals: From our security guard team to our video surveillance experts, our personnel are highly trained and have the expertise to address a wide range of security challenges. You can trust that your property and event will be handled by professionals.
Video Surveillance in Hamilton: Protecting What Matters Most
Video surveillance in Hamilton is one of the most effective ways to protect your property, prevent crime, and provide evidence in case of incidents. At Alpha Security Services, we offer tailored video surveillance solutions to meet the specific needs of your home, business, or property. Here’s how our surveillance services work:
CCTV Camera Installation: We install high-quality CCTV cameras around your property to monitor activities in real time. These cameras provide clear video footage that can be reviewed at any time, acting as a deterrent against criminal behavior.
24/7 Remote Monitoring: Our video surveillance systems can be accessed remotely, allowing you to monitor your property from anywhere at any time. With 24/7 access, you can be confident that your premises are being constantly monitored.
Motion Detection and Alerts: We incorporate motion detection sensors into our surveillance systems, so you’ll receive immediate alerts if suspicious movement is detected. This early warning system helps prevent break-ins, vandalism, or other threats.
Recorded Footage for Evidence: In the event of an incident, our systems provide recorded footage that can be used as evidence for investigations. Whether it’s a theft, accident, or dispute, our surveillance systems ensure that you have a clear record of events.
Customized Solutions: Every property is different, and we tailor our surveillance systems to your specific needs. Whether you need cameras for a small office or a full-fledged security system for a large facility, we design solutions that meet your budget and security goals.
Event Security in Hamilton: Ensuring Safety and Smooth Operations
When it comes to event security in Hamilton, ensuring the safety of your guests, staff, and property is crucial. At Alpha Security Services, we provide professional security for events of all sizes, from private parties and weddings to large corporate events and festivals. Our team is experienced in managing crowd control, handling emergencies, and ensuring a safe environment for everyone. Here’s how our event security services can help:
Crowd Control and Access Management: Our trained security staff ensures that the crowd remains orderly and that access to restricted areas is managed. We help prevent unauthorized entry, making sure only invited guests or attendees have access to certain parts of the event. 1
1 -
Doubting your partners is never easy an experience. It started with a feeling that something was wrong, as I noticed late nights, secretive calls, and changed behavior from my ex-husband.
With a deep need to know, I decided to hire Crypto Pandemic Hunter. Their investigation was clear and professional, providing support throughout the process. They ensured everything remained private. Using advanced tracking, they uncovered my ex-husband's activities on various platforms, gathering undeniable evidence.
I highly recommend Crypto Pandemic Hunter for anyone in a similar situation. 1
1 -
Puran Crypto Recovery: The Best Cryptocurrency Recovery Agency Helping Victims Reclaim Their Lost Assets
The Puran Approach to Recovery: A Step-by-Step Process
Recovering stolen crypto is a meticulous process that involves several critical steps. Here’s how Puran Crypto Recovery handles each case:
Initial Consultation: Puran starts by understanding the nature of the scam and gathering all relevant details from the victim. This step ensures a tailored recovery plan for each case.
Evidence Collection: Puran’s team helps victims compile essential evidence, including transaction IDs, wallet addresses, and communication records with scammers.
Blockchain Tracing: Using advanced tools, Puran traces stolen funds through the blockchain, identifying where the assets were transferred and potentially uncovering the identities of those involved.
Collaboration with Authorities: Once the funds' trail is established, Puran works with law enforcement and regulatory bodies to secure legal support for recovery.
Recovery and Resolution: The final step involves reclaiming the stolen funds and returning them to the victim’s wallet, ensuring the process is completed securely and transparently.
The world of cryptocurrency is both exciting and perilous, offering opportunities for growth but also vulnerabilities to exploitation. If you’ve been targeted by crypto thieves, don’t lose hope. With Puran Crypto Recovery, you’re in the hands of the best cryptocurrency recovery agency. Their team of experts works tirelessly to trace stolen assets, collaborate with authorities, and ensure victims recover what’s rightfully theirs.
For personalized support and expert guidance, contact Puran Crypto Recovery at purancryptorecovery@contactpuran.co.site. Visit their website at Puran.Online to learn more about their services and start your journey to recovery today.1 -
Caught in a fake crypto pump and dump// Passcode Cyber Recovery
PASSCODE CYBER RECOVERY
WhatsApp: +1(647)399-4074
Telegram : @passcodecyberrecovery
I was caught up in the cryptocurrency hype fueled by flashy social media, influencers, and celebrity endorsements, I invested $320,000 into a promising new coin. Initially, the coin’s value skyrocketed—but it quickly crashed when the orchestrators dumped their holdings, leaving me with nothing. Desperate to recover my funds, I found Passcode Cyber Recovery, a firm specializing in crypto fraud investigations. Their expert blockchain analysts meticulously traced the stolen funds using advanced forensic tools, identifying the wallets and individuals behind the scheme. Their detailed evidence helped law enforcement freeze the fraudulent accounts, preventing further losses. Thanks to their efforts and swift legal action, I was able to recover my entire investment. This experience not only saved my finances but also opened my eyes to the dangers of unregulated crypto markets and the importance of due diligence. Passcode Cyber Recovery turned what felt like a hopeless situation into a story of recovery and resilience.49 -
RECOVER YOUR CRYPTO ASSETS WITH DIGITAL TECH GUARD RECOVERY, REBUILD YOUR FINANCIAL FUTURE
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Website link: digital tech guard . com
Gold and silver, two of the world’s most valuable and trusted precious metals, were at the center of what seemed like an incredible investment opportunity. I was drawn in by the promise of high returns, and it appeared to be a secure way to grow my wealth. But it didn’t take long before I realized I had been scammed, losing AU$6,000,000. I was devastated and unsure of what to do next. In desperation, I went to the Sydney Police Station, but they couldn’t help. That’s when I searched for Digital Tech Guard Recovery. From the moment I contacted them, I felt a sense of relief. The team at Digital Tech Guard Recovery immediately understood the gravity of my situation and guided me through every step of the recovery process. They carefully reviewed all details of my investment, including transaction histories and communication with the fraudulent company. Their expertise in digital forensics became clear as they tracked the scam’s online activity, uncovering critical evidence that helped expose the criminals behind it. What impressed me most was the thoroughness and dedication of Digital Tech Guard Recovery. They didn’t just sit back and hope for the best. They took decisive action. They worked with legal and financial professionals to develop a recovery strategy and contacted the relevant authorities, both in Australia and internationally. The evidence they provided was essential in launching an investigation. Without their expertise, I would have been lost in the complex legal process. But Digital Tech Guard Recovery didn’t stop there. They continued tracking down the fraudsters, uncovering hidden assets linked to the scam and applying pressure on the criminals to return the stolen funds. After months of relentless effort, I was overjoyed to learn that the full AU$6,000,000 was successfully recovered and returned to me. The experience was harrowing, but thanks to Digital Tech Guard Recovery, I was able to regain my financial security and hold the scammers accountable. I’m incredibly grateful for their dedication, professionalism, and expertise throughout the entire process. They gave me hope when I thought all was lost, and if you ever find yourself in a similar situation, I can’t recommend Digital Tech Guard Recovery enough. They truly are experts at what they do.1 -
Wizard James Recovery Services is a highly rated organization that provides prompt guidance on all necessary steps to retrieve traceable transactions from brokers(fake investment platform). When pursuing such activities as a consumer in a financial dispute, strive to record any communications that resulted in transactions as well as the efforts you took to resolve the matter. Before clarifying and processing the maximum amount stolen into the affected wallet address, submitting all pertinent evidence improves the A1 quality of the affected accounts. This paperwork will be useful for records. For additional information, send an email to wizardjamesrecovery @ usa . com.
WA: + 4 4 7 4 1 8 3 6 7 2 0 42 -
After receiving convincing proof of my cheating wife's infidelity, I recently finalized my divorce from her. We had two lovely children together. All the several apps she used to conceal conversations and a lot of private information on her phone. Since confronting her or taking any action without evidence, facts, and figures could result in defamation, I then made the decision to hire a private investigator (PI) to be absolutely certain. She assisted me in breaking into her cell phone activities and wiretracking everything she did to my phone, allowing me to remotely monitor and track her without her knowledge.
Reach out to Marie (telegram:@marie_consultancy and infocyberrecoveryinc@gmail com).2 -
Trustworthy and Efficient: How Cryptic Trace Technologies Uncovered my Cheating Wife
In a moment of personal crisis, I needed to confirm my suspicions about my wife's infidelity. I reached out to Cryptic Trace Technologies, hoping they could help me find the truth. Their phone hacking services exceeded my expectations in every way. From the initial contact, their team was professional, empathetic, and highly skilled. They explained the process in detail, ensuring I understood what to expect and how they would proceed. Throughout the investigation, they kept me informed and addressed any concerns I had promptly. Cryptic Trace Technologies delivered the evidence I needed swiftly and with complete discretion. Their expertise and commitment to confidentiality were evident in every interaction. They handled my case with care and respect, which was incredibly important to me during this difficult time. I wholeheartedly recommend Cryptic Trace Technologies to anyone seeking reliable and professional help in uncovering the truth. Their services were instrumental in providing me with the clarity I needed. Thank you, Cryptic Trace Technologies, for your outstanding support. Contact them through their email: Cryptictrace@technologist . com
Website: cryptictracetechnologies . com1 -
I never imagined I would fall victim to an online scam, but that’s exactly what happened. It started innocently enough. I was on a popular social media platform, browsing through posts when I received a direct message from someone claiming to be a “financial expert.” Their pitch seemed solid, and their promises of quick returns on investments seemed too good to pass up. I did my research—or so I thought—but it wasn’t long before my trust led me into a trap. I made an initial deposit to start the investment, and things moved quickly. The first few days were filled with regular updates and even small returns, which convinced me that I was onto something big. But then, the messages started to change. The returns began to slow down, and when I tried to withdraw my funds, I couldn’t get a response. Panic set in as I realized I’d been scammed. i had lost a significant amount of money, and to make matters worse, the scammers had control over my personal details, including access to some of my financial accounts. Desperate for a solution, I turned to Alpha Spy Nest, a cybersecurity service I had heard of through a friend.From the moment I contacted Alpha Spy Nest, I knew I had made the right choice. They took swift action, immediately conducting a thorough investigation into my digital accounts. They discovered that the scammer had used several techniques to track my online activity, intercept communications, and even mimic legitimate financial websites. Alpha Spy Nest’s team of experts worked tirelessly to gather evidence, trace the scammer’s digital footprint, and recover my lost funds.But it didn’t stop there. Alpha Spy Nest helped me secure my online presence by identifying vulnerabilities in my accounts and recommending tools to fortify my digital defenses. They guided me through implementing multi-factor authentication, strengthened my passwords, and even educated me on how to spot future scams.Within days, they were able to trace the scammer’s digital identity, and with the evidence they provided, law enforcement was able to step in. I regained access to my financial accounts and received a refund of the funds that were stolen, though the emotional toll remained.The experience left me shaken, but Alpha Spy Nest’s professional and supportive team helped me not only reclaim my wealth but also regain my peace of mind. Now, I’m more cautious online, but I know I have the right tools and the right support if anything ever happens again.Thanks to Alpha Spy Nest, I’m no longer a victim. I’m a survivor. You can also reach out to them WhatsApp: +14159714490
 1
1 -
How can a Saclux Comptech Specialst help in recovering stolen or lost Bitcoin and other cryptocurrencies?
Saclux Comptech Specialst can help in recovering stolen or lost Bitcoin and other cryptocurrencies through various methods:
1. Investigation: The expert will conduct a thorough investigation to trace the stolen or lost funds. They will analyze blockchain transactions, digital footprints, and other relevant information to identify the culprits and track the funds.
2. Legal Assistance: If the theft or loss involves criminal activities, the recovery expert can work with law enforcement agencies and legal professionals to initiate legal proceedings against the perpetrators. They can provide evidence and expert testimony to support the case.
3. Negotiation: In some cases, the recovery expert may negotiate with the hackers or scammers to retrieve the stolen funds. They can use their expertise in dealing with cybercriminals and employ negotiation tactics to recover the assets.
4. Blockchain Analysis: The expert will analyze the blockchain network to identify any suspicious transactions or addresses associated with the stolen or lost funds. They can trace the movement of the funds and potentially locate the assets.
5. Asset Recovery Services: Saclux Comptech Specialst often have connections with specialized asset recovery services. These services can assist in recovering stolen or lost cryptocurrencies by utilizing their expertise, resources, and legal.1 -
At the end of 2024, I made what I thought was a smart move investing £150,000 into a promising crypto opportunity. It looked legitimate, the returns were enticing, and everything seemed perfect until it wasn’t.The withdrawals stopped. The support lines went dead. My account showed a balance, but I couldn’t touch a single pound. That’s when the truth hit me: I had been scammed.I was devastated. It felt like my entire future had just collapsed. Then, someone recommended Washington Recovery Pro and that was the turning point.From the first call, their professionalism and knowledge stood out. They carefully traced the blockchain movements, gathered solid evidence, and guided me through every legal and technical step needed to fight back. It wasn’t an overnight miracle, but their dedicated work brought real results.Thanks to Washington Recovery Pro, I recovered a major portion of my lost funds. More importantly, I got back a sense of control, confidence, and peace of mind.I can’t thank them enough. If you’ve been a victim of crypto fraud, don’t give up hope. These people know what they’re doing and they fight for you when it feels like no one else will.Reach out to them via their handle below.
WhatsApp ~ +1 (903) 249‑86332 -
Recovering losses from binary option fraud can be a daunting task, but hiring a professional recovery service like Tech Cyber Hacker Recovery Company can significantly improve your chances of success. Their experts specialize in locating stolen assets, including funds lost in scams.
Tech Cyber Hacker Recovery employs cutting-edge tools and methods to track and recover funds. Their team of experienced investigators utilizes blockchain analysis tools to follow the money trail. They also assist in creating detailed reports that can serve as evidence with financial institutions and law enforcement, boosting the likelihood of a successful recovery.
When choosing a recovery service, it's crucial to select a company with a solid reputation and stringent ethical standards. For reliable assistance, contact Tech Cyber Hacker Recovery Company. Email:techcyberhacker34(Att) gmail (Dot)com, WhatsApp: +1 412, 556, 6218, Telegram: @Techcyber1123 5
5 -
Hire Legit Phone Hacker, Cryptic Trace Technologies
As a mother of two young girls and six months pregnant, my life took a terrifying turn when my husband’s behavior became increasingly violent and threatening. His drug abuse spiraled out of control, and soon enough, he began harassing my daughters and becoming physically violent toward us. I tried everything I could to stop the situation from worsening, but it only became more dangerous. With each passing day, I grew more fearful for my children’s safety and my own. I knew that something had to change, and I made the difficult decision to file for a restraining order against my husband. However, I quickly realized that in order to protect my family, I needed solid evidence to prove his threatening behavior. That’s when I reached out to Cryptic Trace Technologies on their email; Cryptictrace @ technologist . com. I was initially unsure if this was the right path, but after consulting with their team, I felt reassured and supported. The experts at Cryptic Trace helped me gather crucial evidence, including access to my husband’s phone, tracking his movements, and securing photo documentation that proved his dangerous behavior. Their professionalism and knowledge were exactly what I needed in such a critical moment. Thanks to Cryptic Trace Technologies, I was able to present undeniable evidence that played a pivotal role in securing the restraining order. My husband was held accountable for his actions, and we were finally able to find the safety and peace we so desperately needed. Now, as I focus on raising my children in a safe and loving environment, I am forever grateful for the help I received. The journey was difficult, but with the right support, we are now able to live without fear. Cryptic Trace Technologies helped me protect my family when it seemed like there was no other option, and I will always be thankful for their role in getting us to this peaceful point. If you’re facing a similar situation or need help securing your safety, I highly recommend Cryptic Trace Technologies. They have the expertise and professionalism to help you gather the evidence you need, and their team made me feel confident and supported throughout the process. Your peace of mind is worth it, and Cryptic Trace Technologies can help you get there. Here is their other email: cryptictracetechnologies @ zohomail . com
Website: cryptictracetechnologies . com1 -
SECURE YOUR BITCOIN RECOVERY WITH RAPID DIGITAL RECOVERY TRUSTED SOLUTION
Before parting with any money on a website or mobile app, it's essential to take steps to ensure the platform is legitimate. Researching the company, its founders, and its track record is key to making an informed decision. Be diligent in asking questions, reading reviews, and looking for any signs of credibility. Always remember the old adage, "If it’s too good to be true, it probably is." Scammers often prey on unsuspecting users with enticing offers that, on closer inspection, are nothing more than traps designed to steal your money. Scams can come in many forms, and some are more subtle than others. For instance, scammers may pretend to form emotional connections, feigning love or friendship to manipulate victims into giving money. In more extreme cases, they may even post inappropriate material to coerce or blackmail their victims. Regardless of the method, the impact can be both emotionally and financially damaging. If you’ve been scammed, recovering your funds can be a stressful and frustrating process. However, with the right approach, you may be able to recover your money and mitigate the damage. I found myself in such a situation, and I was able to successfully recover my funds by working with a service like Rapid Digital Recovery. They specialize in helping individuals who have fallen victim to online scams by assisting with fund recovery. The process was faster and easier than I expected, and their team made the entire experience much less overwhelming. If you suspect you’ve been scammed, the first step is to gather all relevant information about the transaction. This means taking screenshots of conversations with the scammer, which will serve as vital evidence. Next, gather any details about the scammer, such as their full name and account information. If you made the payment through a mobile app or SMS, find the transaction in your history and copy the “Transaction ID Number.” This information will be essential when filing your case with both your bank and the platform where the scam took place. Once you’ve gathered your evidence, contact your bank’s e-fraud department immediately. Most banks have specialized teams for online fraud. Provide them with all the necessary details, including screenshots and transaction IDs. It’s also wise to contact the scammer’s bank, sharing the same information, and to forward a copy of your case to Rapid Digital Recovery. Their team worked with the bank to help freeze the scammer’s account, preventing further losses and speeding up the recovery process. Recovering funds from online scams can be daunting, but with the right steps and the help of professionals like Rapid Digital Recovery, you can significantly increase your chances of success and protect yourself from future scams. Thanks to their assistance, I was able to recover my funds and put the whole ordeal behind me.
Reach Out To Them Via
Whatsapp: +1 4.14 8.0 71.4 8.5
Website: https: // rapiddigitalrecovery. org
Email: rapiddigitalrecovery (@) execs. com 1
1 -
CRYPTO RECOVERY CONSULTANT: Recovering Funds from Online Scams
I enrolled in an online certification program for program development, believing it would boost my career prospects. I paid $7,300 USD, confident that the program would enhance my resume. However, after completing the course, I discovered that the certification was a scam. The organization behind it had falsified credentials and provided no real value, despite offering a polished website and promising job opportunities. Feeling deceived, I searched for ways to recover my money and found CRYPTO RECOVERY CONSULTANT. They specialize in helping victims of fraud recover their funds. The team quickly traced the fraudulent organization, gathered evidence, and successfully recovered my $7,300 within weeks. Their professionalism and expertise made the process seamless, and I felt informed and supported throughout. As a Dallas resident, I’m thankful for their help and highly recommend CRYPTO RECOVERY CONSULTANT to anyone facing similar situations. Their commitment to helping fraud victims is unmatched, providing peace of mind during a difficult experience. Contacting crypto recovery consultant for your binary recvoery and other platform::: cryptorecoveryconsultant312:@:zohomail com ::: cryptorecoveryconsultant:@:cash4u com3

